Using Mobile Device Management (MDM), administrators can configure the necessary permissions
for macOS agents to work without additional operations required from the end-user.
In addition to setting permissions, the sections below provide instructions to properly
deploy MDM so that Zero Trust Secure Access for macOS agents operates for the end-user
without pop-ups (asking for permission, for example).
NoteThis documentation provides detailed configuration instructions for Microsoft Intune.
For other MDM platforms such as Jamf, AirWatch (Workspace One), or other solutions,
please refer to Creating and Configuring MDM Profiles for TrendAI™ Security Agent for Mac.
|
Deploy Mobile Device Management profiles using Microsoft Intune
To deploy a Mobile Device Management profile using Microsoft Intune:
- Login to Microsoft Intune.
- Click Devices > macOS to enter the macOS devices settings page.
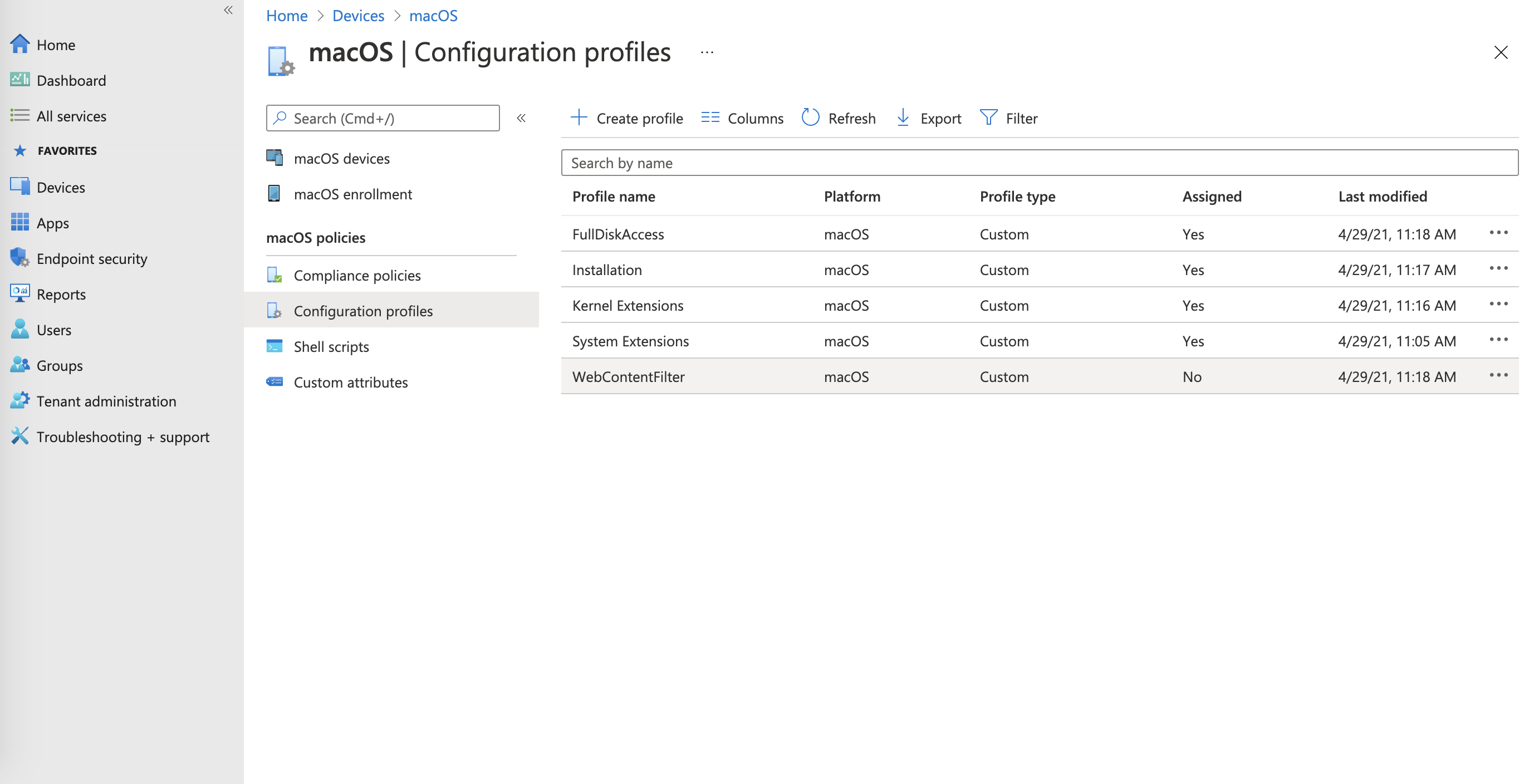
- Go to Configuration profiles > Create profile, and select Templates.
- Select Custom. (This method allows you upload self-created .mobileconfig files to deploy all types
of profiles including System Extensions, Web Content Filter, Full Disk Access, and
Service Management profiles.)
- In the Basics section, provide the Name and Description of the macOS profile.
