Simple. Quick. Cost-effective Solution.
Trend Micro understands how important it is to safeguard your network
and how costly the technology infrastructure can be to do this. Therefore, with our
expert cloud technology, we have created an elastic cloud-security gateway
product—Trend Micro Web Security.
As a cloud-based application, no capital expenditure needs to be
invested in either hardware or software. By using Trend Micro Web Security, you can
focus on strategic security, such as policy and architecture, rather than on the
operational tasks of managing network infrastructure.
Our Cloud Solution Will Help You:
- Protect against viruses or other security risks in file-uploads and downloads using highly configurable Anti-Malware Protection technology. In addition, Trend Micro Web Security scans for many types of spyware, grayware, and other risk types.
- Block websites determined by Web Reputation Service (WRS) to be malicious, based on a website’s reputation score.
- Control Internet applications discovered by Application Control using policies.
- Control access to any specific site using the Approved/Blocked lists.
- Scan traffic organized by URL categories, such as “Adult” and “Gambling”. When a user requests a URL, Trend Micro Web Security, using URL Filtering policies, first looks up the category for that URL and then allows, denies, or monitors access based on the policies set up.
- Monitor and analyze web traffic status using the dashboard reporting and log query feature.
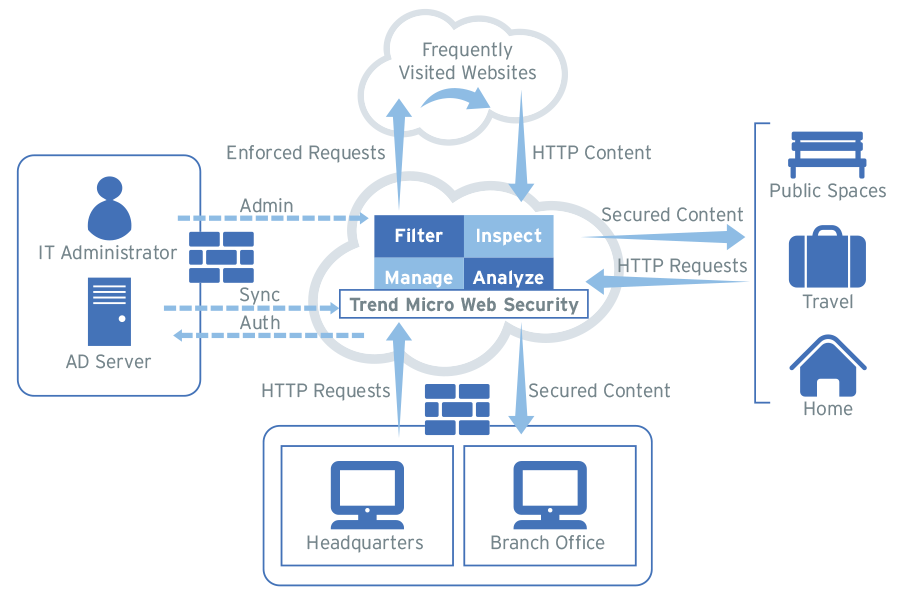
How Trend Micro Web Security Works
The diagram below illustrates how Trend Micro Web Security manages your
network traffic in the cloud. When a user sends an HTTP
request - whether inside or outside your firewall - that user's traffic is routed
through the cloud. Trend Micro Web Security inspects the request, analyzes it, and
filters it based on policies set by administrators. If the request is allowed, and
the user logs onto Trend Micro Web Security, then Trend Micro Web Security sends the
secure content back to the user. If the request is not allowed, for example a
request to a forbidden URL category, then Trend Micro Web Security blocks the
request and notifies the user.
Click the blue question mark button on any page to open help for that page.
Page-level help appears in a panel. Within this panel, information necessary to
complete the screen is found in the "Steps" tab and any information supporting this
procedure is found in a "More" tab.
You can access the table of content-type Help—the Help Contents from the Help menu
located in the main banner, along with the readme, Getting Started instructions, and
Getting Start Guide.


