The Logs screen allows you to view and manage log entries. You can also view infected files that the Security Agent has quarantined.
-
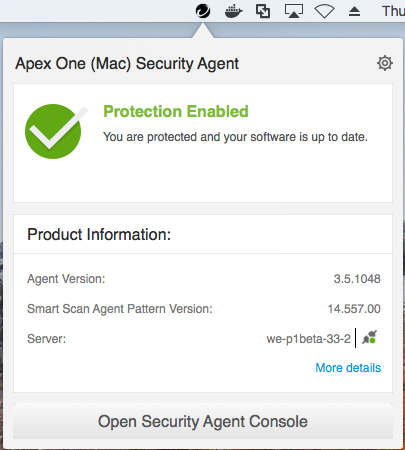
Click the Security Agent icon on your endpoint's system tray and
click Open Security Agent Console.
-
Click the view log icon (
 ) or click the
Virus/Malware detection number.
) or click the
Virus/Malware detection number.
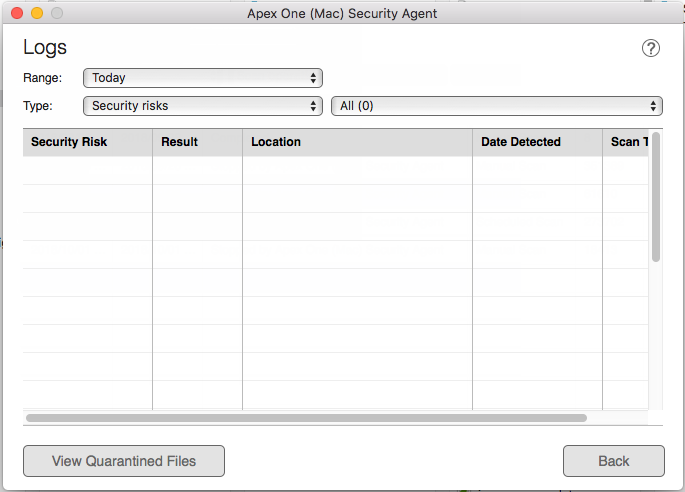
- Select a predefined time period or specify a custom time period.
-
Select a log type.
-
Security risks: Displays a list of security risks that the Security Agent has detected since the last time the list was deleted.
You can select a scan action to filter security risk logs.
-
Blocked web sites: Displays a list of websites that the Security Agent has blocked since the last time the list was deleted.
-
Scan operation: Displays the list of scan operations that the Security Agent has performed on the endpoint.
-
Device control: Displays the list of external storage device detected on the endpoint and the access permissions.
-
-
Click View Quarantined Files to
display quarantined files.
For details, see Working with Quarantined Files.

