了解如何在無法使用堆疊範本時將您的 AWS 帳戶連接到 Cloud Accounts。
有些 AWS 帳戶不允許使用堆疊範本在雲端環境中部署資源。這通常是由於安全政策阻止自動建立堆疊範本中部署程式檔所需的 IAM 政策和角色。
若要手動連接 AWS 帳戶,請利用 自動化中心上的 API 資源。使用此方法進行部署可啟用以下功能和權限:
-
Core Features and Cyber Risk Exposure Management:連接您的 AWS 帳戶所需的核心功能和必要的權限。
-
「Container Protection for Amazon ECS」(選用):此功能集允許 Container Security 連接並部署元件到您的 AWS 帳戶,以保護您在 Elastic Container Service (ECS) 環境中的容器和容器映像。
重要
|
步驟 1:生成並下載堆疊範本
從 Trend Vision One 主控台生成堆疊範本或透過調用 API 生成。
步驟
- 生成並下載堆疊範本:
-
存取Trend Vision One主控台並建立範本。
-
在 Trend Vision One 主控台上,移至
-
點擊「新增帳號」。
-
在「Deployment Type」畫面上,選擇「CloudFormation」和「Single AWS Account」。
-
按「下一步」。
-
指定「帳號」、「說明」,並選擇 AWS 部署區域。
-
如果您有多個伺服器與工作負載保護管理員實例,請選擇要與連接的帳戶關聯的實例,然後點擊「下一步」。
-
請點選「下一步」而不需設定「Features and Permissions」畫面。
-
點擊「Download and Review Template」。

注意
「帳號」 和 「說明」 欄位不會匯出到審核範本中。您可以在呼叫 「Add AWS account」 API 時提供這些參數。 -
-
調用 API 以獲取範本。
-
在自動化中心找到「Generate AWS CloudFormation template」 API。
-
找出
query_params字串。 -
對於
awsRegion,請提供您想要部署堆疊模板和核心功能的 AWS 區域。預設區域是根據您的 Trend Vision One 區域。 -
對於
features和featureAwsREgions,請將參數留空。 -
儲存您的變更並呼叫 API。API 回傳以下內容:
-
templateUrl:下載範本的 URL。 -
visionOneOidcProviderUrl:部署範本所需的參數。 -
createStackUrl:指向 Trend Vision One 的 CloudFormation 範本的 AWS CloudFormation 主控台 URL。
-
-
下載範本。
-
-
步驟 2:新增 Trend Vision One 作為身份提供者
在 AWS 控制台中使用 Identity and Access Management (IAM) 服務,授予 Trend Vision One 存取您 AWS 帳戶的權限。
- 存取 AWS 主控台
- 將 Trend Vision One 新增為身份提供者。
- 在 AWS 控制台中,開啟「Identity and Access Management (IAM)」服務。
- 移至
- 點擊「Add provider」。
「Add an Identity provider screen」隨即開啟。
- 在「Configure provider」區段中,選取「OpenID Connect」。
- 對於提供者 URL,請輸入或貼上「Provider URL」。
-
如果您使用 API 呼叫範本,請複製並貼上 API 返回的
visionOneOidcProviderUrl參數。 -
如果您下載了範本,請輸入cloudaccounts-{region}.xdr.trendmicro.com,其中
{region}是您Trend Vision One的地區(us, eu, au, sg, in,或jp)例如,如果您的Trend Vision One地區是美國,您的visionOneOidcProviderUrl是cloudaccounts-us.xdr.trendmicro.com
-
- 對於「Audience」輸入arn:aws:iam::${AWSAccountId}:root。
將
${AWSAccountId}替換為您的 AWS 帳號 ID。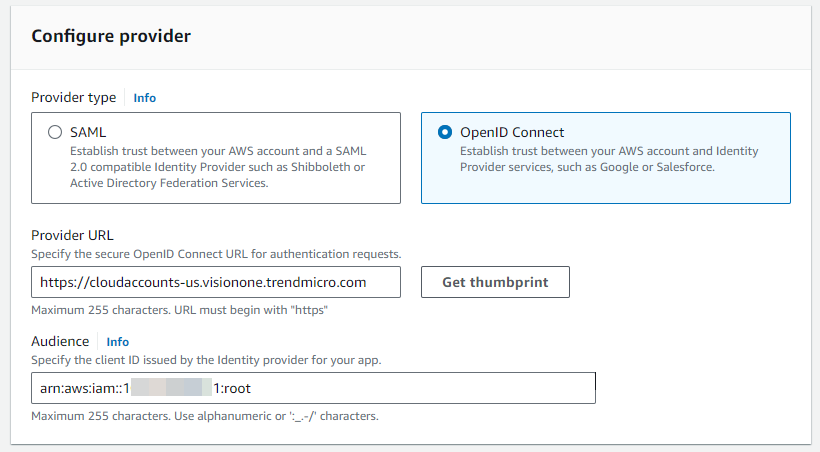
- 點擊「Get thumbprint」。
- 點擊「Add provider」。
提供者已新增至「Identity providers」清單。
- 點擊您創建的提供者名稱。
提供者詳細資訊畫面隨即開啟。
- 複製提供者 ARN,以便在稍後的步驟中建立角色時使用。
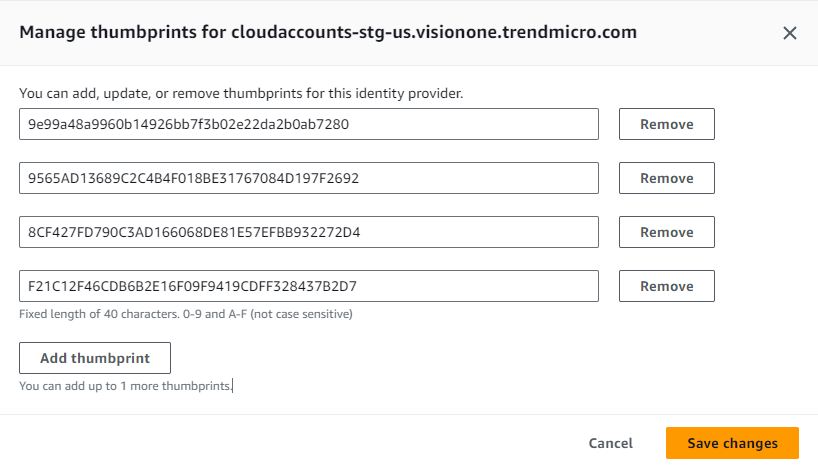
- 找到「Thumbprints」區段並點擊「Manage」。
- 刪除建立提供者時產生的指紋,然後貼上以下指紋。
按一下「Add thumbprint」以新增每一行。
-
9e99a48a9960b14926bb7f3b02e22da2b0ab7280 -
9565AD13689C2C4B4F018BE31767084D197F2692 -
8CF427FD790C3AD166068DE81E57EFBB932272D4 -
F21C12F46CDB6B2E16F09F9419CDFF328437B2D7
-
- 點擊「儲存變更」。
步驟 3:新增 Trend Vision One 政策
將 Trend Vision One 政策新增至 Identity and Access Management (IAM) 服務,以定義存取權限。若要檢視和複製這些政策,請參閱 JSON 格式的 AWS 政策。
