The following procedure explains the configurable options for policy rules affecting File Encryption devices.
-
Create a new Endpoint Encryption policy.
See Creating a Policy.
-
Click File Encryption.
The File Encryption policy rules settings appear.
Figure 1. File Encryption Policy Rules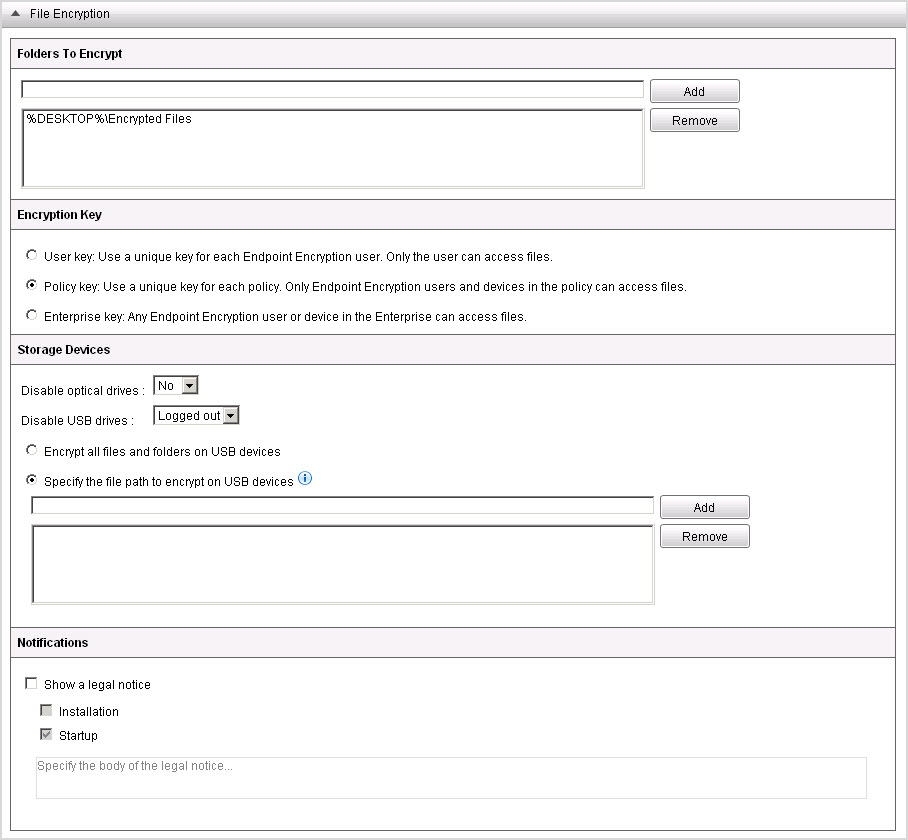
- Under Folder to Encrypt, specify folders that are automatically created and encrypted on the endpoint when the File Encryption agent synchronized policies.
-
Under Encryption Key, select the encryption for the
File Encryption encrypted folder.
-
User key: Use a unique key for each Endpoint Encryption user. Only the Endpoint Encryption user can decrypt files that he or she encrypted.
-
Policy key: Use a unique key for each policy. Only Endpoint Encryption users and devices in the policy can decrypt files.
-
Enterprise key: Any Endpoint Encryption user or device in the Enterprise can decrypt the files.
Note:Selecting Policy key or Enterprise key controls the sharing for the File Encryption shared key. For more information, see File Encryption Actions.
-
-
Under Storage Devices, configure the following
options:
-
Select Disable optical drives to control whether removable media is accessible from the endpoint.
-
Select Disable USB drives to control when the USB ports are disabled. Options are:
-
Always
-
Logged out
-
Never
-
-
Select Encrypt all files and folders on USB devices to automatically encrypt all the files and folders on removable drives when plugged into the endpoint.
-
Select Specify the file path to encrypt on USB devices to add or remove encrypted folders to USB drives. If a folder does not exist, it is created. If no drive letter is specified, all USB devices are affected.
-
- Under Notifications, select Show a legal notice to show the specific legal message at start up or only after installing the File Encryption agent.


