SAML is supported for sign-on and access to the Workload Security service and not
to the overall Trend Cloud One product.
SAML is supported for the following regions:
-
US:
https://app.deepsecurity.trendmicro.com -
India:
https://workload.in-1.cloudone.trendmicro.com -
UK:
https://workload.gb-1.cloudone.trendmicro.com -
Japan:
https://workload.jp-1.cloudone.trendmicro.com -
Germany:
https://workload.de-1.cloudone.trendmicro.com -
Australia:
https://workload.au-1.cloudone.trendmicro.com -
Canada:
https://workload.ca-1.cloudone.trendmicro.com -
Singapore:
https://workload.sg-1.cloudone.trendmicro.com
Currently, Workload Security supports only the HTTP POST binding of the SAML 2.0 identity
provider (IdP)-initiated login flow, and not the service provider (SP)-initiated login
flow.
For information on how to configure SAML SSO with Microsoft Entra ID to work with
Trend Cloud One, see the Azure Microsoft Entra ID setup guide.
For a detailed explanation of how Workload Security implements the SAML standard,
see About SAML single sign-on (SSO).
For instructions on configuring it with other identity providers, see Configure SAML single sign-on.
Administrators involved in the process
Typically, there are two types of administrators required to configure Workload Security
to use Microsoft Entra ID for SAML single sign-on (SSO): a Workload Security administrator
and a Microsoft Entra ID administrator.
The Workload Security administrator must be assigned a Workload Security role with
the SAML Identity Providers right set to either Full or to Custom with Can Create New SAML Identity Providers enabled.
The following table lists the steps required to set up SAML single sign-on with Workload
Security using Microsoft Entra ID, and the person who performs each step:
|
Step
|
Performed by
|
|
Workload Security administrator
|
|
|
Microsoft Entra ID administrator
|
|
|
Workload Security administrator
|
|
|
Microsoft Entra ID administrator
|
Download Workload Security service provider SAML metadata document
In the Workload Security console, go to and click Download. The file is downloaded as
ServiceProviderMetadata.xml. Send the file to your Microsoft Entra ID administrator.Configure Microsoft Entra ID
The following steps are performed by a Microsoft Entra ID administrator. For details,
see Configure single sign-on to non-gallery applications in Microsoft Entra ID.
-
In the portal, add a new non-gallery application.
-
Configure single sign-on for the application. Trend Micro recommends that you upload the metadata file,
ServiceProviderMetadata.xml, that was downloaded from Workload Security. Alternatively, you can enter a reply URL (the Workload Security URL +/saml).The Workload Security URL depends on your Trend Cloud One region:-
US:
https://app.deepsecurity.trendmicro.com -
India:
https://workload.in-1.cloudone.trendmicro.com -
UK:
https://workload.gb-1.cloudone.trendmicro.com -
Japan:
https://workload.jp-1.cloudone.trendmicro.com -
Germany:
https://workload.de-1.cloudone.trendmicro.com -
Australia:
https://workload.au-1.cloudone.trendmicro.com -
Canada:
https://workload.ca-1.cloudone.trendmicro.com -
Singapore:
https://workload.sg-1.cloudone.trendmicro.com
-
-
Configure SAML claims. Workload Security requires the following:
-
https://deepsecurity.trendmicro.com/SAML/Attributes/RoleSessionName- This is a unique user ID that is the username in Workload Security. For example, you could use the User Principal Name (UPN). -
https://deepsecurity.trendmicro.com/SAML/Attributes/Role- The format is “IDP URN,Role URN”. The IDP has not been created in Workload Security yet, so you can configure this SAML claim later, in Define a role in Microsoft Entra ID.
You can also configure other optional claims, as described in SAML claims structure.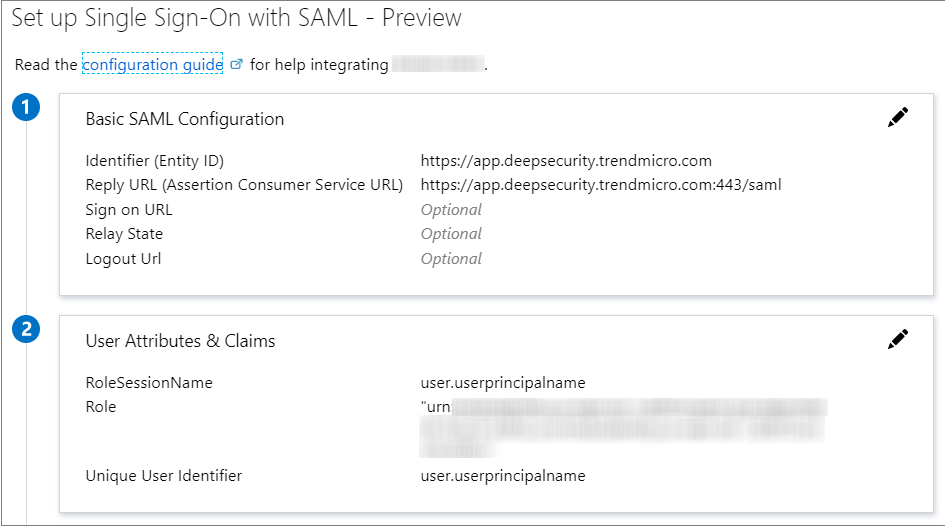
-
-
Download the Federation Metadata XML file and send it to the Workload Security administrator.
