The following diagram shows the components in a cluster environment to illustrate
the data flow and to explain how each component is used within the clusters.
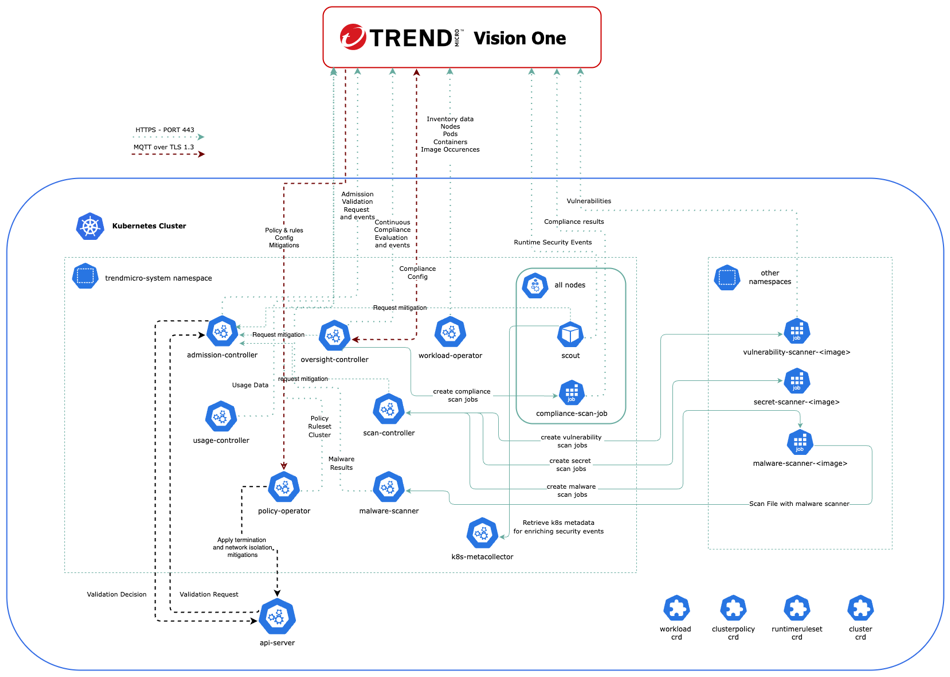
The following tables provide brief descriptions of the components that make up Kubernetes
clusters in Container Security.
NoteAdd ports to your firewall or network policy allow lists. This allows Container Security
to post component information from clusters to the backend, like health checks and
metrics, and to implement features that require communication among in-cluster components.
|
Default components
|
Component name
|
Description
|
Pod name
|
Container names
|
Ports | ||||
|
Usage Controller
|
Usage Controller regularly reports usage data which is used for Cloud One billing
and for determining installed helm versions.
|
trendmicro-usage-controller-xxxxxxxxxx-xxxxx
|
|
|
||||
|
Admission Controller
|
Admission Controller is used to validate Kubernetes and to perform block or log actions
based on deployment policy.
|
trendmicro-admission-controller-xxxxxxxxxx-xxxxx
|
|
|
||||
|
Oversight Controller
|
The Oversight Controller component repeatedly scans Kubernetes resources against continuous
policy and handles isolation and termination actions. Used for continuous compliance
policy enforcement.
|
trendmicro-oversight-controller-xxxxxxxxx-xxxxx
|
|
|
||||
|
Workload Operator
|
The Workload Operator component detects unique, running container images for the runtime
scanning feature and also collects Kubernetes resource data for the Inventory feature.
|
trendmicro-workload-operator-xxxxxxxxxx-xxxxx
|
|
|||||
|
Policy Operator
|
The Policy Operator manages the lifecycle of Container Security resources like clusters,
policies, and custom rulesets. The Policy Operator also keeps these resources in sync
with Vision One and handles authentication token rotation. Other TrendAI™ components contact the Policy Operator to get the policy and to request to apply
mitigations.
|
trendmicro-policy-operator-xxxxxxxxxx-xxxxx
|
|
|
Runtime security components
|
Component name
|
Description
|
Pod name
|
Container names
|
Ports | ||
|
Scout
|
Scout provides a runtime security feature, controls runtime rules, and handles event
aggregation and uploads. A deamonset is deployed per node.
|
trendmicro-scout-xxxxx
|
|
|||
|
K8s-metacollector
|
The k8s-metacollector fetches the metadata from the API server for various Kubernetes
resources and transmits the metadata to the in-cluster components, like Falco instances,
to decrease the performance impact to Kubernetes API server.
|
trendmicro-metacollector-xxxxxxxxxx-xxxxx
|
|
|
||
|
fargate-injector
|
The fargate-injector component injects scout and falco sidecar containers into a pod
running in an EKS Fargate environment.
|
trendmicro-fargate-injector
|
|
|
Vulnerability scanning components
|
Component name
|
Description
|
Pod name
|
Container names
|
Ports | ||
|
Scan Manager
|
Scan Manager manages in-cluster vulnerability scans and starts Scan Jobs.
|
trendmicro-scan-manager-xxxxxxxx-xxxxx
|
|
|
||
|
Scan Job
|
Scan Job generates SBOMs for container images and reports to Scan Manager. This pod
deploys in the target pod name-space.
|
trendmicro-scan-job-xxxxxxxxxx-xxxxx
|
|
Malware scanning components
|
Component name
|
Description
|
Pod name
|
Container names
|
Ports |
|
Malware scanner
|
Malware scanner provides an in-cluster malware scanning capability to analyze files.
|
trendmicro-malware-scanner-xxxxxxxxxx-xxxxx
|
|
|
Secret scanning components
|
Component name
|
Description
|
Pod name
|
Container names
|
Ports | ||
|
Scan Manager
|
Scan Manager manages in-cluster secret scans and starts Scan Jobs.
|
trendmicro-scan-manager-xxxxxxxx-xxxxx
|
|
|
||
|
Scan Job
|
Scans all files in container images (excluding user-defined paths) for secrets. Findings
are reported to the Scan Manager. This pod is deployed within the target namespace.
|
trendmicro-scan-job-sec-scanner-xxxxxxxxxx-xxxxx
|
scan-job
|
|||
|
Scout
|
Responsible for "delta" secret scans of running pods. It identifies files created
after deployment and scans them for secrets, reporting findings directly to the backend.
|
trendmicro-scout-xxxxxxxx-xxxxx
|
scout, falco
|
FIM components
|
Component name
|
Description
|
Pod name
|
Container names
|
Ports | ||
|
Scout
|
Responsible for the file integrity monitoring feature, including detections in the
container lifecycle, building the baseline, scanning files for changes, and reporting
changes to the backend.
|
trendmicro-scout-xxxxxxxx-xxxxx
|
scout
|
|


