Some policies have controls to set a range of policy values, such as the minimum and maximum length for a password.
An example of editing policies with ranges is the Failed Login Attempts Allowed policy. Failed Login Attempts Allowed controls whether a device locks when a user exceeds the number of failed authentication attempts allowed.
Figure 1. Policy
with Ranges Window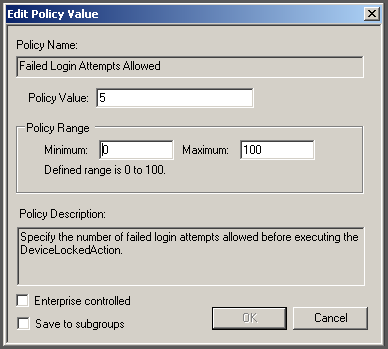

Using the parameters defined in the Policy Range fields, indicate the number of failed authentication attempts allowed per user in the Policy Value field.