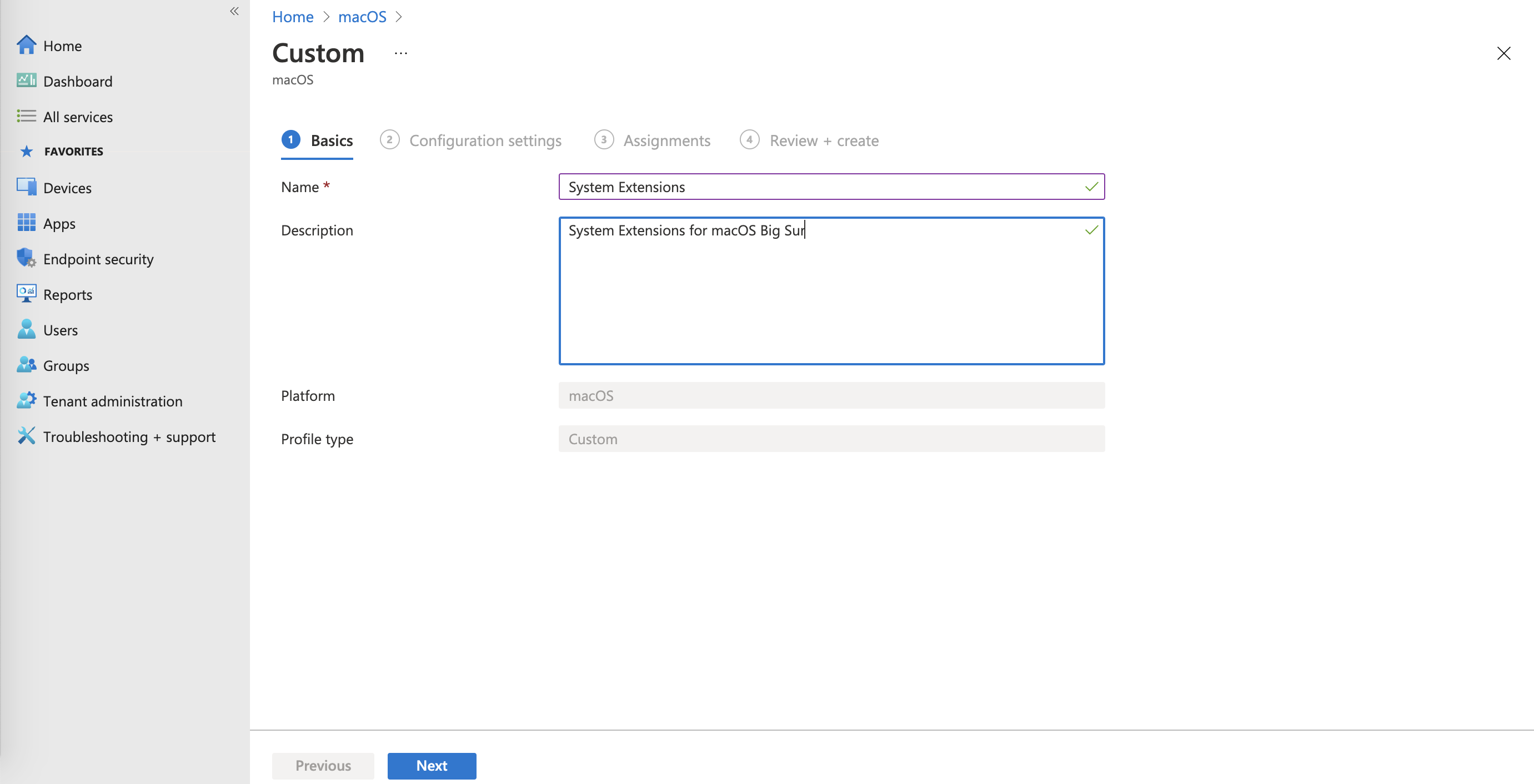
- In the Configuration settings section, add the Configuration profile name and upload your .mobileconfig Configuration profile file (for example, SystemExtension.mobileconfig).
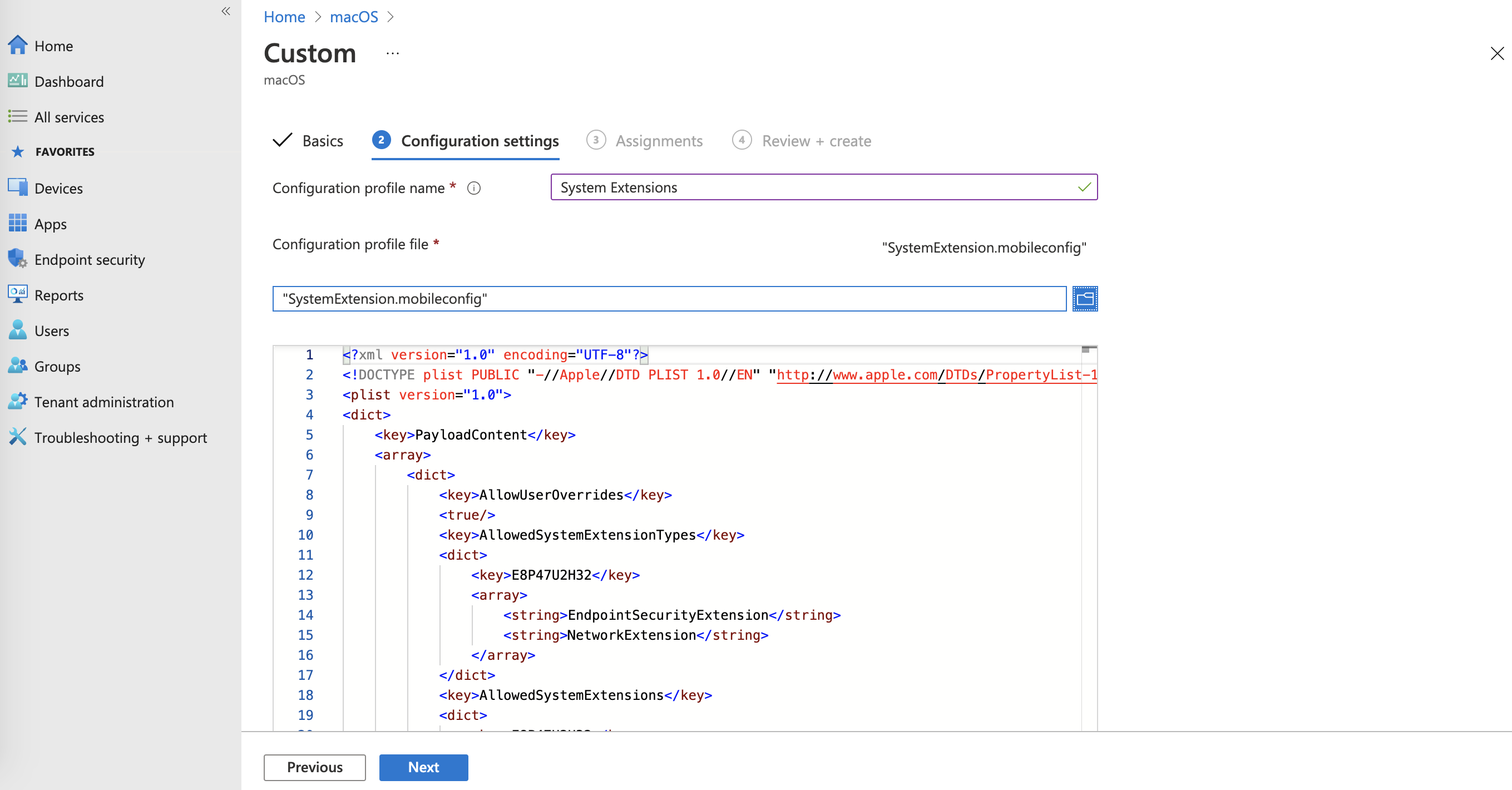
- In the Assignments section, set the Included groups or Excluded groups according to your needs to control which devices receive the profile.
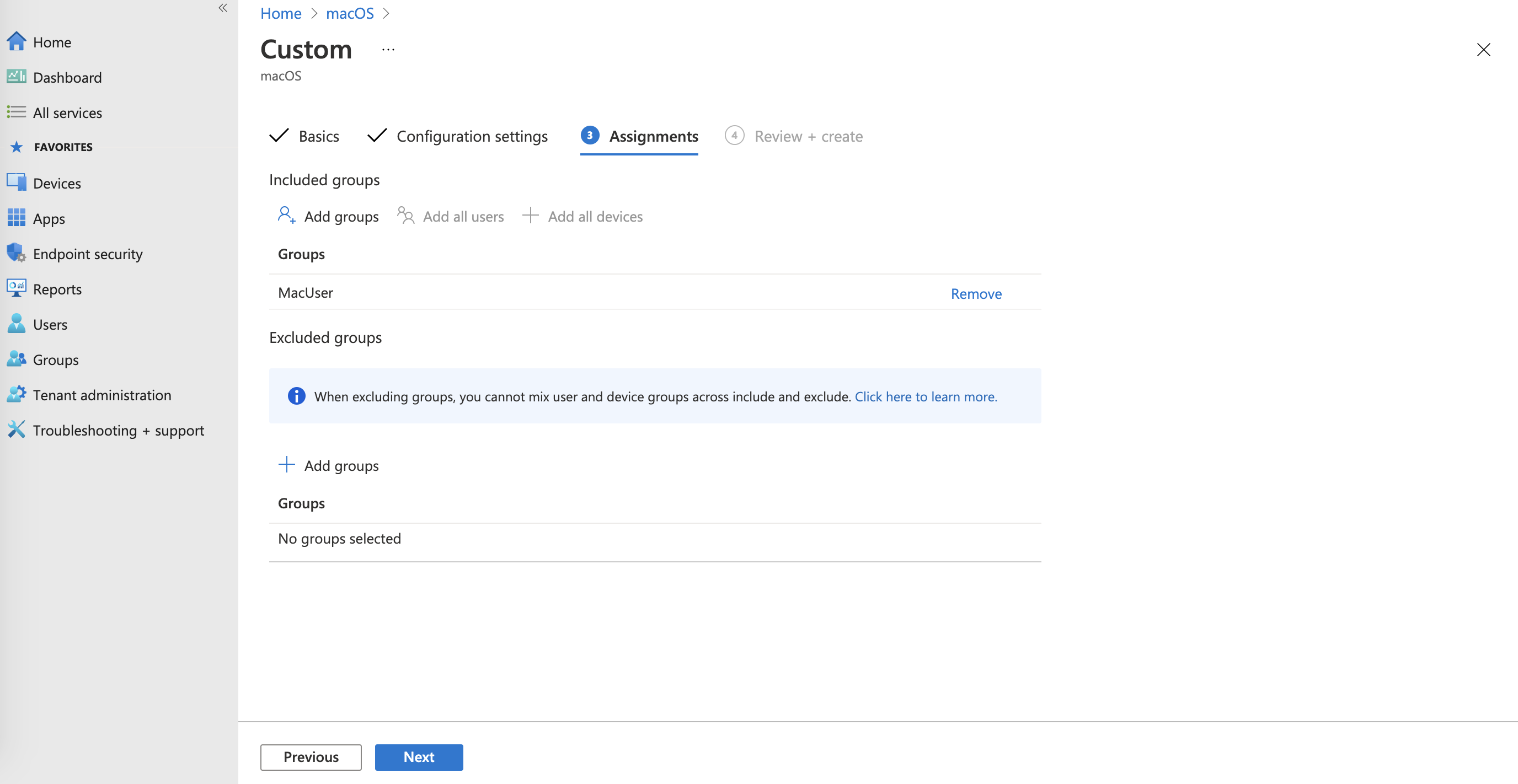
- In the Review + create section, review your configuration and then create the profile.
- In the Basics section, provide the Name and Description of the macOS profile.