重要對於每個政策,請確保保留程式碼的第二行
"Version": "2012-10-17"。刪除此行可能會導致政策無法正常運作。 |
步驟
- 在 「Identity and Access Management」 服務中,移至。
- 建立
VisionOnePolicyPart1政策:- 點擊「Create policy」。
- 對於「Policy editor」,請選取「JSON」。
- 使用您下載的範本檔案中
VisionOnePolicyPart1的相同參數來複製並替換Statement參數。您也可以點擊此連結直接查看並複製 JSON 代碼。 - 按「下一步」。
- 對於「策略名稱」,輸入VisionOnePolicyPart1。
- 點擊「Create policy」。
VisionOnePolicyPart1政策已建立,並顯示 「策略」 畫面。
- 建立
VisionOnePolicyPart2政策:- 點擊「Create policy」。
- 對於「Policy editor」,請選取「JSON」。您也可以點擊此連結直接查看並複製 JSON 代碼。
- 按「下一步」。
- 對於「策略名稱」,輸入VisionOnePolicyPart2。
- 點擊「Create policy」。已建立
VisionOnePolicyPart2政策,並顯示「策略」畫面。
- 建立
VisionOnePolicyPart3政策:- 點擊「Create policy」。
- 對於「Policy editor」,請選取「JSON」。您也可以點擊此連結以直接查看和複製 JSON 代碼。
- 按「下一步」。
- 對於「策略名稱」,輸入VisionOnePolicyPart3。
- 點擊「Create policy」。已建立
VisionOnePolicyPart3政策,並顯示「策略」畫面。
- 建立
VisionOneFeaturesPolicy原則:- 點擊「Create policy」。
- 對於「Policy editor」,請選取「JSON」。您也可以點擊此連結直接查看並複製 JSON 代碼。

重要
您必須將所有<AWS-Account-ID>的佔位符實例替換為您的 AWS 帳號 ID。 - 按「下一步」。
- 對於「策略名稱」,輸入VisionOneFeaturesPolicy。
- 點擊「Create policy」。已建立
VisionOneFeaturesPolicy政策,並顯示「策略」畫面。
步驟 4:使用 Terraform 部署 Container Security(可選)
在此可選步驟中,使用 Terraform 將 Container Security 部署到您的 AWS 帳戶,以保護您的 Amazon ECS 容器和容器映像。
此方法允許您在不需存取 Trend Vision One console 的情況下,在您的 AWS 帳戶上啟用 Container Security。如果您選擇不使用
Terraform 啟用 Container Security,您可以在帳戶連接後於 Trend Vision One 中在 AWS 帳戶上啟用它。欲了解更多資訊,請參閱使用現有的 AWS 帳戶連接 Amazon ECS 叢集。
步驟
- 存取 AWS 主控台。
- 使用以下命令將範本套件下載到您的環境:
curl https://container-security-us-east-1-484917860638.s3.amazonaws.com/templates/terraform/ecs_container_security_tf.zip --output container-security-terraform-package.zip - 使用下列命令提取範本:
unzip -o container-security-terraform-package.zip -d container-security-terraform-package
注意
您必須擁有在您的環境中解壓縮檔案的權限。 - 使用下列命令存取解壓縮的資料夾:
cd container-security-terraform-package - 使用以下命令將 terraform.tfvars.example 複製為 terraform.tfvars:
cp terraform.tfvars.example terraform.tfvars - 根據您所需的配置,修改
terraform.tfvars文件中的變數:- 使用以下端點值將「vision_one_endpoint_parameter_value」設置為符合您Trend Vision One地區:
- 根據需要設定其他變數。例如,使用「stackset_regions」來指定應安裝 Container Security 的所有 AWS 區域,或使用「common_tags」來指定應用於所有資源的自訂標籤。
- 使用以下端點值將「vision_one_endpoint_parameter_value」設置為符合您Trend Vision One地區:
- 使用以下命令部署 Terraform 模板:
terraform init terraform plan terraform apply

注意
您必須安裝 Terraform 才能完成此步驟。
步驟 5:新增 Trend Vision One 角色
- 新增 Trend Vision One 角色。
- 在 「Identity and Access Management」 服務中,移至。
- 點擊「Create role」。
- 對於「Trusted entity type」,請選取「Custom trust policy」。
The Custom trust policy JSON editor appears.
