- On the Deep Discovery Email Inspector management console, go to Administration > Integrated Products/Services > Auxiliary Products/Services.
- Select Check Point Open Platform for Security (OPSEC).
- Under Object Distribution, select Enable.
-
Under Server Settings, select a connection type.
Note:
Ensure that your network configuration allows Deep Discovery Email Inspector to connect to the Check Point appliance.
Deep Discovery Email Inspector may connect to the Check Point appliance through the secured connection port or clear connection port that is configured on the Check Point appliance. Deep Discovery Email Inspector also pulls the certificate from the Check Point appliance through port 18210.
If you selected Secured connection, the OPSEC application name and SIC one-time password settings appear.
-
Type a server name.
Note:
The server name must be the FQDN or IPv4 address of the auxiliary product.
-
If you selected Secured connection, type the
OPSEC application name and SIC one-time
password.
For more details, see Configuring a Secured Connection.
Note:If the one-time password is reset on the Check Point appliance, the new one-time password must be different than the previous one-time password.
-
Type the port.
Note:
This port must be the same port that is configured on the security gateway. For details, see Preconfiguring a Security Gateway.
- (Optional) Click Test Connection.
-
To send object information from Deep Discovery Email
Inspector to this
product/service, configure the following criteria:
-
Object type:
-
Suspicious Object
-
IPv4 address
-
-
-
Risk level:
-
High only
-
High and medium
-
High, medium, and low
-
-
- Click Save.
- On your Check Point firewall appliance, preconfigure a security gateway. For details see Preconfiguring a Security Gateway.
-
Go to Check Point SmartConsole and do the following to configure your Check
Point appliance for deploying suspicious objects from Deep Discovery Email
Inspector:
-
On the SECURITY POLICIES tab, go to Access Control > Policy.
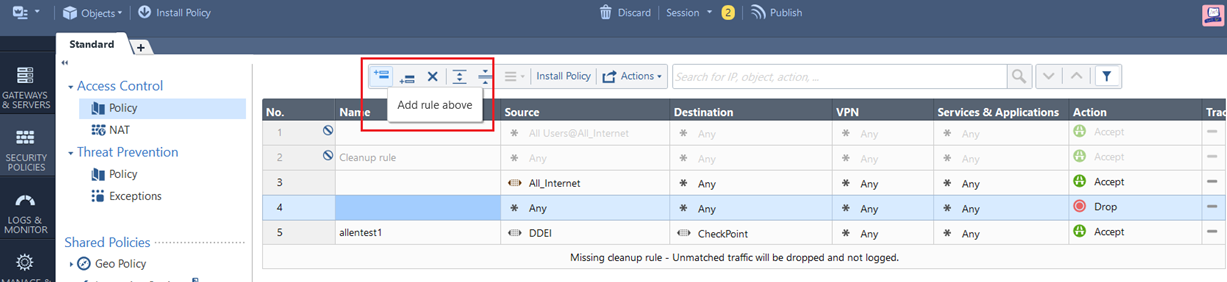
-
To add a rule, click the Add rule above
 icon.
icon.
- To configure the new policy, right-click the action.
- Change the action to Accept.
-
Right-click the source.
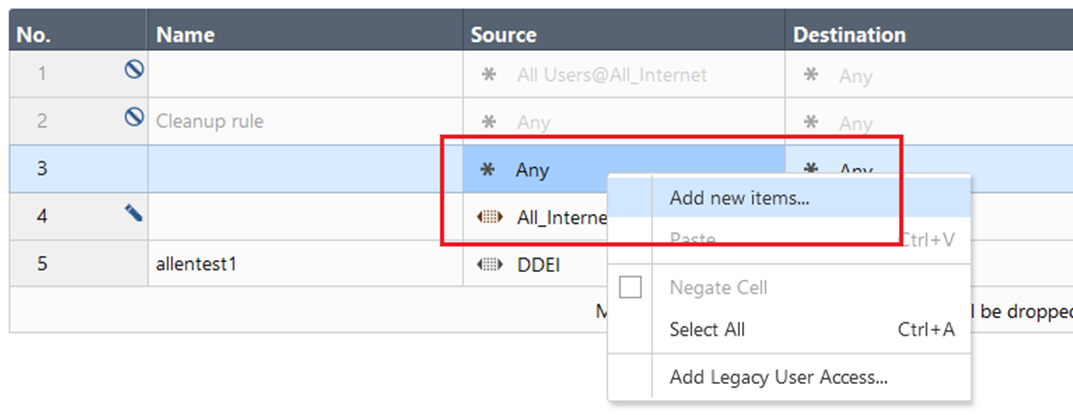
-
Select Add new items....