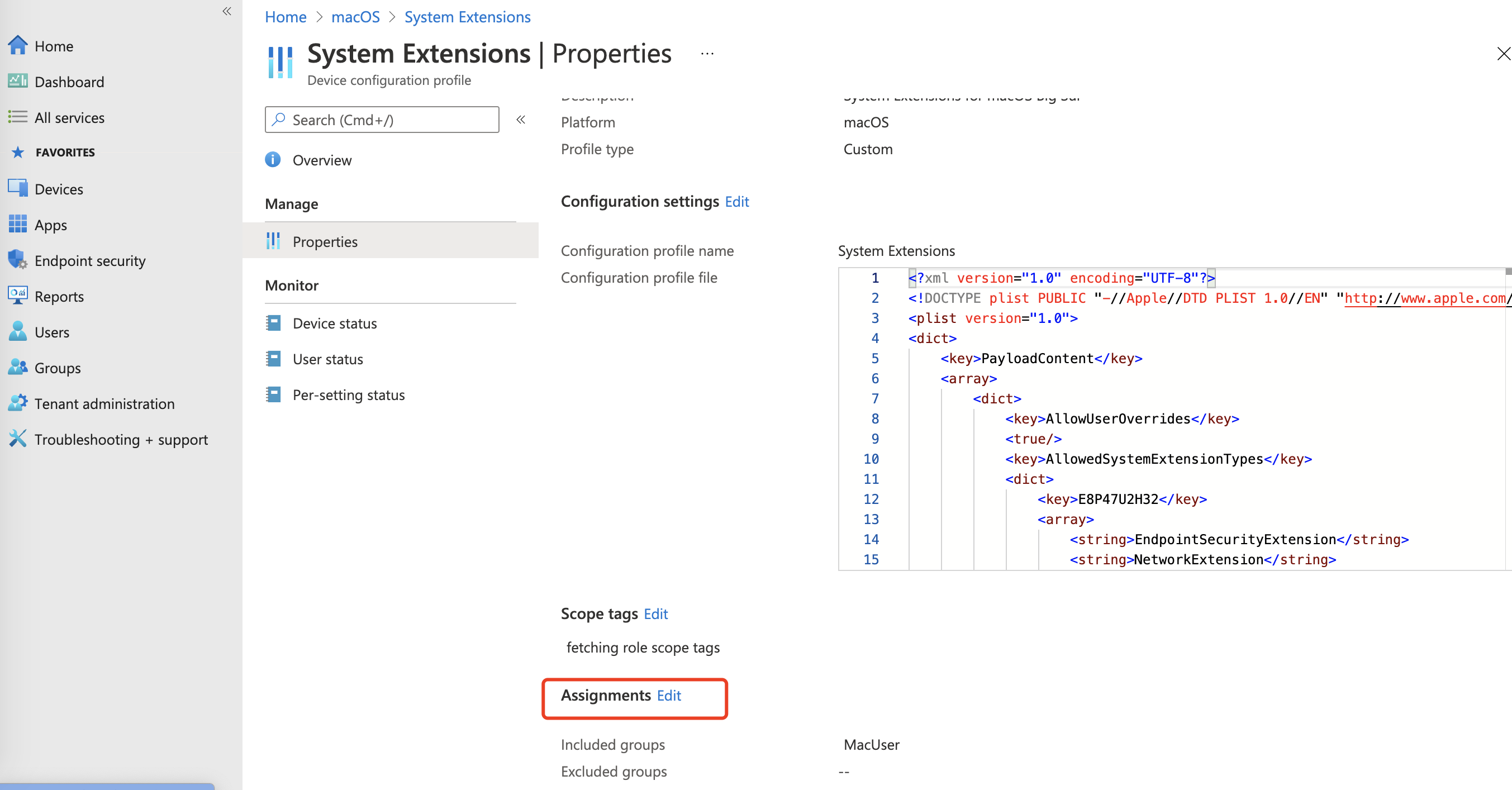
- If deployment does not update for a long time, click Assignments to execute again.

Tip
You can monitor the deployment progress in the profile overview page. Once finished, the Deployment Status will show "Succeeded".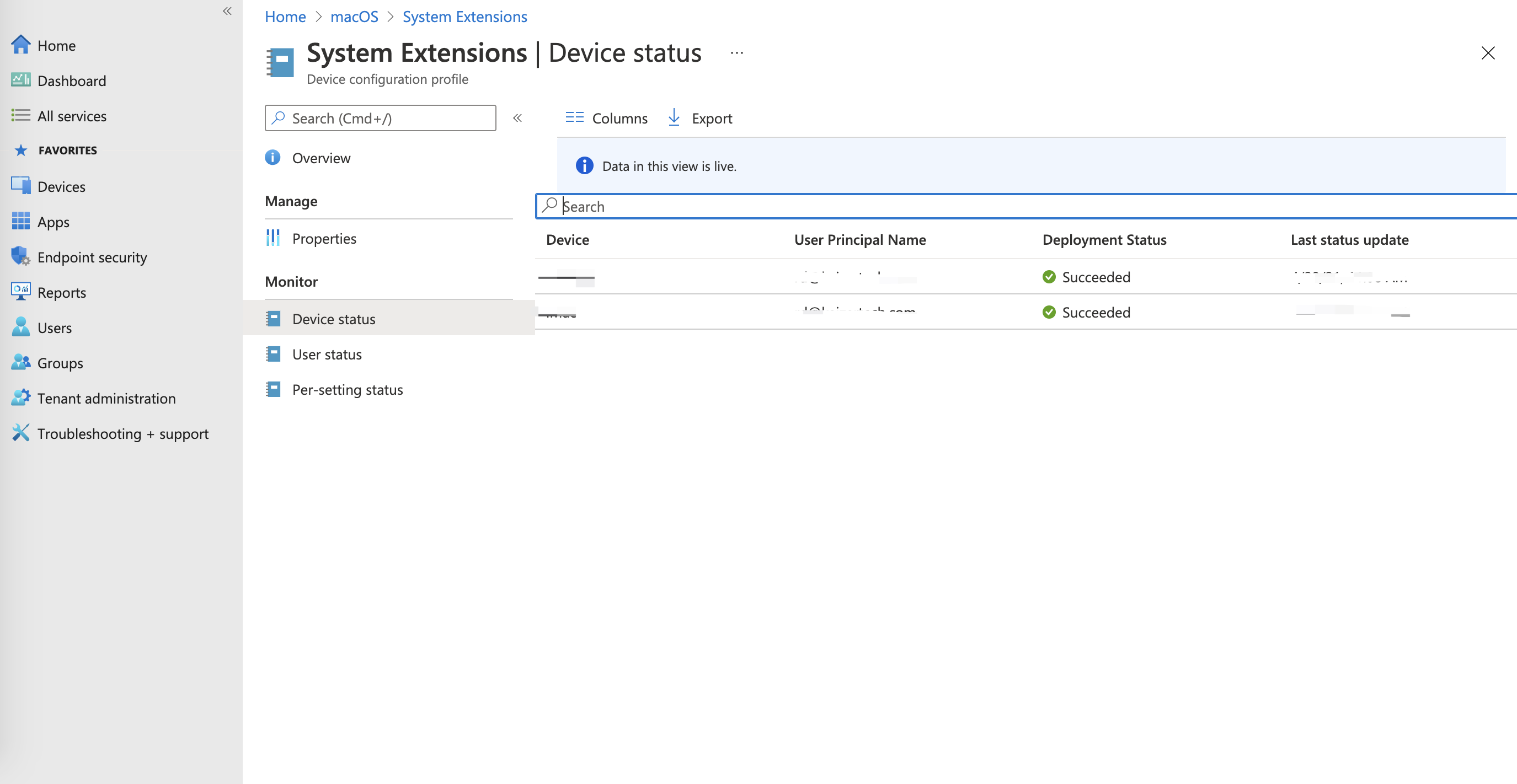
- On the managed Mac computer, verify that the profile installed by checking System Settings > Privacy & Security > Profiles.