- 將佔位符代碼替換為以下 JSON 代碼:
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": { "Federated": "${visionOneOIDCProvider}" }, "Action": [ "sts:AssumeRoleWithWebIdentity", "sts:SetSourceIdentity" ], "Condition": { "StringEquals": { "${visionOneOIDCProviderURL}:aud": "arn:aws:iam::${AWSAccountId}:root", "${visionOneOIDCProviderURL}:sub": [ "urn:visionone:identity:${visionOneRegion}:${visionOneAccountID}:account/${visionOneAccountID}" ] } } } ] } - 替換以下參數的字串:
參數描述範例
"聯邦"將"${visionOneOIDCProvider}"替換為您在 步驟 2:新增 Trend Vision One 作為身份提供者 中建立的提供者 ARN。例如,如果您的Trend Vision One地區是美國,則 ARN 的格式為"arn:aws:iam::1xxxxxxxxxx1:oidc-provider/cloudaccounts-us.xdr.trendmicro.com""StringEquals"將兩個"${visionOneOIDCProviderURL}"替換為您在 步驟 2:新增 Trend Vision One 作為身份提供者 中創建提供者時使用的值。例如,如果您的Trend Vision One地區是美國,請使用cloudaccounts-us.xdr.trendmicro.com對於字串"arn:aws:iam::${AWSAccountID}:root",將${AWS::AccountID}替換為您的 AWS 帳號 ID。字串應遵循格式 "arn:aws:iam::1xxxxxxxxxx1:root"在以"urn:visionone:identity:..."開頭的字串中,替換以下參數:-
${visionOneRegion}:您使用的 Trend Vision One 區域(us, eu, au, sg, in,或jp) -
${visionOneAccountID}您的 Trend Vision One 商業 ID。請確保替換兩個實例。
如果您的Trend Vision One地區是美國,字串看起來像"urn:visionone:identity:us:1#####1:account/1#####1" -
- 按「下一步」。
- 在「Add permissions」畫面上,搜尋您建立的政策並選擇全部。
- 按「下一步」。
- 在「Name, review, and create」畫面中,於「角色名稱」輸入VisionOneRole。
- 在「Step 3: Add tags」下方,新增下列標籤。
機碼值VisionOne功能輸入下列其中一個值:
-
如果您在 步驟 4:使用 Terraform 部署 Container Security(可選) 中部署了 Container Security,請輸入 container-security
-
如果您未部署 Container Security,請將值保留為 VisionOneFeatures: Base。
VisionOneCloudFormationStackNameVision-One-雲端帳戶管理VisionOneCloudFormationStackRegion輸入您想要部署資源的 AWS 區域。例如,us-east-1。 -
- 點擊「Create role」。
- 創建完成後,點擊您創建的角色名稱。
- 在角色詳細資訊畫面中,複製 ARN 以便在稍後的步驟中使用 「Add AWS account」 API。
步驟 6:使用新增 AWS 帳戶 API 連接 AWS 帳戶
在此最後步驟中,您將提供參數值並調用「Add AWS account」 API 以將您的 AWS 帳戶連接到 Trend Vision One。
步驟
- 從自動化中心存取 API,或複製以下代碼進行自訂:
import json import requests BASE_URL = "https://api.xdr.trendmicro.com" # Modify this to the correct endpoint for your region following https://automation.trendmicro.com/xdr/Guides/Regional-domains/ ACCOUNTS_PATH = "/beta/xdr/cam/awsAccounts" TOKEN = "API Keys" # Required inputs ROLE_ARN = "YOUR_ROLEARN" # e.g. arn:aws:iam::123456789012:role/VisionOneRole ACCOUNT_NAME = "YOUR_ACCOUNT_NAME" # Display name in Cloud Accounts DESCRIPTION = "YOUR_DESCRIPTION" # Optional description # Features: # Leave empty to skip features will not enable any # Example structure # FEATURES = [ # { # "id": "container-security", # "regions": ["us-east-1"] # } # ] FEATURES = [] # Leave empty to skip features (will not enable V1CS) # Optional connected security services (example placeholder) # CONNECTED_SECURITY_SERVICES = [ # { # "name": "workload", # "instanceIds": ["INSTANCE_ID_1"] # } # ] CONNECTED_SECURITY_SERVICES = [] # Server Workload Protection settings # User can enable any AWS commercial region listed in https://docs.aws.amazon.com/general/latest/gr/rande.html # (the US GovCloud regions in that list are not supported). # Example structure (must match the regions you enable for the workload service): # SERVER_WORKLOAD_PROTECTION_REGIONS = ["us-east-1", "eu-west-1"] SERVER_WORKLOAD_PROTECTION_REGIONS = [] # Required when enabling Workload Security via workload service # Timeouts / settings REQUEST_TIMEOUT = 30 headers = { "Authorization": f"Bearer {TOKEN}", "Content-Type": "application/json;charset=utf-8", } # Base body (mirrors original script structure) body = { "roleArn": ROLE_ARN, "name": ACCOUNT_NAME, "description": DESCRIPTION, } if FEATURES: body["features"] = FEATURES if CONNECTED_SECURITY_SERVICES: body["connectedSecurityServices"] = CONNECTED_SECURITY_SERVICES def workload_service_selected(services): """Return True when workload service is present with at least one instance ID.""" for service in services: service_name = str(service.get("name", "")).strip().lower() instance_ids = service.get("instanceIds") or service.get("InstanceIDs") if service_name == "workload" and instance_ids: return True return False workload_selected = workload_service_selected(CONNECTED_SECURITY_SERVICES) if SERVER_WORKLOAD_PROTECTION_REGIONS: if not workload_selected: raise SystemExit( "SERVER_WORKLOAD_PROTECTION_REGIONS can only be specified when the workload connected security service is provided." ) body["serverWorkloadProtectionRegions"] = SERVER_WORKLOAD_PROTECTION_REGIONS elif workload_selected: raise SystemExit( "SERVER_WORKLOAD_PROTECTION_REGIONS must include at least one AWS region when Workload Security features are enabled." ) def list_accounts(): """Return list of existing AWS accounts or None if request fails.""" try: resp = requests.get(f"{BASE_URL}{ACCOUNTS_PATH}", headers=headers, timeout=REQUEST_TIMEOUT) if resp.status_code // 100 == 2: data = resp.json() if isinstance(data, dict) and "items" in data: return data.get("items", []) if isinstance(data, list): return data return None except Exception: return None def find_existing(accounts, role_arn, name): """Find existing account by roleArn or name; returns account dict or None.""" if not accounts: return None for acct in accounts: if acct.get("roleArn") == role_arn or acct.get("name") == name: return acct return None def _print_request(method: str, url: str, payload: dict): """Standardized pre-request logging to mimic legacy verbose output.""" print(f"Request URL: {url}") print(f"Request Headers: {headers}") if payload is not None: try: print("Request Body:") print(json.dumps(payload, indent=2)) except Exception: print(f"Request Body (raw): {payload}") def add_account(payload): url = f"{BASE_URL}{ACCOUNTS_PATH}" _print_request("POST", url, payload) return requests.post( url, headers=headers, params={}, json=payload, timeout=REQUEST_TIMEOUT, ) def patch_account(account_id, payload): url = f"{BASE_URL}{ACCOUNTS_PATH}/{account_id}" _print_request("PATCH", url, payload) return requests.patch( url, headers=headers, params={}, json=payload, timeout=REQUEST_TIMEOUT, ) def main(): print("Starting AWS account onboarding (idempotent)...") response = None accounts = list_accounts() if accounts is not None: existing = find_existing(accounts, ROLE_ARN, ACCOUNT_NAME) if existing and existing.get("id"): acct_id = existing["id"] print(f"Existing account found (id={acct_id}). Sending PATCH...") try: response = patch_account(acct_id, body) except Exception as e: print(f"PATCH failed ({e}); falling back to POST") response = add_account(body) else: print("No matching account found. Sending POST...") response = add_account(body) else: print("List call failed or returned nothing. Sending POST (original behavior)...") response = add_account(body) # Output diagnostics print("Status:", response.status_code) for k, v in response.headers.items(): print(f"{k}: {v}") print() ctype = response.headers.get("Content-Type", "") if "application/json" in ctype: try: print(json.dumps(response.json(), indent=4)) except Exception: print(response.text) else: print(response.text) if not (response.status_code // 100 == 2): raise SystemExit("Request failed. See output above.") if __name__ == "main" or __name__ == "__main__": main() - 在 API 代碼中提供以下參數的值:
-
參數值
ROLE_ARN您在步驟 5:新增 Trend Vision One 角色中創建的角色的ARN。ACCOUNT_NAME該帳戶在 Cloud Accounts 應用程式中顯示的名稱。名稱必須在 Cloud Accounts 應用程式中是唯一的。DESCRIPTION此帳戶的描述如同在 Cloud Accounts 應用程式中顯示。FEATURES執行下列其中一項作業:-
如果您未在 步驟 4:使用 Terraform 部署 Container Security(可選) 啟用 Container Security,請將此值留空。
-
若要啟用 Container Security,請提供以下數值:
-
"id": "container-security" -
"regions": ["us-east-1", "another region"]。新增所有您想啟用 Container Security 的區域。
-
TOKEN在 Server & Workload Protection 中建立 API 金鑰時顯示的值。欲了解詳細資訊,請參閱 使用 伺服器與工作負載保護 控制台創建 API 金鑰。
注意
在建立 API 金鑰時,令牌僅顯示一次。如果您無法確認,請建立新的金鑰以進行驗證。CONNECTED_SECURITY_SERVICES如果您已配置至少一個 Server & Workload Protection 實例,您必須為 CONNECTED_SECURITY_SERVICES提供以下參數:-
