The Connection Details section of the Affected
Hosts - Detection Details screen contains the following information:
Click View in Threat Connect to connect with Threat Connect, where you can search for current information about
the threat.
Click Download and then select Connection
Details to download a CSV file of the connection details.
Click Download and then select Detected
File to download a password protected ZIP archive containing the detected file.
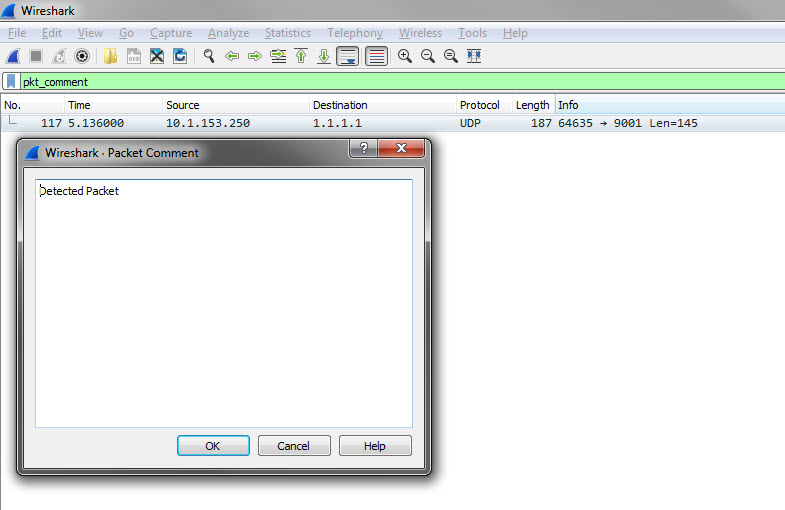
If a packet capture has been enabled and the detection matched a packet
capture rule, click Download and then select PCAP
File to download a password protected ZIP archive containing the pcap file. In
the pcap file, the comment "Detected Packet" in the "pkt_comment" field marks the
packet that
triggered the detection.
For details about packet capture, see Packet capture.
Click Download and then select
All to download a password protected ZIP archive containing the
detected file, the packet capture file, and the connection details.
ImportantSuspicious files and pcap files must always be handled with caution.
Extract the detected file and pcap file at your own risk. Trend Micro recommends analyzing the files in an
isolated environment.
The password for the zip archive is "virus".
|
Affected Hosts - Detection Details - Detection Information
Information provided in the Detection
Information section may include the following:
-
Activity detected
-
Attack phase
-
Correlation Rule ID (ICID)
-
Detection name
-
Detection rule ID

Tip
Click the detection rule number to view more details about the rule in the Threat Encyclopedia. -
Detection severity
-
Detection type
-
Event class
-
MITRE ATT&CK™ Framework
-
Tactics
-
Techniques

Tip
Click the tactic or technique to view more details on the MITRE website.© ATT&CK™ is a trademark of the MITRE Corporation. -
-
Notable Object
-
Protocol
-
Reference
-
Targeted attack campaign
-
Targeted attack related
-
Threat
-
Threat description
-
Timestamp
-
URL category
-
Virtual Analyzer risk level
NoteAdditional information may appear for specific correlated incidents.
|
Detection Types
|
Detection Types
|
Description
|
|
Correlated Incident
|
Events/detections that occur in a sequence or reach a
threshold and define a pattern of activity
|
|
Disruptive Application
|
Any peer-to-peer, instant messaging, or streaming media
applications considered to be disruptive because they may do the following:
|
|
Exploit
|
Network and file-based attempts to access information
|
|
Grayware
|
Adware/grayware detections of all types and confidence
levels
|
|
Malicious Behavior
|
Behavior that definitely indicates compromise with no
further correlation needed, including the following:
|
|
Malicious Content
|
File signature detections
|
|
Malicious URL
|
Websites that try to perform malicious activities
|
|
Suspicious Behavior
|
Behavior that could indicate compromise but requires
further correlation to confirm, including the following:
|
Affected Hosts - Detection Details - Connection Summary
Information provided in the Connection Summary
section may include the following:
-
A graphical display that includes the direction of the event and other information. The Client in the diagram is the host that initiated the connection.
-
Host details may include the following:
-
Host name
-
IP address and port
-
Last logon user
-
MAC address
-
Network group
-
Network zone
-
Operating system
-
Affected Hosts - Detection Details - Protocol Information
Information provided in the Protocol Information
section may include the following:
-
BOT command
-
BOT URL
-
Certificate Information
-
Issued To
-
Common name
-
Organization
-
Organizational unit
-
-
Issued By
-
Common name
-
Organization
-
Organizational unit
-
-
-
Domain name
-
Host name
-
HTTP referer
-
ICMP code
-
ICMP type
-
IRC channel name
-
IRC nick name
-
Message ID
-
Protocol
-
Queried domain
-
Recipients
-
Sender
-
SNI host name
-
Subject
-
Target share
-
Transport Layer Security (TLS)
-
URL
-
User agent
-
User name
Affected Hosts - Detection Details - File Information
Information provided in the File Information section
may include the following:
-
File name
-
File SHA-1
-
File SHA-256
-
File size
Affected Hosts - Detection Details - Additional Information
Information provided in the Additional Information
section may include the following:
-
Attempted to disrupt connection
-
Detected by
-
Mitigation
-
Fingerprinting
-
JA3 hash value
-
JA3S hash value
-
-
VLAN ID