If there are multiple roles defined in Workload Security, repeat these steps to create
a separate application for each role.
Configure SAML in Workload Security
You need to perform a number of steps to configure SAML in Workload Security.
Import the Microsoft Entra ID metadata document
-
In Workload Security, go to .
-
Click Get Started or New.
-
Click Choose File, select the Federation Metadata XML file that was downloaded from Microsoft Entra ID and click Next.
-
Enter a Name for the identity provider, and then click Finish to transition to the Roles page.
Create Workload Security roles for SAML users
Make sure the page in Workload Security contains appropriate roles for your organization. Users
should be assigned a role that limits their activities to only those necessary for
the completion of their duties. For information on how to create roles, see Define roles for users. Each Workload Security role requires a corresponding Microsoft Entra ID application.
Get URNs
Your Microsoft Entra ID administrator requires identity provider URNs and role URNS
(URNs for the Workload Security for roles to associate with the Microsoft Entra ID
application). The required information for both can be found in the Workload Security
console:
-
To view identity provider URNs, go to and check the URN column.
-
To view role URNs, go to and check the URN column.
If you have multiple roles, you need the URN for each role, because each one requires
a separate Microsoft Entra ID application.
Define a role in Microsoft Entra ID
The following steps must be performed by an Microsoft Entra ID administrator.
In Microsoft Entra ID, use the identity provider URN and role URN identified in the
previous section to define the role attribute in the Azure application. This must
be in the format “IDP URN,Role URN”. See "Workload Security user role (required)"
in the SAML claims structure section.
Use the Validate button in Microsoft Entra ID to test the setup, or assign the new
application to a user and test that it works.
Service and identity provider settings
You can set how far in advance Workload Security alerts you to the expiry date of
the server and identity provider certificates, as well as how much time must pass
before inactive user accounts added through SAML single sign-on are automatically
deleted.
To change these settings, go to .
SAML claims structure
The following SAML claims are supported by Workload Security:
Workload Security username (required)
The claim must have a SAML assertion that contains an
Attribute element with a Name attribute of https://deepsecurity.trendmicro.com/SAML/Attributes/RoleSessionName and a single AttributeValue element. Workload Security will use the AttributeValue as the Workload Security username.Sample SAML data (abbreviated):
<samlp:Response xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol">
<Assertion xmlns="urn:oasis:names:tc:SAML:2.0:assertion">
<AttributeStatement>
<Attribute Name="https://deepsecurity.trendmicro.com/SAML/Attributes/RoleSessionName">
<AttributeValue>alice</AttributeValue>
</Attribute>
</AttributeStatement>
</Assertion>
</samlp:Response>
Workload Security user role (required)
The claim must have a SAML assertion that contains an
Attribute element with a Name attribute of https://deepsecurity.trendmicro.com/SAML/Attributes/Role and between one and ten AttributeValue elements. Workload Security uses the attribute values to determine the tenant, identity
provider, and role of the user. A single assertion may contain roles from multiple
tenants.Sample SAML data (abbreviated):
<samlp:Response xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol">
<Assertion xmlns="urn:oasis:names:tc:SAML:2.0:assertion">
<AttributeStatement>
<Attribute Name="https://deepsecurity.trendmicro.com/SAML/Attributes/Role">
<AttributeValue>urn:tmds:identity:[pod ID]:[tenant ID]:saml-provider/[IDP name],
urn:tmds:identity:[pod ID]:[tenant ID]:role/[role name]</AttributeValue>
</Attribute>
</AttributeStatement>
</Assertion>
</samlp:Response>
The line break in the
AttributeValue element is present for readability; in the claim, it must be on a single line.Maximum session duration (optional)
If the claim has a SAML assertion that contains an
Attribute element with a Name attribute of https://deepsecurity.trendmicro.com/SAML/Attributes/SessionDuration and an integer-valued AttributeValue element, the session will automatically terminate when that amount of time (in seconds)
has elapsed.Sample SAML data (abbreviated):
<samlp:Response xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol">
<Assertion xmlns="urn:oasis:names:tc:SAML:2.0:assertion">
<AttributeStatement>
<Attribute Name="https://deepsecurity.trendmicro.com/SAML/Attributes/SessionDuration">
<AttributeValue>28800</AttributeValue>
</Attribute>
</AttributeStatement>
</Assertion>
</samlp:Response>
Preferred language (optional)
If the claim has a SAML assertion that contains an
Attribute element with the Name attribute of https://deepsecurity.trendmicro.com/SAML/attributes/PreferredLanguage and a string-valued AttributeValue element that is equal to one of the supported languages, Workload Security uses the
value to set the user's preferred language.The following languages are supported:
-
en-US(US English) -
ja-JP(Japanese) -
zh-CN(Simplified Chinese)
Sample SAML data (abbreviated):
<samlp:Response xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol">
<Assertion xmlns="urn:oasis:names:tc:SAML:2.0:assertion">
<AttributeStatement>
<Attribute Name="https://deepsecurity.trendmicro.com/SAML/Attributes/PreferredLanguage">
<AttributeValue>en-US</AttributeValue>
</Attribute>
</AttributeStatement>
</Assertion>
</samlp:Response>