"name": "工作負載" -
Instance ID:您要與已連接的 AWS 帳戶關聯的伺服器及 Workload Protection 實例的 「執行個體 ID」您可以在 Trend Vision One 主控台上移至,來找到實例 ID。
重要
您只能將一個 Server & Workload Protection 實例與 AWS 帳戶連接關聯。
-
- 調用「Add AWS account」 API。該 API 返回現有已連接的 AWS 帳戶列表,並執行以下操作之一:
-
如果存在具有匹配
ROLE_ARN或ACCOUNT_NAME的 AWS 帳戶,則 API 會修補該帳戶以更新名稱和描述,並在您提供FEATURES參數所需的值時啟用 Container Security。 -
如果沒有返回匹配的 AWS 帳戶,Trend Vision One 中的 Cloud Accounts 應用程式會連接到您的 AWS 帳戶。您可以在 Cloud Accounts 應用程式中驗證連接,或透過調用 「Get Connected Accounts」 API 來驗證。
-
後續步驟
在Trend Vision One中查看 AWS 帳戶,請前往。您可以選擇在雲端帳號設定的AWS 堆疊更新標籤中啟用額外的安全功能。JSON 格式的 AWS 政策
允許雲端帳戶連接到您 AWS 帳戶所需的 AWS IAM 政策在 JSON 代碼塊中提供。
當手動將您的 AWS 帳戶連接到 Trend Vision One 雲端帳戶應用程式時,需要以下 JSON 代碼區塊。如果您從雲端帳戶下載堆疊模板檔案或使用 API 調用模板,則可以在其中找到這些代碼區塊。這些政策並不僅限於您的
AWS 帳戶或 Trend Vision One 帳戶。欲了解有關使用該代碼的更多資訊,請參見 手動連接 AWS 帳戶。
使用這些連結跳轉到您需要的政策代碼:
-
政策 1:
VisionOnePolicyPart1 -
政策 2:
VisionOnePolicyPart2 -
政策 3:
VisionOnePolicyPart3 -
政策 4:
VisionOneFeaturesPolicy
政策 1:
VisionOnePolicyPart1{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"access-analyzer:ListAnalyzers",
"access-analyzer:ListFindings",
"acm:DescribeCertificate",
"acm:ListCertificates",
"acm:ListTagsForCertificate",
"apigateway:GET",
"appflow:DescribeFlow",
"appflow:ListFlows",
"application-autoscaling:DescribeScalableTargets",
"application-autoscaling:DescribeScalingActivities",
"application-autoscaling:DescribeScalingPolicies",
"application-autoscaling:DescribeScheduledActions",
"athena:GetQueryExecution",
"athena:ListQueryExecutions",
"athena:ListTagsForResource",
"autoscaling:DescribeAccountLimits",
"autoscaling:DescribeAutoScalingGroups",
"autoscaling:DescribeAutoScalingInstances",
"autoscaling:DescribeLaunchConfigurations",
"autoscaling:DescribeLoadBalancerTargetGroups",
"autoscaling:DescribeLoadBalancers",
"autoscaling:DescribeNotificationConfigurations",
"autoscaling:DescribeTags",
"backup:DescribeBackupVault",
"backup:GetBackupVaultAccessPolicy",
"backup:ListBackupVaults",
"ce:GetAnomalies",
"ce:GetAnomalyMonitors",
"cloudformation:DescribeAccountLimits",
"cloudformation:DescribeStackDriftDetectionStatus",
"cloudformation:DescribeStackEvents",
"cloudformation:DescribeStackResources",
"cloudformation:DescribeStacks",
"cloudformation:DetectStackDrift",
"cloudformation:GetStackPolicy",
"cloudformation:GetTemplate",
"cloudformation:ListStackInstances",
"cloudformation:ListStackResources",
"cloudformation:ListStacks",
"cloudfront:GetDistribution",
"cloudfront:ListDistributions",
"cloudfront:ListTagsForResource",
"cloudtrail:DescribeTrails",
"cloudtrail:GetEventSelectors",
"cloudtrail:GetTrailStatus",
"cloudtrail:ListTags",
"cloudwatch:DescribeAlarms",
"cloudwatch:DescribeAlarmsForMetric",
"cloudwatch:GetMetricStatistics",
"cloudwatch:ListMetrics",
"comprehend:ListDocumentClassificationJobs",
"comprehend:ListDominantLanguageDetectionJobs",
"comprehend:ListEntitiesDetectionJobs",
"comprehend:ListKeyPhrasesDetectionJobs",
"comprehend:ListSentimentDetectionJobs",
"comprehend:ListTopicsDetectionJobs",
"compute-optimizer:GetAutoScalingGroupRecommendations",
"compute-optimizer:GetEC2InstanceRecommendations",
"config:DescribeComplianceByConfigRule",
"config:DescribeConfigRules",
"config:DescribeConfigurationRecorderStatus",
"config:DescribeConfigurationRecorders",
"config:DescribeDeliveryChannelStatus",
"config:DescribeDeliveryChannels",
"config:GetComplianceDetailsByConfigRule",
"config:GetResourceConfigHistory",
"config:SelectResourceConfig",
"dax:DescribeClusters",
"dax:ListTags",
"dms:DescribeReplicationInstances",
"dms:ListTagsForResource",
"ds:DescribeDirectories",
"ds:ListTagsForResource",
"dynamodb:DescribeContinuousBackups",
"dynamodb:DescribeLimits",
"dynamodb:DescribeTable",
"dynamodb:ListBackups",
"dynamodb:ListTables",
"dynamodb:ListTagsOfResource",
"ec2:DescribeAccountAttributes",
"ec2:DescribeAddresses",
"ec2:DescribeAvailabilityZones",
"ec2:DescribeEgressOnlyInternetGateways",
