The Threats tab on the User information screen allows you to view all security threats detected
on endpoints assigned to the selected user.
You can access this screen from the following widgets on the tab on the Trend Micro Apex Central console.
-
Critical Threats: Click a number in the Important Users or Other Users columns and then click the user you want to view.
-
Users with Threats: Click the number in the Threats column for the user you want to view.
-
Endpoints with Threats: Click the number in the Threats column for the endpoint you want to view.
-
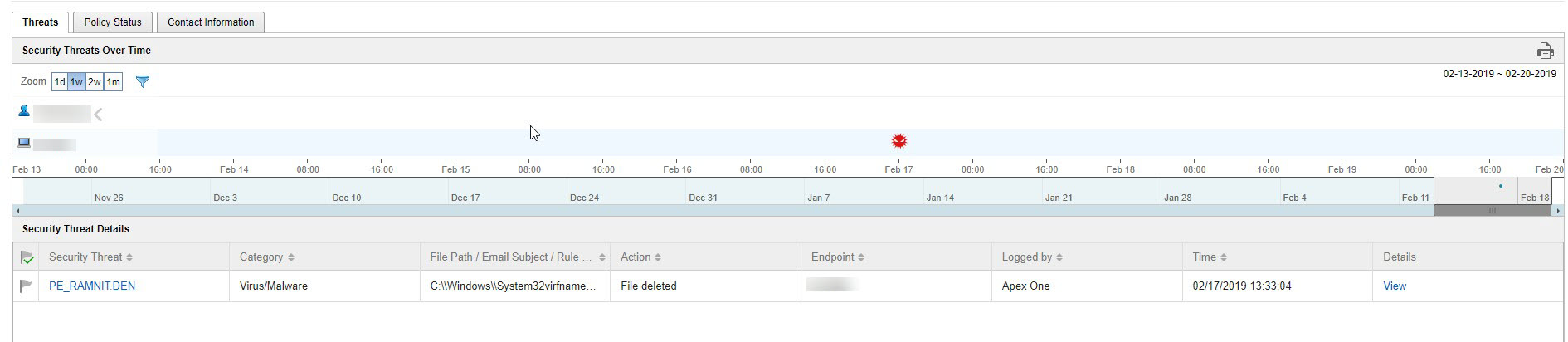
Security Threats Over Time: Provides a graphical representation of threat information based on the time of the detection and whether the detection occurred on an assigned endpoint or the user's account
-
Hover over a threat icon (for example,
 ) to view details about
the detection.
) to view details about
the detection. -
Change the displayed time interval by changing the Zoom value.
-
Change the end date by scrolling through the dates displayed under the graph.
-
Apply filters by clicking the funnel icon (
 ) and selecting the
following criteria and using the OR or
AND operators to build advanced filters.
) and selecting the
following criteria and using the OR or
AND operators to build advanced filters.-
Threat type: Select a threat category from the second drop-down list
-
Security threat: Type a malware name or suspicious URL, IP address, or sender email address
-
Threat status: Select Resolved by product, Action required, or Resolved manually
-
-
-
Security Threat Details: Provides more detailed information about the threats displayed on the Security Threats Over Time graph
-
Click a value in the Security Threat column to view the Affected Users screen.For more information, see Affected Users.
-
Click View link in the Details column to view detailed information.
-
Click a flag icon in the Threat Status column (
 ) to
change the threat status for threats that require remediation.
) to
change the threat status for threats that require remediation.
Note
Threat StatusDescriptionResolved by product ( )Indicates that the threat has been resolved by a managed product
)Indicates that the threat has been resolved by a managed product
Note
You cannot change this threat status.Action required ( )Indicates that remediation is requiredClick the Action required icon (
)Indicates that remediation is requiredClick the Action required icon ( )
to change the threat status to Resolved manually
(
)
to change the threat status to Resolved manually
( ).Resolved manually (
).Resolved manually ( )Indicates that remediation has been performed by an administratorClick the Resolved by product icon (
)Indicates that remediation has been performed by an administratorClick the Resolved by product icon ( )
to change the threat status to Action required
(
)
to change the threat status to Action required
( ).
).
-

