Centralize management of TrendAI Vision One™ Endpoint Security agent settings for Endpoint Sensor and protection manager features.
Important
|
Endpoint security policies are a tool you can use to centrally manage endpoint settings
for your connected TrendAI Vision One™ Endpoint Security agent, including agents with Standard Endpoint Protection and Server & Workload Protection
installed.
Endpoint security policies modularize features and the component pieces of policies,
enabling settings and policies to be reused across your security environment.
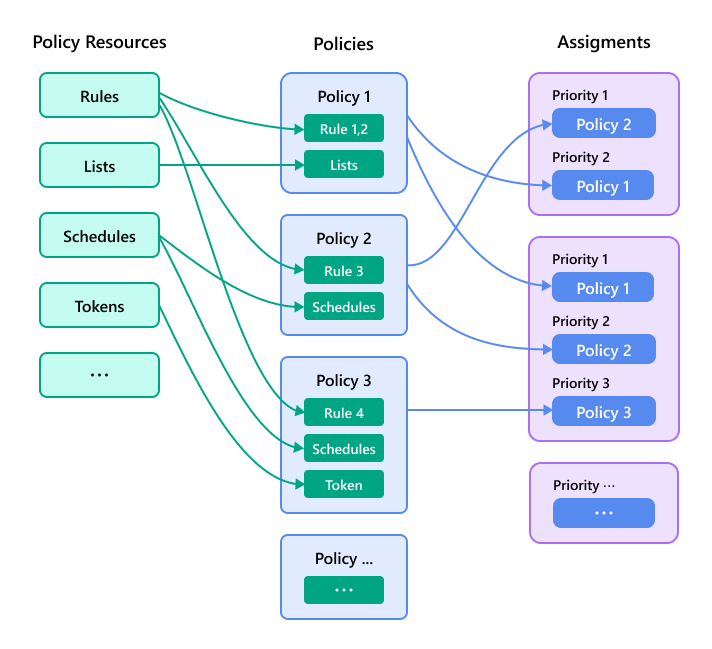
To create and assign settings across your endpoints, use the following steps:
-
Configure policy resources.Policy resources include rules, lists, and schedules for use with configuring security modules in your policies. You can also use policy resources to generate authorization tokens for terminating the agent program on an endpoint.
-
Configure the policy.Create policies and configure the security modules to protect and monitor your security environment.
-
Create policy assignments.Assignments use priorities and criteria to assign policies to targeted endpoints within selected endpoint groups. An assignment can include endpoint groups from both Standard Endpoint Protection and Server & Workload Protection.
Endpoint security policies feature a wide range of security modules you can configure.
Endpoint security policy modules
|
Category
|
Module name
|
Description
|
|
Threat Prevention
|
Actively protects endpoints by detecting and eliminating threats in real time
Use this module to set your Anti-Malware monitoring level, scheduled scans, and scan
exclusions.
|
|
|
Protects against web threats by blocking access to malicious URLs
Use this module to set your Web Reputation scan settings, access rules, and port monitoring.
|
||
|
Protects your endpoints from known and zero-day vulnerability attacks
Use this module to configure rule statuses and recommendation settings.
|
||
|
Hardening Rules
|
Provides protection by regulating programs that trigger certain events in commonly
targeted system areas
Support for configuring Hardening Rules is coming soon.
|
|
|
Access Control
|
Monitors endpoints for software changes and allows or blocks software actions based
on configured settings and rules
Use this module to enable or disable Application Control rules. You can also enforce
lockdown mode with Application Control.
|
|
|
Regulates access to external storage devices when connected to your endpoints
Use this module to configure device permissions and to specify allowed devices
|
||
|
Provides bidirectional stateful inspection of incoming and outgoing network traffic
Use this module to configure the firewall security level, enabled rules, and specify
allowed programs.
|
||
|
Advanced Capabilities
|
Log Inspection
|
Helps identify important events within your operating system and application logs
Support for configuring Log Inspection is coming soon.
|
|
Integrity Monitoring
|
Scans for unexpected changes to registry values, keys, services, processes, installed
software, ports, and files on endpoints
Support for configuring Integrity Monitoring is coming soon.
|
|
|
Cyber Risk & Security Operations
|
Analyzes endpoints for potential security posture weaknesses and performs vulnerability
assessments
Use this module to enable or disable Advanced Risk Telemetry
|
|
|
Sends activity data for state-of-the-art threat detection and alerting
Previously called Endpoint sensor detection and response, use this module to configure
the Endpoint Sensor monitoring level and deepfake detector.
|
||
|
Sends activity data to trace the movement of sensitive data within the Data Security
module
|
||
|
Identity Security Sensor
|
Monitors your identity management solutions to ensure robust and effective identity
security
Support for configuring Identity Security Sensor is coming soon.
|
|
|
Allows agents to automatically submit suspicious objects for analysis in a secure,
virtual cloud sandbox environment
When enabled, you can view analysis results in Sandbox Analysis.
|
||
|
Management Settings
|
Manage exceptions across endpoint protection features
Use this module to manage rule exceptions and configure the trusted programs list.
|
|
|
Deploy the TrendAI™ Toolbar for Enterprise browser extension to provide additional visibility and enhanced
monitoring capabilities for endpoint protection features
Browser extension helps enhance monitoring and detection for Web Reputation, Suspicious
Objects, and Data Security.
|
||
|
Provides a user interface on the endpoint for users to interact with the TrendAI Vision One™ Endpoint Security agent
Use this module to configure endpoint user permissions to interact with the agent,
perform manual scans, receive notifications, and terminate the agent program.
|