"ec2:DescribeFlowLogs",
"ec2:DescribeImages",
"ec2:DescribeInstanceAttribute",
"ec2:DescribeInstanceStatus",
"ec2:DescribeInstances",
"ec2:DescribeInternetGateways",
"ec2:DescribeKeyPairs",
"ec2:DescribeManagedPrefixLists",
"ec2:DescribeNatGateways",
"ec2:DescribeNetworkAcls",
"ec2:DescribeNetworkInterfaces",
"ec2:DescribeRegions",
"ec2:DescribeReservedInstances",
"ec2:DescribeRouteTables",
"ec2:DescribeSecurityGroupReferences",
"ec2:DescribeSecurityGroups",
"ec2:DescribeSnapshotAttribute",
"ec2:DescribeSnapshots",
"ec2:DescribeSubnets",
"ec2:DescribeTags",
"ec2:DescribeTransitGatewayPeeringAttachments",
"ec2:DescribeTransitGatewayRouteTables",
"ec2:DescribeTransitGateways",
"ec2:DescribeVolumes",
"ec2:DescribeVpcAttribute",
"ec2:DescribeVpcEndpoints",
"ec2:DescribeVpcPeeringConnections",
"ec2:DescribeVpcs",
"ec2:DescribeVpnConnections",
"ec2:DescribeVpnGateways",
"ec2:GetEbsEncryptionByDefault",
"ec2:SearchTransitGatewayRoutes",
"ecr:DescribeImages",
"ecr:DescribeRepositories",
"ecr:GetLifecyclePolicy",
"ecr:GetRepositoryPolicy",
"ecs:DescribeClusters",
"ecs:DescribeContainerInstances",
"ecs:DescribeServices",
"ecs:DescribeTaskDefinition",
"ecs:DescribeTasks",
"ecs:ListClusters",
"ecs:ListContainerInstances",
"ecs:ListServices",
"ecs:ListTagsForResource",
"ecs:ListTaskDefinitions",
"ecs:ListTasks",
"eks:DescribeCluster",
"eks:ListClusters",
"elasticache:DescribeCacheClusters",
"elasticache:DescribeReplicationGroups",
"elasticache:DescribeReservedCacheNodes",
"elasticache:ListTagsForResource",
"elasticbeanstalk:DescribeConfigurationSettings",
"elasticbeanstalk:DescribeEnvironments",
"elasticfilesystem:DescribeFileSystems",
"elasticfilesystem:DescribeTags",
"elasticloadbalancing:DescribeListeners",
"elasticloadbalancing:DescribeLoadBalancerAttributes",
"elasticloadbalancing:DescribeLoadBalancerPolicies",
"elasticloadbalancing:DescribeLoadBalancers",
"elasticloadbalancing:DescribeRules",
"elasticloadbalancing:DescribeTags",
"elasticloadbalancing:DescribeTargetGroups",
"elasticloadbalancing:DescribeTargetHealth",
"elasticmapreduce:DescribeCluster",
"elasticmapreduce:ListClusters",
"elasticmapreduce:ListInstances",
"es:DescribeElasticsearchDomain",
"es:DescribeElasticsearchDomainConfig",
"es:DescribeElasticsearchDomains",
"es:DescribeElasticsearchInstanceTypeLimits",
"es:DescribeReservedElasticsearchInstanceOfferings",
"es:DescribeReservedElasticsearchInstances",
"es:ListDomainNames",
"es:ListElasticsearchInstanceTypes",
"es:ListElasticsearchVersions",
"es:ListTags",
"events:DescribeEventBus",
"events:ListRules",
"firehose:DescribeDeliveryStream",
"firehose:ListDeliveryStreams",
"firehose:ListTagsForDeliveryStream",
"glue:GetDataCatalogEncryptionSettings",
"glue:GetDatabases",
"glue:GetSecurityConfiguration",
"glue:GetSecurityConfigurations",
"guardduty:GetDetector",
"guardduty:GetFindings",
"guardduty:ListDetectors",
"guardduty:ListFindings",
"health:DescribeAffectedEntities",
"health:DescribeEventDetails",
"health:DescribeEvents",
"iam:GenerateCredentialReport",
"iam:GetAccessKeyLastUsed",
"iam:GetAccountAuthorizationDetails",
"iam:GetAccountPasswordPolicy",
"iam:GetAccountSummary",
"iam:GetCredentialReport",
"iam:GetGroup",
"iam:GetGroupPolicy",
"iam:GetLoginProfile",
"iam:GetOpenIDConnectProvider"
],
"Resource": [
"*"
],
"Effect": "Allow"
}
]
}
政策 2:
VisionOnePolicyPart2{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"iam:GetPolicy",
"iam:GetPolicyVersion",
"iam:GetRole",
"iam:GetRolePolicy",
"iam:GetSAMLProvider",
"iam:GetServerCertificate",
"iam:GetUser",
"iam:GetUserPolicy",
"iam:ListAccessKeys",
"iam:ListAccountAliases",
"iam:ListAttachedGroupPolicies",
"iam:ListAttachedRolePolicies",
"iam:ListAttachedUserPolicies",
"iam:ListEntitiesForPolicy",
"iam:ListGroupPolicies",
"iam:ListGroups",
"iam:ListInstanceProfiles",
"iam:ListInstanceProfilesForRole",
"iam:ListMFADevices",
"iam:ListOpenIDConnectProviders",
