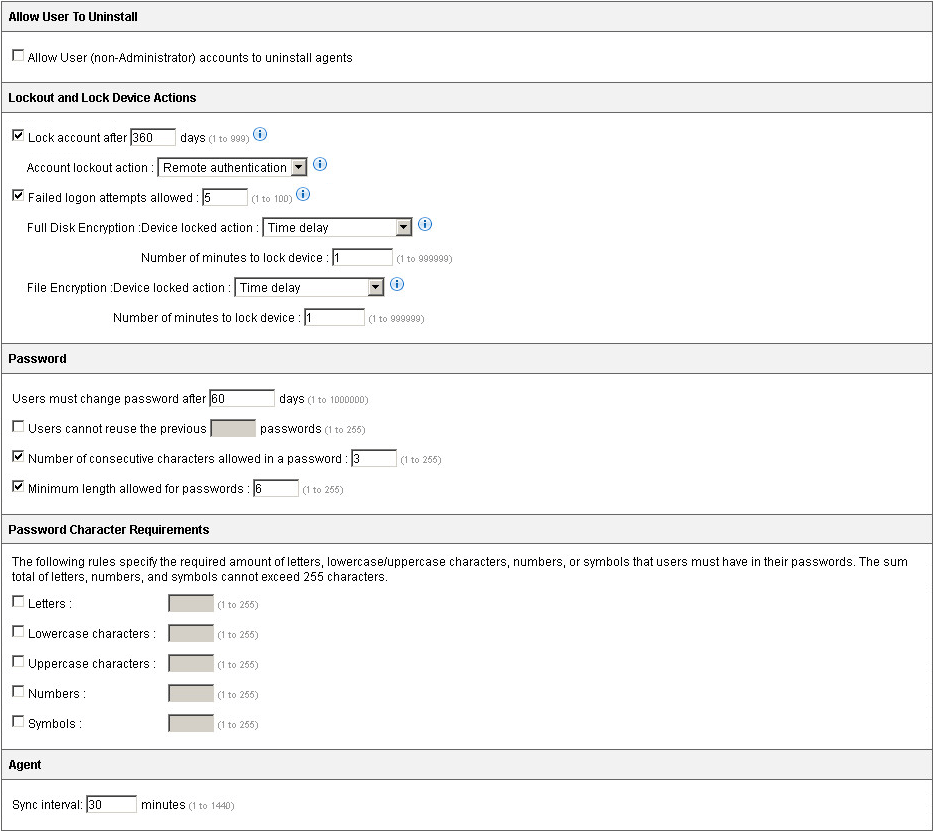
This section explains the configurable options for policy rules affecting all Endpoint Encryption devices.
Lockout Actions
Some policies have settings to lock out a user account or to lock a device based on certain criteria. Account lockout and device lockout actions affect the Endpoint Encryption device whether or not the agent synchronizes policies with PolicyServer. For example, if the Endpoint Encryption agent does not communicate with PolicyServer for a certain period of time, the Endpoint Encryption agent automatically locks the Endpoint Encryption device. Use the tables below to understand the actions available for the account lockout and device lock actions.
The following table describes when the lockout actions occur:
|
Type |
Description |
|---|---|
|
Account lockout |
Account lockout actions take effect when the Endpoint Encryption agent does not communicate with PolicyServer for a certain period of time as set by the policy. |
|
Full Disk Encryption device lockout |
Full Disk Encryption device lockout actions take effect when the Endpoint Encryption user exceeds the number of unsuccessful logon attempts to that Full Disk Encryption device as set by the policy. |
|
File Encryption device lockout |
File Encryption device lockout actions take effect when the Endpoint Encryption user exceeds the number of unsuccessful logon attempts to that File Encryption device as set by the policy. |
The options for lockout actions are as follows:
|
Action |
Description |
|---|---|
|
Erase |
PolicyServer erases all data controlled by the associated Endpoint Encryption agent. Warning:
The Endpoint Encryption user cannot recover the erased data. |
|
Remote authentication |
PolicyServer locks the Endpoint Encryption device until the Endpoint Encryption user contacts receives Remote Help authentication from an authenticator or from Support. See Remote Help. |
|
Time delay |
PolicyServer temporarily locks the Endpoint Encryption device and notifies the Endpoint Encryption user that the device is locked. The ability to authenticate or reset the password is disabled during the time delay. The duration of the time delay is determined by policy. Once the time delay has expired, the user is permitted to authenticate. |