Manage rule, lists, and other settings to use with your policies.
Policy Resources provides a central location to create, manage, and configure settings
that are reusable across your Endpoint Security Policies. Policy Resources includes
rules, lists, schedules, and authorization tokens. There are several actions you can
take depending on the resource type.
NoteSome actions are not available for every resource. Authorization tokens have a different
set of actions. For more information, see Authorization tokens.
TrendAI™ provides pre-defined lists for some resource types. Pre-defined lists cannot be modified or deleted.
|
Common resource actions
|
Action
|
Description
|
||
|
Add a resource
|
Click the add button to create a new rule, list, or schedule.  |
||
|
Find a resource
|
Use the search to find a rule, list, or schedule. Some resources also have filter
options.  |
||
|
Edit a resource
|
Click the name and edit the details under General.  |
||
|
View which policies use a resource
|
Click the rule name and click Policies or Policies and resources to view a list of policies or other resources that use the rule, list, or schedule.  |
||
|
Duplicate a resource
|
Select a resource and click Duplicate.
In the Duplicate window, specify a unique name for the new resource and click Duplicate. 
|
||
|
Delete a resource
|
Select one or more rules, lists, or schedules and click Delete. 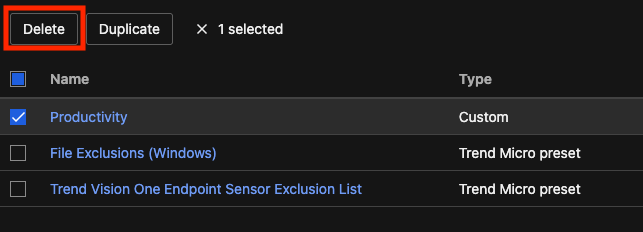 In the Delete window, review the selection and click Delete. You can remove a selected resource using the remove icon ( 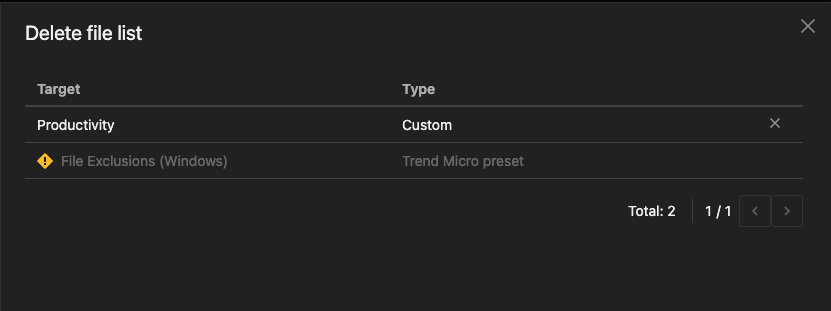
|