"iam:ListPolicies",
"iam:ListPolicyTags",
"iam:ListPolicyVersions",
"iam:ListRolePolicies",
"iam:ListRoleTags",
"iam:ListRoles",
"iam:ListSAMLProviders",
"iam:ListSSHPublicKeys",
"iam:ListServerCertificates",
"iam:ListUserPolicies",
"iam:ListUserTags",
"iam:ListUsers",
"iam:ListVirtualMFADevices",
"inspector:DescribeAssessmentRuns",
"inspector:DescribeAssessmentTargets",
"inspector:DescribeAssessmentTemplates",
"inspector:DescribeExclusions",
"inspector:DescribeFindings",
"inspector:DescribeResourceGroups",
"inspector:ListAssessmentRuns",
"inspector:ListAssessmentTargets",
"inspector:ListAssessmentTemplates",
"inspector:ListExclusions",
"inspector:ListFindings",
"inspector:PreviewAgents",
"kafka:DescribeCluster",
"kafka:ListClusters",
"kafka:ListNodes",
"kinesis:DescribeStream",
"kinesis:ListStreams",
"kinesis:ListTagsForStream",
"kms:DescribeKey",
"kms:GetKeyPolicy",
"kms:GetKeyRotationStatus",
"kms:ListAliases",
"kms:ListGrants",
"kms:ListKeyPolicies",
"kms:ListKeys",
"kms:ListResourceTags",
"lambda:GetAccountSettings",
"lambda:GetFunctionConfiguration",
"lambda:GetPolicy",
"lambda:ListEventSourceMappings",
"lambda:ListFunctionUrlConfigs",
"lambda:ListFunctions",
"lambda:ListLayers",
"lambda:ListTags",
"logs:DescribeLogGroups",
"logs:DescribeLogStreams",
"logs:DescribeMetricFilters",
"macie2:GetClassificationExportConfiguration",
"macie2:GetFindingStatistics",
"macie2:ListClassificationJobs",
"mq:DescribeBroker",
"mq:ListBrokers",
"organizations:DescribeAccount",
"organizations:DescribeCreateAccountStatus",
"organizations:DescribeHandshake",
"organizations:DescribeOrganization",
"organizations:DescribeOrganizationalUnit",
"organizations:DescribePolicy",
"organizations:ListAWSServiceAccessForOrganization",
"organizations:ListAccounts",
"organizations:ListAccountsForParent",
"organizations:ListChildren",
"organizations:ListCreateAccountStatus",
"organizations:ListHandshakesForAccount",
"organizations:ListHandshakesForOrganization",
"organizations:ListOrganizationalUnitsForParent",
"organizations:ListParents",
"organizations:ListPolicies",
"organizations:ListPoliciesForTarget",
"organizations:ListRoots",
"organizations:ListTargetsForPolicy",
"rds:DescribeAccountAttributes",
"rds:DescribeDBClusters",
"rds:DescribeDBInstances",
"rds:DescribeDBParameterGroups",
"rds:DescribeDBParameters",
"rds:DescribeDBSecurityGroups",
"rds:DescribeDBSnapshotAttributes",
"rds:DescribeDBSnapshots",
"rds:DescribeEventSubscriptions",
"rds:DescribeEvents",
"rds:DescribeReservedDBInstances",
"rds:ListTagsForResource",
"redshift:DescribeClusterParameterGroups",
"redshift:DescribeClusterParameters",
"redshift:DescribeClusters",
"redshift:DescribeLoggingStatus",
"redshift:DescribeReservedNodes",
"redshift:DescribeTags",
"route53:GetDNSSEC",
"route53:GetGeoLocation",
"route53:ListHostedZones",
"route53:ListResourceRecordSets",
"route53:ListTagsForResource",
"route53domains:GetDomainDetail",
"route53domains:ListDomains",
"route53domains:ListTagsForDomain",
"s3:GetAccelerateConfiguration",
"s3:GetAccountPublicAccessBlock",
"s3:GetBucketAcl",
"s3:GetBucketLocation",
"s3:GetBucketLogging",
"s3:GetBucketObjectLockConfiguration",
"s3:GetBucketPolicy",
"s3:GetBucketPolicyStatus",
"s3:GetBucketPublicAccessBlock",
"s3:GetBucketTagging",
"s3:GetBucketVersioning",
"s3:GetBucketWebsite",
"s3:GetEncryptionConfiguration",
"s3:GetLifecycleConfiguration",
"s3:ListAllMyBuckets",
"s3:ListBucket",
"sagemaker:DescribeNotebookInstance",
"sagemaker:ListNotebookInstances",
"sagemaker:ListTags",
"secretsmanager:DescribeSecret",
"secretsmanager:ListSecrets",
"securityhub:DescribeHub",
"securityhub:GetEnabledStandards",
"securityhub:GetFindings",
"securityhub:GetInsightResults",
"securityhub:GetInsights",
"securityhub:GetMasterAccount",
"securityhub:GetMembers",
"securityhub:ListEnabledProductsForImport",
"securityhub:ListInvitations",
"securityhub:ListMembers",
"servicequotas:ListServiceQuotas",
