Server & Workload Protection components communicate over your network. They
use:
Before deployment, your network administrator might need to configure firewalls, AWS
security groups, and web proxies to allow those network services.
For a list of the firewall exceptions, see Firewall exception requirements for Trend Vision One. Firewall exception requirements differ depending on your environment. Refer to the
appropriate region to ensure you configure the correct allow rules.
NoteDefault settings are shown. Many network settings are configurable. For example, if
your
network has a web proxy, you could configure agents to connect
through it on port 1443, instead of directly to Server & Workload Protection on port 443. If you change the
default settings, then firewalls must allow communications via the
new settings instead.
|
For a basic overview, see the network diagram below. For details, see the required port
numbers, IP addresses, and URLs tables after the diagram.
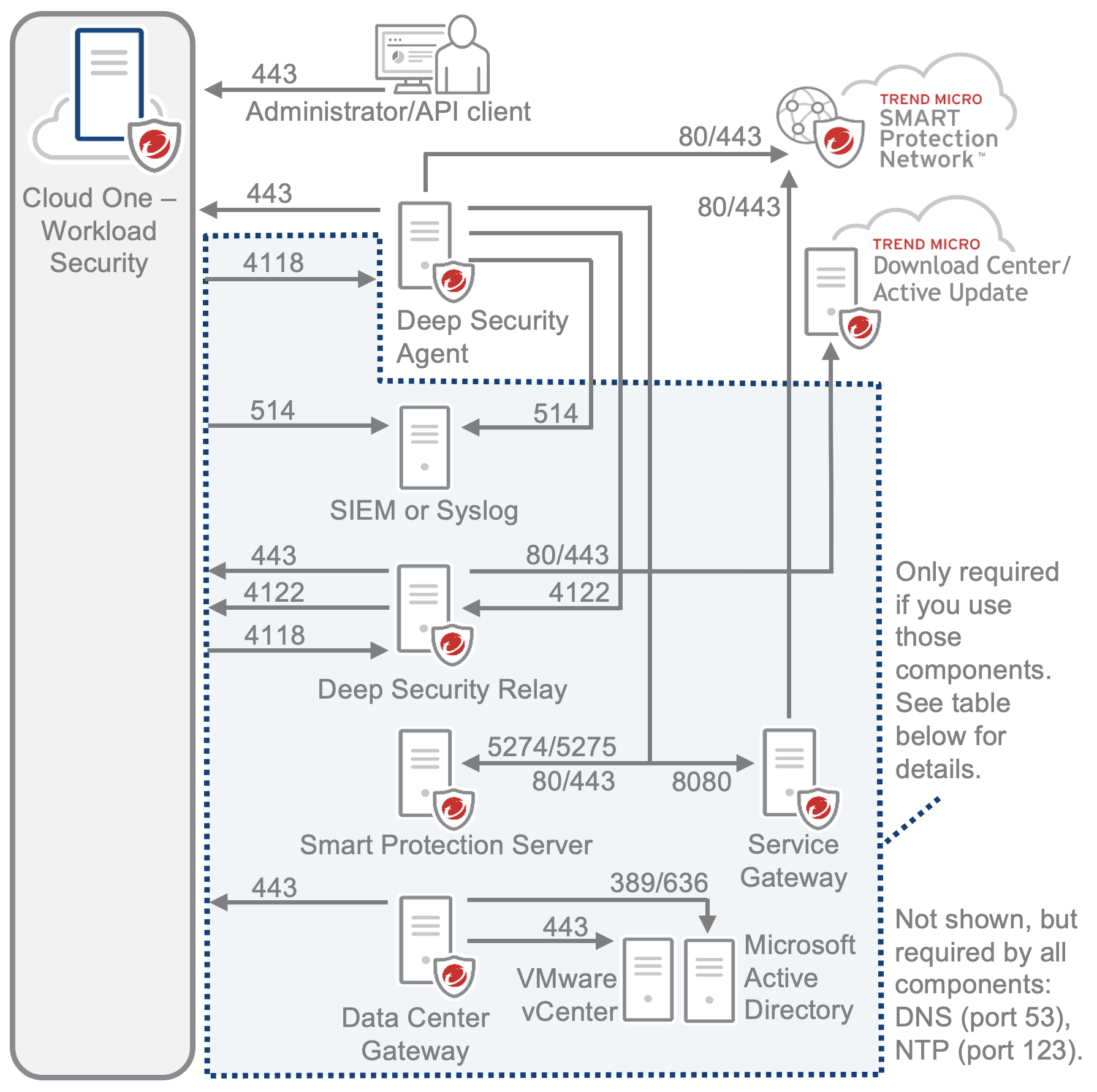
Required Server & Workload Protection IP addresses and port numbers
The table below is organized by source address (the deployment component which starts
the TCP connection or UDP session). Replies (packets in the same connection but
opposite direction, from the destination address) usually must be allowed, too.