- Repeat steps 3-6 for each required .mobileconfig profile (for System Extension, Web
Content Filter, Full Disk Access, and Service Management - Managed Login Items).
NoteFor alternative deployment methods or other MDM platforms, see Install Endpoint and Workload Security Agent for Mac via AirWatch (Workspace One)
and Microsoft Intune.
|
Configure system extensions
To comply with changes to the Apple guidelines for software developers, starting from
macOS Big Sur 11.0, kernel extensions are not loaded by the system. Zero Trust Secure
Access for macOS agent uses system extensions with Network Extension framework to
provide secure access functionality.
The Network Extension framework allows you to customize and extend core networking
features. For reference, see: https://developer.apple.com/documentation/networkextension.
The following system extension fields are required:
<key>AllowUserOverrides</key> <true/> <key>AllowedSystemExtensions</key> <dict> <key>E8P47U2H32</key> <array> <string>com.trendmicro.ztnasase.tunnel</string> </array> </dict> <key>PayloadType</key> <string>com.apple.system-extension-policy</string> <key>PayloadDisplayName</key> <string>System Extension</string>
Below is an example of a MDM configuration profile that allows system extensions:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>PayloadContent</key>
<array>
<dict>
<key>AllowUserOverrides</key>
<true/>
<key>AllowedSystemExtensions</key>
<dict>
<key>E8P47U2H32</key>
<array>
<string>com.trendmicro.ztnasase.tunnel</string>
</array>
</dict>
<key>PayloadDescription</key>
<string></string>
<key>PayloadDisplayName</key>
<string>System Extensions</string>
<key>PayloadEnabled</key>
<true/>
<key>PayloadIdentifier</key>
<string>com.yourorg.systemextension</string>
<key>PayloadOrganization</key>
<string>Your Org.</string>
<key>PayloadType</key>
<string>com.apple.system-extension-policy</string>
<key>PayloadUUID</key>
<string>170970B2-F040-49C1-9325-05E27BB63C6A</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
</array>
<key>PayloadDescription</key>
<string></string>
<key>PayloadDisplayName</key>
<string>System Extension</string>
<key>PayloadEnabled</key>
<true/>
<key>PayloadIdentifier</key>
<string>com.apple.system-extension-policy.EB63187C-EDAB-4CEE-9311-4DDB40587CED</string>
<key>PayloadOrganization</key>
<string>Your Org.</string>
<key>PayloadRemovalDisallowed</key>
<true/>
<key>PayloadScope</key>
<string>System</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadUUID</key>
<string>com.apple.system-extension-policy.EB63187C-EDAB-4CEE-9311-4DDB40587CED</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
</plist>
Configure web content filter
An on-device network content filter examines user network content as it passes through
the network stack and determines if that content should be blocked or allowed to pass
on to its final destination. For more details, see Content Filter Providers.
When creating an MDM profile, the following web content filter fields are required:
<key>FilterBrowsers</key> <true/> <key>FilterDataProviderBundleIdentifier</key> <string>com.trendmicro.ztnasase.tunnel</string> <key>FilterDataProviderDesignatedRequirement</key> <string>identifier "com.trendmicro.ztnasase" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string> <key>FilterGrade</key> <string>firewall</string> <key>FilterPackets</key> <true/> <key>FilterSockets</key> <true/> <key>FilterType</key> <string>Plugin</string> <key>PayloadType</key> <string>com.apple.webcontent-filter</string> <key>PluginBundleID</key> <string>com.trendmicro.ztnasase</string>
Below is an example of a Web Content Filter profile configuration to facilitate internal
VPN setup:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>PayloadContent</key>
<array>
<dict>
<key>FilterBrowsers</key>
<true/>
<key>FilterDataProviderBundleIdentifier</key>
<string>com.trendmicro.ztnasase.tunnel</string>
<key>FilterDataProviderDesignatedRequirement</key>
<string>identifier "com.trendmicro.ztnasase" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>FilterGrade</key>
<string>firewall</string>
<key>FilterPackets</key>
<true/>
<key>FilterSockets</key>
<true/>
<key>FilterType</key>
<string>Plugin</string>
<key>PayloadDescription</key>
<string>Adds a Web Content Filter</string>
<key>PayloadDisplayName</key>
<string>ZTSA Web Content Filter</string>
<key>PayloadIdentifier</key>
<string>D738AB74-9848-4097-9429-137DB1C9ZTSA</string>
<key>PayloadOrganization</key>
<string></string>
<key>PayloadType</key>
<string>com.apple.webcontent-filter</string>
<key>PayloadUUID</key>
<string>D738AB74-9848-4097-9429-137DB1C9ZTSA</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>PluginBundleID</key>
<string>com.trendmicro.ztnasase</string>
<key>UserDefinedName</key>
<string>TrendAI™ - ZTSA</string>
</dict>
</array>
<key>PayloadDescription</key>
<string>YourOrg</string>
<key>PayloadDisplayName</key>
<string>YourOrg</string>
<key>PayloadIdentifier</key>
<string>66CE283B-CA7E-49E3-BA51-A396ACE2ZTSA</string>
<key>PayloadOrganization</key>
<string>YourOrg</string>
<key>PayloadScope</key>
<string>System</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadUUID</key>
<string>A19134F2-F9C3-4F35-B10B-1E75613BZTSA</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
</plist>
Configure full disk access
NoteFor specific configuration instructions, see https://success.trendmicro.com/dcx/s/solution/000277823?language=en_US.
|
Full disk access permission is a privacy feature introduced in macOS Mojave (10.14)
that prevents some applications from accessing your important data in your Mail, Messages,
TimeMachine, and Safari files, for example. You'll need to manually grant permission
for certain applications to access these protected areas of your macOS endpoint.