"ses:GetIdentityDkimAttributes",
"ses:GetIdentityPolicies",
"ses:GetIdentityVerificationAttributes",
"ses:ListIdentities",
"ses:ListIdentityPolicies",
"shield:DescribeSubscription",
"sns:GetTopicAttributes",
"sns:ListSubscriptionsByTopic",
"sns:ListTagsForResource",
"sns:ListTopics",
"sqs:GetQueueAttributes",
"sqs:ListQueueTags",
"sqs:ListQueues",
"ssm:AddTagsToResource",
"ssm:DeleteParameter",
"ssm:DescribeInstanceInformation",
"ssm:DescribeParameters",
"ssm:DescribeSessions",
"ssm:GetParameters",
"ssm:PutParameter",
"ssm:RemoveTagsFromResource",
"storagegateway:DescribeNFSFileShares",
"storagegateway:DescribeSMBFileShares",
"storagegateway:DescribeTapes",
"storagegateway:ListFileShares",
"storagegateway:ListTagsForResource",
"storagegateway:ListTapes",
"support:DescribeSeverityLevels",
"support:DescribeTrustedAdvisorCheckRefreshStatuses",
"support:DescribeTrustedAdvisorCheckResult",
"support:DescribeTrustedAdvisorChecks",
"support:RefreshTrustedAdvisorCheck",
"tag:GetResources",
"tag:GetTagKeys",
"tag:GetTagValues",
"transfer:DescribeServer",
"transfer:ListServers",
"waf:GetWebACL",
"waf:ListWebACLs",
"wafv2:ListWebACLs",
"wellarchitected:GetWorkload",
"wellarchitected:ListWorkloads",
"workspaces:DescribeTags",
"workspaces:DescribeWorkspaceBundles",
"workspaces:DescribeWorkspaceDirectories",
"workspaces:DescribeWorkspaces",
"workspaces:DescribeWorkspacesConnectionStatus",
"xray:GetEncryptionConfig"
],
"Effect": "Allow",
"Resource": [
"*"
]
}
]
}
政策 3:
VisionOnePolicyPart3{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"sqs:ListQueueTags",
"sqs:ListQueues",
"ssm:DescribeInstanceInformation",
"ssm:DescribeParameters",
"ssm:DescribeSessions",
"ssm:GetParameter",
"ssm:GetParameters",
"ssm:GetParametersByPath",
"ssm:PutParameter",
"storagegateway:DescribeNFSFileShares",
"storagegateway:DescribeSMBFileShares",
"storagegateway:DescribeTapes",
"storagegateway:ListFileShares",
"storagegateway:ListTagsForResource",
"storagegateway:ListTapes",
"support:DescribeSeverityLevels",
"support:DescribeTrustedAdvisorCheckRefreshStatuses",
"support:DescribeTrustedAdvisorCheckResult",
"support:DescribeTrustedAdvisorChecks",
"support:RefreshTrustedAdvisorCheck",
"tag:GetResources",
"tag:GetTagKeys",
"tag:GetTagValues",
"transfer:DescribeServer",
"transfer:ListServers",
"waf:GetWebACL",
"waf:ListWebACLs",
"wafv2:GetWebACL",
"wafv2:ListWebACLs",
"wellarchitected:GetWorkload",
"wellarchitected:ListWorkloads",
"workspaces:DescribeTags",
"workspaces:DescribeWorkspaceBundles",
"workspaces:DescribeWorkspaceDirectories",
"workspaces:DescribeWorkspaces",
"workspaces:DescribeWorkspacesConnectionStatus",
"xray:GetEncryptionConfig"
],
"Resource": [
"*"
],
"Effect": "Allow"
}
]
}
政策 4:
VisionOneFeaturesPolicy
重要您必須將所有
<AWS-Account-ID> 的佔位符實例替換為您的 AWS 帳號 ID。 |
{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"lambda:ListTags"
],
"Effect": "Allow",
"Resource": [
"*"
]
},
{
"Action": [
"sqs:SendMessage"
],
"Effect": "Allow",
"Resource": [
"arn:aws:sqs:*:<Aws-Account-ID>:StackSet-V1CSStackSet-*"
]
},
{
"Action": [
"ecs:DescribeServices",
"ecs:DeleteService",
"ecs:UpdateService",
"ecs:CreateService",
"ecs:TagResource",
"ecs:UntagResource"
],
"Effect": "Allow",
"Resource": [
"arn:aws:ecs:*:<Aws-Account-ID>:service/*/trendmicro-scout"
]
},
{
"Action": [
"ssm:PutParameter",
"ssm:DeleteParameters",
"ssm:AddTagsToResource",
"ssm:RemoveTagsFromResource"
],
"Effect": "Allow",
"Resource": [
"arn:aws:ssm:*:<Aws-Account-ID>:parameter/V1CS/*"
]
},
{
"Action": [
"iam:PassRole"
],
"Effect": "Allow",
"Resource": [
"arn:aws:iam::aws:policy/service-role/AmazonECSTaskExecutionRolePolicy",
"arn:aws:iam::<Aws-Account-ID>:role/StackSet-V1CSStackSet-*-ExecutionRole-*",
"arn:aws:iam::<Aws-Account-ID>:role/StackSet-V1CSStackSet-*-TaskRole-*"
]
},
{
"Action": [
"ecs:StopTask"
],
"Effect": "Allow",
"Resource": [
"arn:aws:ecs:*:<Aws-Account-ID>:task/*"
]
}
]
}

