Configure reverse proxy mode on an Internet Access On-Premises Gateway in order to secure the use of your private general or generative AI applications.
Reverse proxy mode for the Internet Access On-Premises Gateway allows for additional
security and enhanced performance of your organization's private general or generative
AI applications. The on-premises gateway accepts HTTP or HTTPS requests from endpoints
and distributes the requests to your application or service according to your specifications.
If configured to protect a general private application, reverse proxy mode allows
you to create and apply internet access rules for the specific on-premises gateway
protecting the private application. You may enforce access control, threat protection,
and data loss prevention (DLP) specifically on requests made to the protected app.
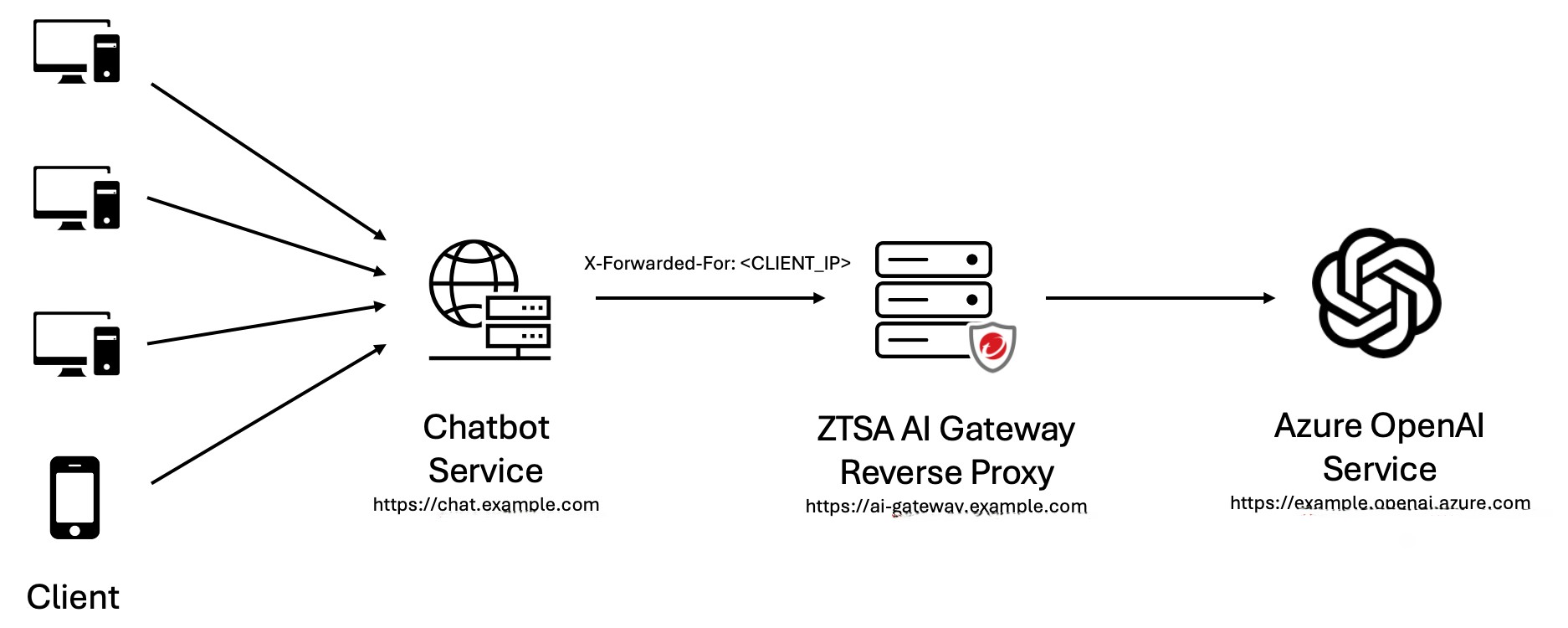
If configured to protect a private generative AI service, reverse proxy mode allows
you to create and apply AI secure access and rate limiting rules specifically for
the protected private generative AI service. The on-premises gateway receives requests
to your private generative AI service and can apply content filtering, prevent prompt
injection, and stop potential denial-of-service attacks with rate limiting rules.
When protecting a private generative AI service, the on-premises gateway configured
in reverse proxy mode must be deployed in front of the server hosting the service
in order to receive and manage requests.
When deploying the private gen AI access control, you can set the access control based
on the user by using the X-Authenticated-User option. By default the X-Authenticated-User
option not enabled and an on-premises gateway in reverse proxy mode can only apply
IP-based AI secure access rules.
To use this option, an X-Authenticated-User header needs to be inserted by a downstream
app that is deployed in front of the on-premises gateway. The value of this X-Authenticated-User
is the end-user's UPN info. This UPN must be associated with the user/group used to
create the user-based AI secure access rule. The format of header is:
X-Authenticated-User: example@domain.com
If this option is enabled, but the downstream app does not insert the header into
the forwarding traffic, the on-premises gateway applies any user or IP-based AI secure
access rule for such traffic.
Important
|
Procedure
- In Internet Access and AI Secure Access Configuration, deploy a new on-premises gateway or click the edit icon (
 ) corresponding to an existing on-premises gateway.
) corresponding to an existing on-premises gateway. - In the Advanced Settings tab, select Reverse proxy as the service mode. The default HTTP listening port is 8088.

Note
Enabling reverse proxy mode causes Internet Access and AI Secure Access to determine user count based on total vCPUs allocated to the corresponding Service Gateway. The new credit calculation will take effect in 24 hours. - If desired, enable HTTPS listening. The default HTTPS listening port is 8443.
- For HTTPS requests, choose to use the default SSL certificate or provide a custom certificate with private key and passphrase.
- (Optional) Provide the name of the app you wish to protect.
- (Optional) Specify whether the protected app is a general private app or a private
generative AI service.If you specify a Private generative AI service, you can use X-Authenticated-Users. This requires an AI Service rule. For more information, see Create an AI secure access rule.

Important
Rate limiting rules can only be applied to on-premises gateways in reverse proxy mode that are protecting a private generative AI service. - (Optional) Specify up to 10 FQDNs or IP addresses and ports used to connect to your
protected app.
- Specify the weight of traffic, from 0 to 100 percent, to be routed through each specified FQDN or IP address.
- Click Save.