The following screen appears.
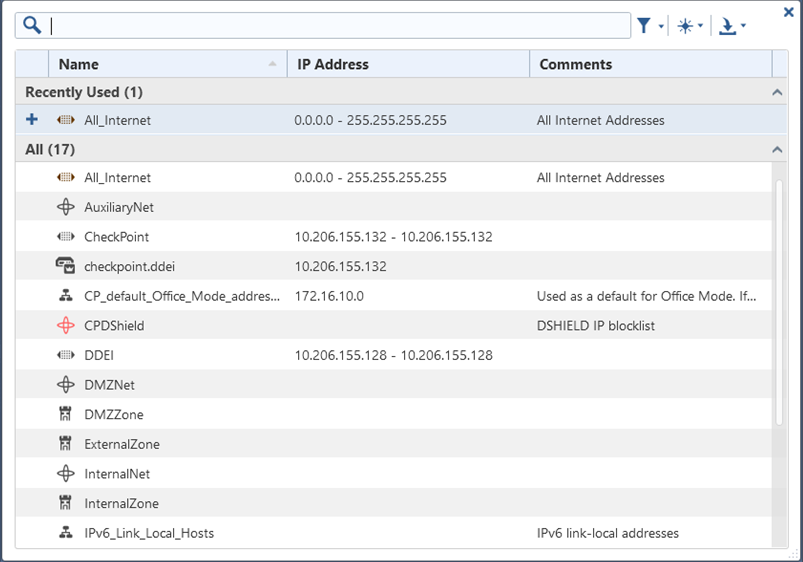
-
Click the new icon (
 ).
).
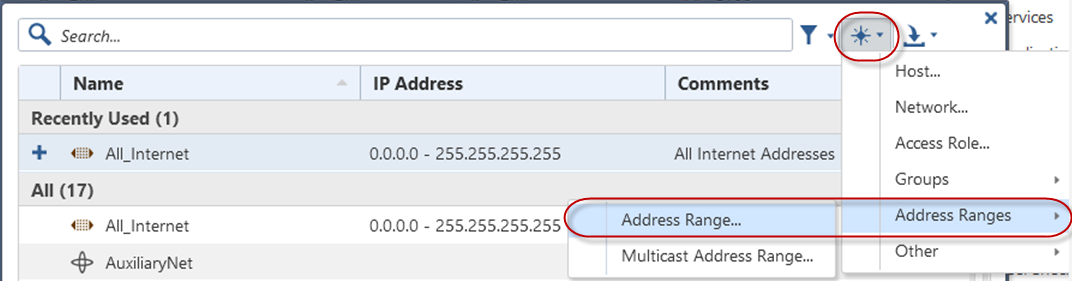
-
Select Address Ranges > Address Range....
The New Address Range window appears.
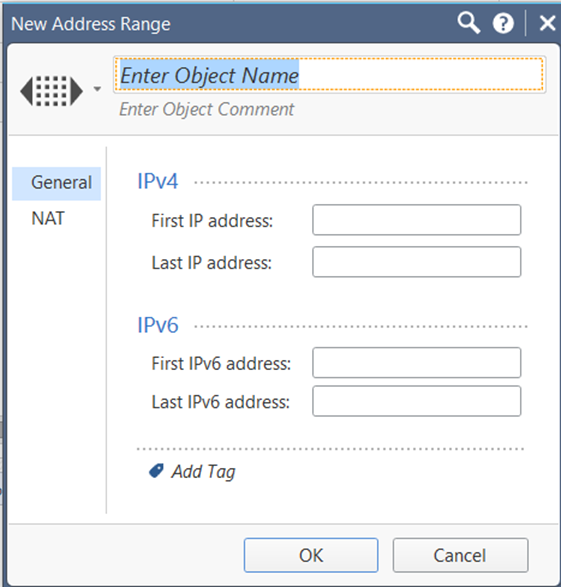
- In the Enter Object Name field, type DDEI.
- In First IP address, type the Deep Discovery Email Inspector IP address.
- In Last IP address, type the Deep Discovery Email Inspector IP address.