NoteIn earlier versions of macOS (10.13 and lower), this permission is automatically granted
during installation of your product.
|
WARNINGIf full disk access is not enabled, Zero Trust Secure Access may not function properly
for certain network access scenarios and configuration management tasks.
|
In creating the Mobile Device Management profile for Full Disk Access, it is recommended
to use the Privacy Preferences Policy Control Utility (PPPC Utility) app.
Below are the required paths and permissions:
- Installer paths:
/Applications/Zero Trust Secure Access.app/Applications/Zero Trust Secure Access.app/Contents/MacOS/ztnp/Applications/Zero Trust Secure Access.app/Contents/MacOS/Zero Trust Secure Access
- Required Permissions:
- Properties:Accessibility → Allow
- Properties:All Files → Allow
- Apple Events:System Events → Allow
Below is an example of a PPPC configuration profile suppressing user prompts during
application execution:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>PayloadContent</key>
<array>
<dict>
<key>PayloadDescription</key>
<string> Your Org.- ZTSA PPPC</string>
<key>PayloadDisplayName</key>
<string> Your Org.- ZTSA PPPC</string>
<key>PayloadIdentifier</key>
<string>0AC7C2F2-B3E7-4B5F-8B92-A1F905501BAF</string>
<key>PayloadOrganization</key>
<string> Your Org.- ZTSA PPPC</string>
<key>PayloadType</key>
<string>com.apple.TCC.configuration-profile-policy</string>
<key>PayloadUUID</key>
<string>C47E2D8A-3A91-4E35-8027-1EABFEB50D9A</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>Services</key>
<dict>
<key>Accessibility</key>
<array>
<dict>
<key>Authorization</key>
<string>Allow</string>
<key>CodeRequirement</key>
<string>identifier "com.trendmicro.ztnasase" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>com.trendmicro.ztnasase</string>
<key>IdentifierType</key>
<string>bundleID</string>
</dict>
<dict>
<key>Authorization</key>
<string>Allow</string>
<key>CodeRequirement</key>
<string>identifier ztnp and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>/Applications/Zero Trust Secure Access.app/Contents/MacOS/ztnp</string>
<key>IdentifierType</key>
<string>path</string>
</dict>
<dict>
<key>Authorization</key>
<string>Allow</string>
<key>CodeRequirement</key>
<string>identifier "com.trendmicro.ztnasase" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>/Applications/Zero Trust Secure Access.app/Contents/MacOS/Zero Trust Secure Access</string>
<key>IdentifierType</key>
<string>path</string>
</dict>
<dict>
<key>Authorization</key>
<string>Allow</string>
<key>CodeRequirement</key>
<string>identifier "com.trendmicro.ztnasase.openvpn" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>com.trendmicro.ztnasase.openvpn</string>
<key>IdentifierType</key>
<string>bundleID</string>
</dict>
</array>
<key>AppleEvents</key>
<array>
<dict>
<key>AEReceiverCodeRequirement</key>
<string>identifier ztnp and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>AEReceiverIdentifier</key>
<string>/Applications/Zero Trust Secure Access.app/Contents/MacOS/ztnp</string>
<key>AEReceiverIdentifierType</key>
<string>path</string>
<key>Authorization</key>
<string>Allow</string>
<key>CodeRequirement</key>
<string>identifier "com.trendmicro.ztnasase" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>com.trendmicro.ztnasase</string>
<key>IdentifierType</key>
<string>bundleID</string>
</dict>
<dict>
<key>AEReceiverCodeRequirement</key>
<string>identifier "com.trendmicro.ztnasase" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>AEReceiverIdentifier</key>
<string>/Applications/Zero Trust Secure Access.app/Contents/MacOS/Zero Trust Secure Access</string>
<key>AEReceiverIdentifierType</key>
<string>path</string>
<key>Authorization</key>
<string>Allow</string>
<key>CodeRequirement</key>
<string>identifier "com.trendmicro.ztnasase" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>com.trendmicro.ztnasase</string>
<key>IdentifierType</key>
<string>bundleID</string>
</dict>
<dict>
<key>AEReceiverCodeRequirement</key>
<string>identifier "com.apple.systemevents" and anchor apple</string>
<key>AEReceiverIdentifier</key>
<string>com.apple.systemevents</string>
<key>AEReceiverIdentifierType</key>
<string>bundleID</string>
<key>Authorization</key>
<string>Allow</string>
<key>CodeRequirement</key>
<string>identifier "com.trendmicro.ztnasase" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>com.trendmicro.ztnasase</string>
<key>IdentifierType</key>
<string>bundleID</string>
</dict>
<dict>
<key>AEReceiverCodeRequirement</key>
<string>identifier "com.apple.systemevents" and anchor apple</string>
<key>AEReceiverIdentifier</key>
<string>com.apple.systemevents</string>
<key>AEReceiverIdentifierType</key>
<string>bundleID</string>
<key>Authorization</key>
<string>Allow</string>
<key>CodeRequirement</key>
<string>identifier ztnp and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>/Applications/Zero Trust Secure Access.app/Contents/MacOS/ztnp</string>
<key>IdentifierType</key>
<string>path</string>
</dict>
<dict>
<key>AEReceiverCodeRequirement</key>
<string>identifier "com.trendmicro.ztnasase" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>AEReceiverIdentifier</key>
<string>/Applications/Zero Trust Secure Access.app/Contents/MacOS/Zero Trust Secure Access</string>
<key>AEReceiverIdentifierType</key>
<string>path</string>
<key>Authorization</key>
<string>Allow</string>
<key>CodeRequirement</key>
<string>identifier ztnp and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>/Applications/Zero Trust Secure Access.app/Contents/MacOS/ztnp</string>
