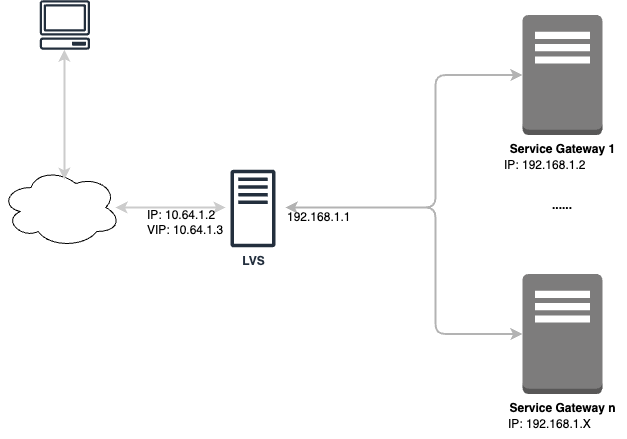
Configure and deploy Linux Virtual Server (LVS) as your load balancer to support using multiple Internet Access on-premises gateways as the authentication proxy for single sign-on.
Linux supports network address translation (NAT) and full network address translation
including source and destination (full NAT) modes for use as an authentication proxy.
Note
|
Procedure
- To set up your LVS to operate in NAT mode:

Important
When operating in NAT mode, the LVS only performs destination network address translation (DNAT) when sending packets to upstream servers, so the LVS must be the gateway to all connected on-premises gateways.- Install Keepalived to provide load balancing functionality to your LVS.
- Edit the Keepalived config file at
/etc/keepalived/keepalived.confand create a block forvirtual_server.virtual_server <IP> <port> { delay_loop <loop> lb_algo <lb_algo> lb_kind NAT persistent_timeout <persistent_timeout> protocol TCP real_server <IP 1> <port 1> { weight <weight 1> } real_server <IP 2> <port 2> { weight <weight 2> } ... } - Specify the values from the table below in the placeholder fields in order to complete
the configuration.FieldValueIPThe IP address of the load balancer to be accessed by clients. It can be the load balancer’s IP or a virtual IP.Port
The listening port on the load balancer used as the authentication proxy lb_algoChoose from:-
rr: Round robin -
wrr: Weighted round robin -
lc: Least connection -
wlc: Weighted least connection -
sh: Source hash -
dh: Destination hash -
lblc: Locality-based least connection

Important
If not usingshordh, you must set a value for the persistence_timeout field in order to make connections persistent.lb_kindNATPersistence_timeout (optional)Required if the value for lb_algo is notshordhSpecify a timeout value (in seconds) for persistent connections.ProtocolTCPIP (1, 2, 3, … )The IP addresses of the Service Gateways with Internet Access on-premises gateways installedPort (1, 2, 3, … )The listening ports on the Service Gateways used for the authentication proxyWeightThe weight to be used for load balancing decisionsBelow is an example configuration with one virtual server listening on port 10000. The load balancing algorithm is round robin working in NAT mode. The persistence timeout is 10 seconds. Two upstream Service Gateways are connected: one is at 192.168.1.100, listening on 8089, and the other is at 192.168.1.101 listening at 18089.virtual_server 10.64.1.2 10000 { delay_loop 20 lb_algo rr lb_kind NAT persistent_timeout 10 protocol TCP real_server 192.168.1.100 8089 { weight 1 } real_server 192.168.1.101 18089 { weight 1 } } -
- (Optional) To set up your LVS to run in full NAT mode, perform the following additional
configuration steps:

Important
When operating in full NAT mode, the LVS performs both DNAT and SNAT when sending packets to upstream servers, so it does not need to serve as the gateway for all connected on-premises gateways.- Configure the following rules in iptables for use with NAT, where the IP field is
the IP address to be accessed by clients, and the port field is the listening port
on the load balancer used as the authentication proxy.
iptables -t nat -I PREROUTING -d <IP> <port> -j MARK --set-xmark 0x4000/0x4000 iptables -t nat -I POSTROUTING -m mark --mark 0x4000/0x4000 -j MASQUERADE
- Use the following command to enable conntrack for IPVS.
sysctl net.ipv4.vs.conntrack=1
- Use the following command to enable IP forwarding.
sysctl net.ipv4.ip_forward=1
- Configure the following rules in iptables for use with NAT, where the IP field is
the IP address to be accessed by clients, and the port field is the listening port
on the load balancer used as the authentication proxy.