Server & Workload Protection servers usually have dynamic IP addresses (that
is, other computers in your deployment use DNS queries to find the current IP
address of a Server & Workload Protection FQDN when required). For
the list of Server & Workload Protection domain names, see Required Server & Workload Protection URLs.
Some ports are required only if you use specific components and features. Some
services might have static IP addresses. These exceptions and optional features
are
indicated.
NoteAll ports in the table are destination ports (also called listening ports). Like
many software, Server & Workload Protection also uses a range of
dynamic, ephemeral source
ports when opening a socket. Rarely, ephemeral source
ports might be blocked, which causes connectivity issues. If that happens, then you must also open the
source ports.
|
|
Source Address
|
Destination Address
|
Port (Default)
|
Protocol
|
|
|
Administrator's computer
|
DNS server
|
53
|
DNS over UDP
|
|
|
NTP server
|
123
|
NTP over UDP
|
||
|
Server & Workload Protection
|
443
|
HTTPS over TCP
|
||
|
Server & Workload Protection
Subnets:
|
514
|
Syslog over UDP
|
||
|
6514
|
Syslog over TLS
|
|||
|
Agents,
|
4118
|
HTTPS over TCP
|
||
|
Agents
|
DNS server
|
53
|
DNS over UDP
|
|
|
NTP server
|
123
|
NTP over UDP
|
||
|
514
|
Syslog over UDP
|
|||
|
Server & Workload Protection
|
443
|
HTTPS over TCP
|
||
|
4122
|
HTTPS over TCP
|
|||
|
Smart Protection Network
|
80
|
HTTP over TCP
|
||
|
443
|
HTTPS over TCP
|
|||
|
8080
|
HTTP over TCP
|
|||
|
80
|
HTTP over TCP
|
|||
|
443
|
HTTPS over TCP
|
|||
|
5274
|
HTTP over TCP
|
|||
|
5275
|
HTTPS over TCP
|
|||
|
All destination addresses, ports, and protocols
required by agents (each relay contains an
agent)
|
||||
|
4122
|
HTTPS over TCP
|
|||
|
Localhost
(on relays, its agent connects locally, not to a remote
relay)
Only configure if the server's other software uses the same port
(a port conflict), or if host firewalls such as iptables
or Windows Firewall block localhost connections (server
connecting internally to itself). Network firewalls do
not need to allow this port because localhost
connections do not reach the network.
|
4123
|
N/A
|
||
|
80
|
HTTP over TCP
|
|||
|
443
|
HTTPS over TCP
|
|||
|
Download Center, or its mirror on a local web server(if any)
Accounts
created before 2020-11-23:
|
443
|
HTTPS over TCP
|
||
|
DNS server
|
53
|
DNS over UDP
|
||
|
NTP server
|
123
|
NTP over UDP
|
||
|
Server & Workload Protection
|
443
|
HTTPS over TCP
|
||
|
VMware vCenter
|
443
|
HTTPS over TCP
|
||
|
Microsoft Active Directory
|
389
|
STARTTLS and LDAP over TCP and UDP
|
||
|
636
|
LDAPS over TCP and UDP
|
|||
|
DNS server
|
53
|
DNS over UDP
|
||
|
NTP server
|
123
|
NTP over UDP
|
||
|
Trend Micro Smart Protection Network(for File
Reputation feature)
|
80
|
HTTP over TCP
|
||
|
443
|
HTTPS over TCP
|
|||
|
Server & Workload Protection
|
443
|
HTTPS over TCP
|
||