<key>IdentifierType</key>
<string>path</string>
</dict>
<dict>
<key>AEReceiverCodeRequirement</key>
<string>identifier "com.trendmicro.ztnasase" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>AEReceiverIdentifier</key>
<string>com.trendmicro.ztnasase</string>
<key>AEReceiverIdentifierType</key>
<string>bundleID</string>
<key>Authorization</key>
<string>Allow</string>
<key>CodeRequirement</key>
<string>identifier ztnp and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>/Applications/Zero Trust Secure Access.app/Contents/MacOS/ztnp</string>
<key>IdentifierType</key>
<string>path</string>
</dict>
<dict>
<key>AEReceiverCodeRequirement</key>
<string>identifier "com.apple.systemevents" and anchor apple</string>
<key>AEReceiverIdentifier</key>
<string>com.apple.systemevents</string>
<key>AEReceiverIdentifierType</key>
<string>bundleID</string>
<key>Authorization</key>
<string>Allow</string>
<key>CodeRequirement</key>
<string>identifier "com.trendmicro.ztnasase" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>/Applications/Zero Trust Secure Access.app/Contents/MacOS/Zero Trust Secure Access</string>
<key>IdentifierType</key>
<string>path</string>
</dict>
<dict>
<key>AEReceiverCodeRequirement</key>
<string>identifier "com.trendmicro.ztnasase" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>AEReceiverIdentifier</key>
<string>com.trendmicro.ztnasase</string>
<key>AEReceiverIdentifierType</key>
<string>bundleID</string>
<key>Authorization</key>
<string>Allow</string>
<key>CodeRequirement</key>
<string>identifier "com.trendmicro.ztnasase" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>/Applications/Zero Trust Secure Access.app/Contents/MacOS/Zero Trust Secure Access</string>
<key>IdentifierType</key>
<string>path</string>
</dict>
<dict>
<key>AEReceiverCodeRequirement</key>
<string>identifier ztnp and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>AEReceiverIdentifier</key>
<string>/Applications/Zero Trust Secure Access.app/Contents/MacOS/ztnp</string>
<key>AEReceiverIdentifierType</key>
<string>path</string>
<key>Authorization</key>
<string>Allow</string>
<key>CodeRequirement</key>
<string>identifier "com.trendmicro.ztnasase" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>/Applications/Zero Trust Secure Access.app/Contents/MacOS/Zero Trust Secure Access</string>
<key>IdentifierType</key>
<string>path</string>
</dict>
<dict>
<key>AEReceiverCodeRequirement</key>
<string>identifier "com.trendmicro.ztnasase" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>AEReceiverIdentifier</key>
<string>com.trendmicro.ztnasase</string>
<key>AEReceiverIdentifierType</key>
<string>bundleID</string>
<key>Authorization</key>
<string>Allow</string>
<key>CodeRequirement</key>
<string>identifier "com.trendmicro.ztnasase.openvpn" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>com.trendmicro.ztnasase.openvpn</string>
<key>IdentifierType</key>
<string>bundleID</string>
</dict>
<dict>
<key>AEReceiverCodeRequirement</key>
<string>identifier "com.apple.systemevents" and anchor apple</string>
<key>AEReceiverIdentifier</key>
<string>com.apple.systemevents</string>
<key>AEReceiverIdentifierType</key>
<string>bundleID</string>
<key>Authorization</key>
<string>Allow</string>
<key>CodeRequirement</key>
<string>identifier "com.trendmicro.ztnasase.openvpn" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>com.trendmicro.ztnasase.openvpn</string>
<key>IdentifierType</key>
<string>bundleID</string>
</dict>
</array>
<key>SystemPolicyAllFiles</key>
<array>
<dict>
<key>Authorization</key>
<string>Allow</string>
<key>CodeRequirement</key>
<string>identifier "com.trendmicro.ztnasase" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>com.trendmicro.ztnasase</string>
<key>IdentifierType</key>
<string>bundleID</string>
</dict>
<dict>
<key>Authorization</key>
<string>Allow</string>
<key>CodeRequirement</key>
<string>identifier ztnp and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>/Applications/Zero Trust Secure Access.app/Contents/MacOS/ztnp</string>
<key>IdentifierType</key>
<string>path</string>
</dict>
<dict>
<key>Authorization</key>
<string>Allow</string>
<key>CodeRequirement</key>
<string>identifier "com.trendmicro.ztnasase" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>/Applications/Zero Trust Secure Access.app/Contents/MacOS/Zero Trust Secure Access</string>
<key>IdentifierType</key>
<string>path</string>
</dict>
<dict>
<key>Authorization</key>
<string>Allow</string>
<key>CodeRequirement</key>
<string>identifier "com.trendmicro.ztnasase.openvpn" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>com.trendmicro.ztnasase.openvpn</string>
<key>IdentifierType</key>
<string>bundleID</string>
</dict>
</array>
<key>SystemPolicyDesktopFolder</key>
<array>
<dict>
<key>Authorization</key>
<string>Allow</string>
<key>CodeRequirement</key>
<string>identifier "com.trendmicro.ztnasase" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>com.trendmicro.ztnasase</string>
<key>IdentifierType</key>
<string>bundleID</string>
</dict>
<dict>
<key>Authorization</key>
<string>Allow</string>
<key>CodeRequirement</key>
<string>identifier ztnp and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>/Applications/Zero Trust Secure Access.app/Contents/MacOS/ztnp</string>
<key>IdentifierType</key>
<string>path</string>
</dict>
<dict>
<key>Authorization</key>
<string>Allow</string>
<key>CodeRequirement</key>
<string>identifier "com.trendmicro.ztnasase" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>/Applications/Zero Trust Secure Access.app/Contents/MacOS/Zero Trust Secure Access</string>
<key>IdentifierType</key>
<string>path</string>
</dict>
<dict>
<key>Authorization</key>
<string>Allow</string>
<key>CodeRequirement</key>
<string>identifier "com.trendmicro.ztnasase.openvpn" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>com.trendmicro.ztnasase.openvpn</string>
<key>IdentifierType</key>
<string>bundleID</string>
</dict>
</array>
<key>SystemPolicyDocumentsFolder</key>
<array>
<dict>
<key>Authorization</key>
<string>Allow</string>
<key>CodeRequirement</key>
<string>identifier "com.trendmicro.ztnasase" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>com.trendmicro.ztnasase</string>
<key>IdentifierType</key>
<string>bundleID</string>
</dict>
<dict>
<key>Authorization</key>
<string>Allow</string>
<key>CodeRequirement</key>
<string>identifier ztnp and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>/Applications/Zero Trust Secure Access.app/Contents/MacOS/ztnp</string>
<key>IdentifierType</key>
<string>path</string>
</dict>
<dict>
<key>Authorization</key>
<string>Allow</string>
<key>CodeRequirement</key>
<string>identifier "com.trendmicro.ztnasase" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>/Applications/Zero Trust Secure Access.app/Contents/MacOS/Zero Trust Secure Access</string>
<key>IdentifierType</key>
<string>path</string>
</dict>
<dict>
<key>Authorization</key>
<string>Allow</string>
<key>CodeRequirement</key>
<string>identifier "com.trendmicro.ztnasase.openvpn" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>com.trendmicro.ztnasase.openvpn</string>
<key>IdentifierType</key>
<string>bundleID</string>
</dict>
</array>
<key>SystemPolicyDownloadsFolder</key>
<array>
<dict>
<key>Authorization</key>
<string>Allow</string>
<key>CodeRequirement</key>
<string>identifier "com.trendmicro.ztnasase" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>com.trendmicro.ztnasase</string>
<key>IdentifierType</key>
<string>bundleID</string>
</dict>
<dict>
<key>Authorization</key>
<string>Allow</string>
<key>CodeRequirement</key>
<string>identifier ztnp and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>/Applications/Zero Trust Secure Access.app/Contents/MacOS/ztnp</string>
<key>IdentifierType</key>
<string>path</string>
</dict>
<dict>
<key>Authorization</key>
<string>Allow</string>
<key>CodeRequirement</key>
<string>identifier "com.trendmicro.ztnasase" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>/Applications/Zero Trust Secure Access.app/Contents/MacOS/Zero Trust Secure Access</string>
<key>IdentifierType</key>
<string>path</string>
</dict>
<dict>
<key>Authorization</key>
<string>Allow</string>
<key>CodeRequirement</key>
<string>identifier "com.trendmicro.ztnasase.openvpn" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = E8P47U2H32</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>com.trendmicro.ztnasase.openvpn</string>
<key>IdentifierType</key>
<string>bundleID</string>
</dict>
</array>
</dict>
</dict>
</array>
<key>PayloadDescription</key>
<string>Your Org</string>
<key>PayloadDisplayName</key>
<string>Your Org</string>
<key>PayloadIdentifier</key>
<string>0AC7C2F2-B3E7-4B5F-8B92-A1F905501BAF</string>
<key>PayloadOrganization</key>
<string>Your Org</string>
<key>PayloadScope</key>
<string>System</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadUUID</key>
<string>FEE78DB2-FAAC-4A56-9503-9ECFB7A0E419</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
</plist>
Configure Service Management - Managed Login Items (macOS 13.0 Ventura and later)
From macOS 13.0 Ventura, LaunchAgents and LaunchDaemons (in both /Library and ~/Library)
are now managed from the System Settings > General > Login Items pane. They are the items under "Allow in the Background".
The following configuration is required:
<key>Rules</key>
<array>
<dict>
<key>Comment</key>
<string>TrendAI™</string>
<key>RuleType</key>
<string>TeamIdentifier</string>
<key>RuleValue</key>
<string>E8P47U2H32</string>
</dict>
<dict>
<key>RuleType</key>
<string>LabelPrefix</string>
<key>RuleValue</key>
<string>com.trendmicro.ztnasase</string>
</dict>
</array>
Below is an example of a Service Management configuration profile that manages login
items and background processes:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>PayloadContent</key>
<array>
<dict>
<key>PayloadDisplayName</key>
<string>Service Management - Managed Login Items</string>
<key>PayloadIdentifier</key>
<string>com.apple.servicemanagement.EE60CA62-F2C3-4E0D-A5EE-0B48CAADF5DB</string>
<key>PayloadType</key>
<string>com.apple.servicemanagement</string>
<key>PayloadUUID</key>
<string>EE60CA62-F2C3-4E0D-A5EE-0B48CAADF5DB</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>Rules</key>
<array>
<dict>
<key>Comment</key>
<string>TrendAI™</string>
<key>RuleType</key>
<string>TeamIdentifier</string>
<key>RuleValue</key>
<string>E8P47U2H32</string>
</dict>
<dict>
<key>RuleType</key>
<string>LabelPrefix</string>
<key>RuleValue</key>
<string>com.trendmicro</string>
</dict>
<dict>
<key>RuleType</key>
<string>LabelPrefix</string>
<key>RuleValue</key>
<string>com.trendmicro.ztnasase</string>
</dict>
</array>
</dict>
</array>
<key>PayloadDisplayName</key>
<string>TrendAI™ - Login Items</string>
<key>PayloadIdentifier</key>
<string>B631E20B-CC84-4E45-991D-11258DA55B39</string>
<key>PayloadOrganization</key>
<string>TrendAI™, Inc.</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadUUID</key>
<string>B631E20B-CC84-4E45-991D-11258DA55B39</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
</plist>