- Click OK.
- Right-click the destination.
- Select Add new items....
-
Click the new icon (
 ).
).
-
Select Address Ranges > Address Range....
The New Address Range window appears.

- In the Enter Object Name field, type CheckPoint.
- In First IP address, type the CheckPoint IP address.
- In Last IP address, type the CheckPoint IP address.
- Click OK.
-
Click Install Policy.
The following window opens.
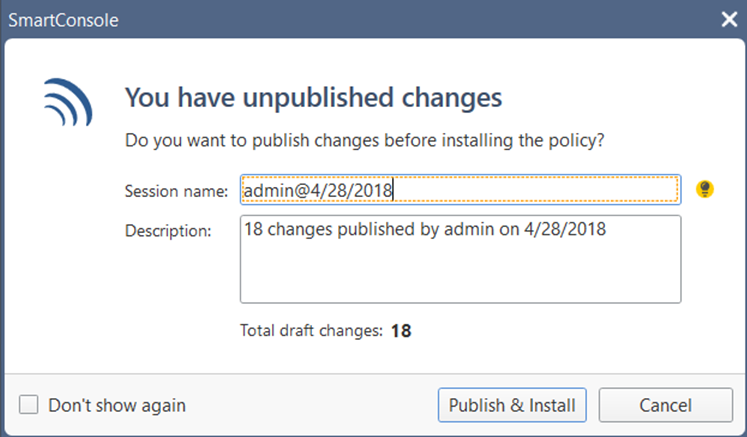
-
Click Publish & Install.
The target gateway installs.
-
Click Install.
The Check Point appliance is enabled to receive suspicious objects from Deep Discovery Email Inspector.
-
On the SECURITY POLICIES tab, go to Access Control > Policy.
-
On the Deep Discovery Email
Inspector
management console, configure the following criteria to send suspicious object
information from Deep Discovery Email
Inspector to this product/service:
-
Object type:
-
Suspicious Object
-
IPv4 address
-
-
-
Risk level:
-
High only
-
High and medium
-
High, medium, and low
-
-
-
Under Advanced Settings, click one of the following
actions:
-
Reject: Packets will be rejected and a notification sent to the communicating peer that the packet has been rejected.
-
Drop: Packets will be dropped without sending the communicating peer a notification.
-
Notify: A notification about the defined activity will be sent but the activity will not be blocked.
-
- Click Save.
- (Optional) Click Distribute Now to distribute suspicious objects to Check Point immediately.
-
To view suspicious objects distributed by Deep Discovery Email
Inspector on Check Point
SmartView Monitor, do the following:
- On Check Point SmartConsole, go to Logs & Monitor.
-
Add a new tab.
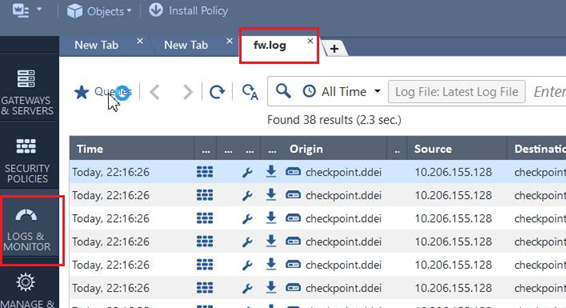
- Click Tunnels & User Monitoring to open SmartView Monitor.
-
Click the Launch Menu icon and go to Tools > Suspicious Activity Rules.
The Enforced Suspicious Activity Rules window opens.
-
At Show On, select the target Check Point
appliance name.
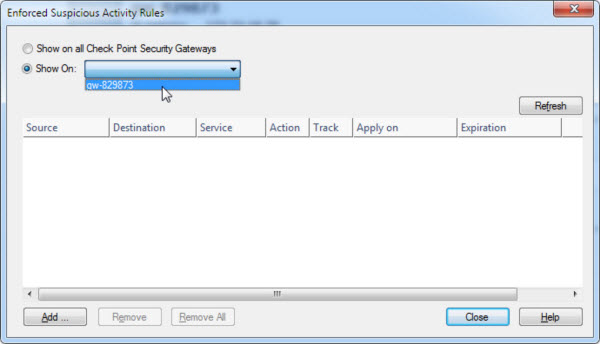
- Click Refresh.
Suspicious objects distributed by Deep Discovery Email Inspector are displayed.
Views:

