The Connected Threat Defense strategy integrates many Trend Micro products. The following diagrams illustrate how the major products interact.
Figure 1. Endpoint Protection Example
Topology
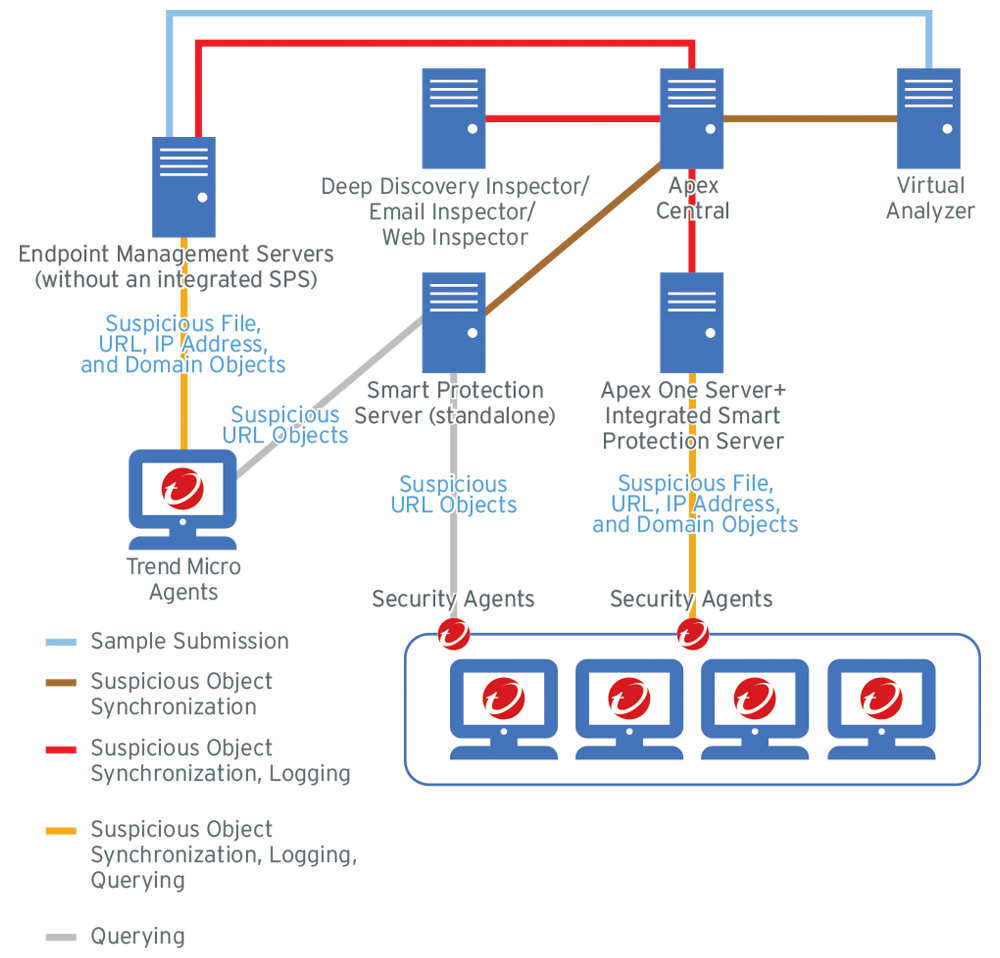

Figure 2. Messaging and Network Security Example
Topology
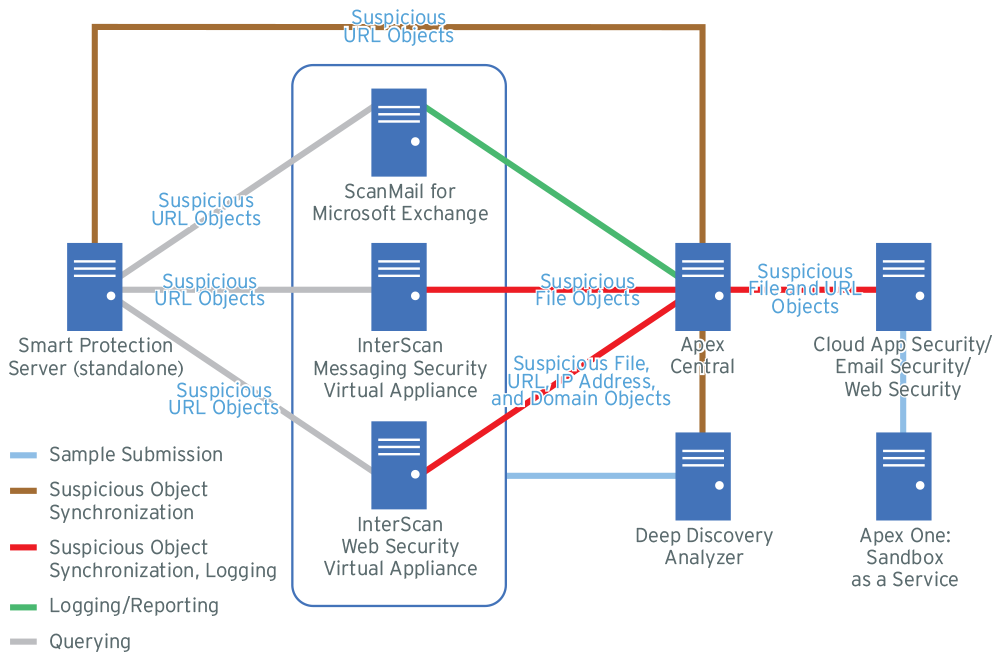

Apex Central further monitors other registered Trend Micro products through log analysis and comparison of detected files with the synchronized suspicious object lists.
For Apex Central registration and suspicious object list synchronization information for each major product, refer to the following:

