The following procedure explains how to configure a Control Manager policy that affects Endpoint Encryption users and devices.
-
Set up your Endpoint Encryption users and
devices.
Endpoint Encryption user and device configuration uses the Endpoint Encryption Users and Endpoint Encryption Devices widgets. See Endpoint Encryption Users and Endpoint Encryption Devices respectively.
If your environment includes Active Directory, ensure that you have configured Active Directory and synchronized all users. See Active Directory Synchronization.
For a general description of authentication process, see Authentication Overview.
-
Go to the Create Policy screen.
- Go to Policies > Policy Management.
- From the Product drop-down list, select Endpoint Encryption.
- Click Create.
The Create Policy screen appears.
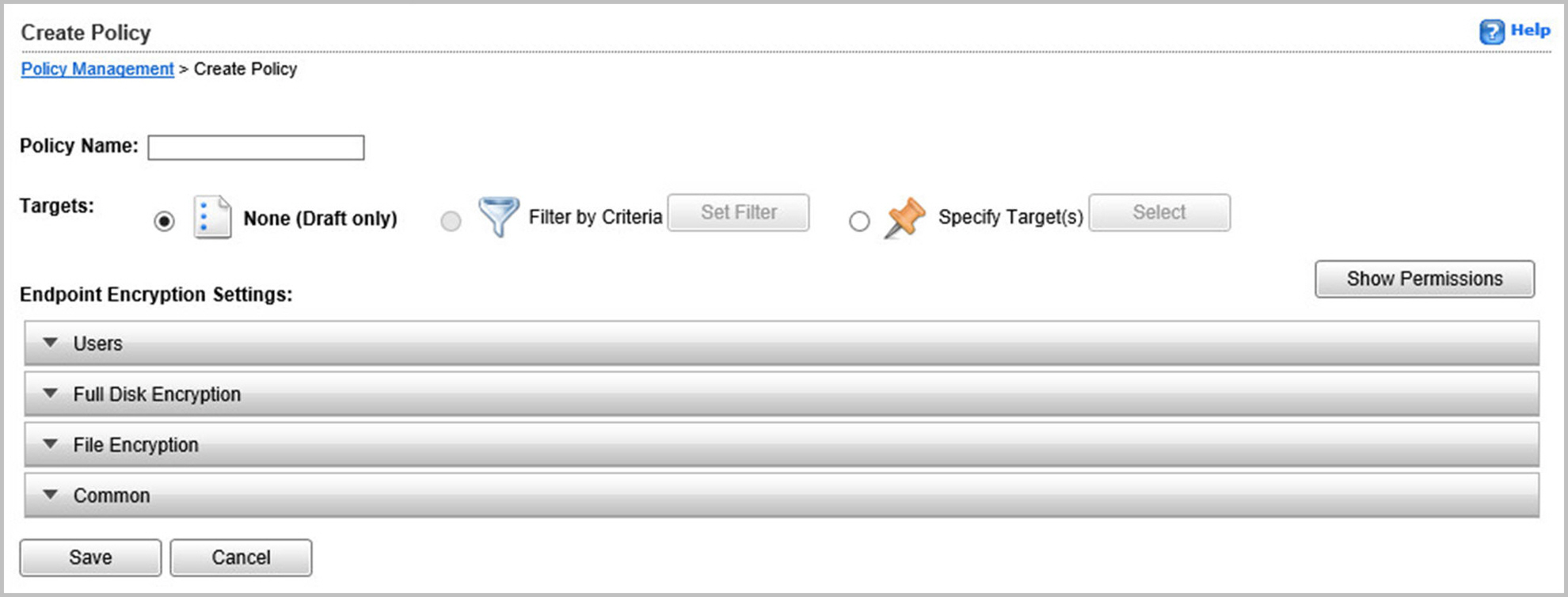
- Specify a policy name.
-
Select one of the following policy target options:
-
None (Draft Only): Create a policy with no targets (endpoints)
A policy with no targets may not be deployed. After creating a draft policy, edit the policy later to specify targets and deploy it to your environment.
-
Filter by Criteria: Endpoint Encryption does not support filtering by criteria
-
Specify Target(s): Specify existing endpoints.
Note:For more information about policy targets, see Specifying Policy Targets.
-
-
Specify Endpoint Encryption policy settings.
Endpoint Encryption settings are divided into the following rule sets:
Rule Set
Reference
Users
Full Disk Encryption
File Encryption
Common
- Click Save.


