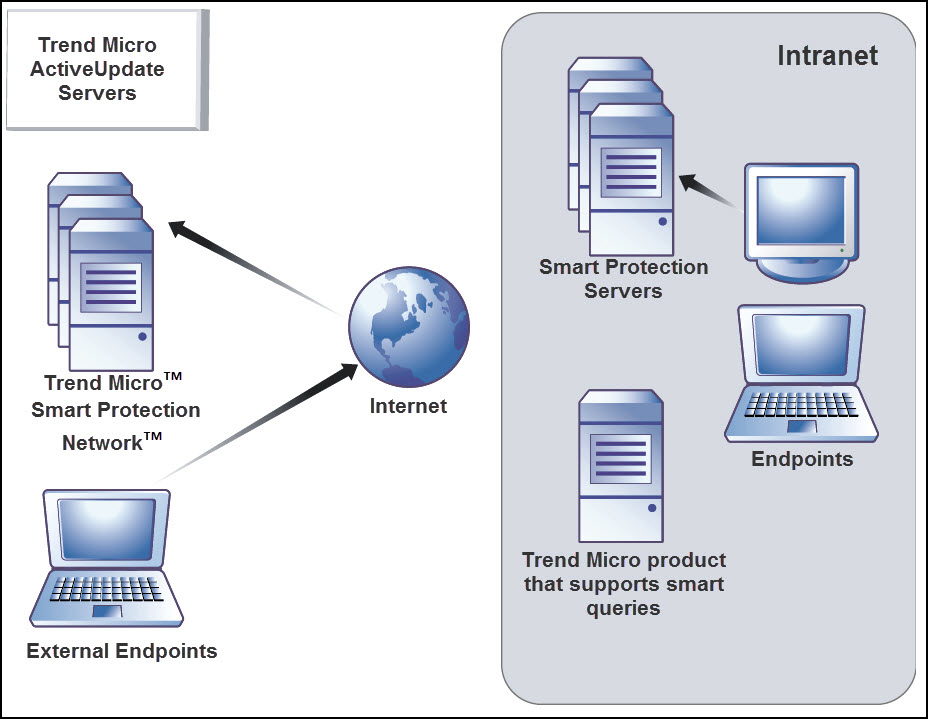
Endpoints that are currently in your intranet use Smart Protection Server computers for queries. Endpoints that are currently not in your intranet can connect to Trend Micro Smart Protection Network for queries.
While a network connection is required for utilizing Smart Protection Server computers, endpoints without access to network connection still benefit from Trend Micro technology. Smart Scan Agent Pattern and scan technology that reside on endpoints protect endpoints that do not have access to a network connection.
Agents installed on endpoints first perform scanning on the endpoint. If the agent cannot determine the risk of the file or URL, the agent verifies the risk by sending a query to a Smart Protection Server.
|
Location |
Pattern File and Query Behavior |
|---|---|
|
Access to intranet |
|
|
Without access to intranet |
|
Advanced filtering technology enables the agent to "cache" the query result. This improves scan performance and eliminates the need to send the same query to Smart Protection Server computers more than once.
An agent that cannot verify a file's risk locally and cannot connect to any Smart Protection Server computers after several attempts will flag the file for verification and temporarily allow access to the file. When connection to a Smart Protection Server is restored, all the files that have been flagged are re-scanned. Then, the appropriate scan action is performed on files that have been confirmed as a threat to your network.
Install multiple Smart Protection Server computers to ensure the continuity of protection in the event that connection to a Smart Protection Server is unavailable.