Trend Cloud One uses role-based access control (RBAC) to restrict user permissions
to parts of the services. Access rights and editing privileges are attached to roles
and not to users. You should create individual accounts for each user and assign each
user a role that restricts their activities to those necessary for the completion
of their duties. To change the access rights and editing privileges of an individual
user, you must assign a different role to the user or edit the role.
Note that these settings are also supported by Trend Cloud One - File Storage Security
and Trend Cloud One - Container Security.
The access that roles have to computers and policies can be restricted to subsets
of computers and policies. For example, users can be permitted to view all existing
computers, but only permitted to modify those in a particular group.
Trend Cloud One comes preconfigured with five roles:
-
Full Access: The full access role grants the user all possible privileges in terms of managing the Trend Cloud One services including creating, editing, and deleting resources, policies, rules, managing users and roles, and others.
-
Auditor: The auditor role gives the user the ability to view all the information in the Trend Cloud One services, but without the ability to make any modifications except to their own personal settings, such as password, contact information, dashboard layout preferences, and others.
-
Workload Security Read Only: This role has the same settings as the Auditor role, but this role cannot be modified. The Read Only role for new Trend Cloud One accounts is mapped to this role in Workload Security.
-
Deep Security Migration: Role used by Deep Security software for migration to Workload Security. For details, see the Deep Security help.
-
Trend Vision One: Role used by Trend Vision One.
Currently, custom roles are only supported for Trend Cloud One - Endpoint & Workload
Security. A custom role for Workload Security is treated as the auditor role when
the user is accessing any other Trend Cloud One service.
Custom Workload Security rights
Depending on the level of access granted, controls in Workload Security are either
visible and changeable, visible but disabled, or hidden. For a list of the rights
granted in the preconfigured roles, as well as the default rights settings when creating
a new role, see Default settings for full access, auditor, and new roles.
You can create new roles that can restrict users from editing or even seeing Workload
Security objects such as specific computers, the properties of security rules, or
the system settings.
Before creating user accounts, identify the roles that your users will take and itemize
what Workload Security objects those roles require access to and what the nature of
that access is (viewing, editing, creating, and so on). Once you have created your
roles, you can then begin creating user accounts and assigning them specific roles.
Do not create a new role by duplicating and then modifying the full access role. To
ensure that a new role only grants the rights you intend, create the new role by clicking
New in the toolbar. The rights for a new role are set at the most restrictive settings
by default. You can then proceed to grant only the rights that are required. If you
duplicate the full access role and then apply restrictions, you risk granting some
rights that you did not intend.
Clicking New ( ) or Properties (
) or Properties ( ) displays the Role properties window with six tabs: General, Computer Rights, Policy Rights, User Rights, Other Rights, and Assigned To.
) displays the Role properties window with six tabs: General, Computer Rights, Policy Rights, User Rights, Other Rights, and Assigned To.
 ) or Properties (
) or Properties ( ) displays the Role properties window with six tabs: General, Computer Rights, Policy Rights, User Rights, Other Rights, and Assigned To.
) displays the Role properties window with six tabs: General, Computer Rights, Policy Rights, User Rights, Other Rights, and Assigned To.Add or edit a role
-
From the Trend Cloud One - Endpoint & Workload Security page, click .
-
Click New to add a new role or double-click an existing role to edit its settings.
-
Specify the general properties for the role, including:
- Name: The name of the role, which appears on the Roles page and in the list of available roles when adding a user.
- Description: An optional description of the role.
- Access Type: Select whether users with this role have access to the Deep Security Manager User Interface or the Web Service API.
-
Use the Computer Rights tab to set viewing, editing, deleting, alert-dismissal, and event tagging rights for users in a role. These rights can apply to all computers and computer groups or they can be restricted to only certain computers.
-
To restrict access, select Selected Computers and select the computer groups and computers to which users in this role have access. These rights restrictions affect not only the user's access to computers in Workload Security, but also what information is visible, including events and alerts. In addition, email notifications are only sent if they relate to data to which the user has access rights.
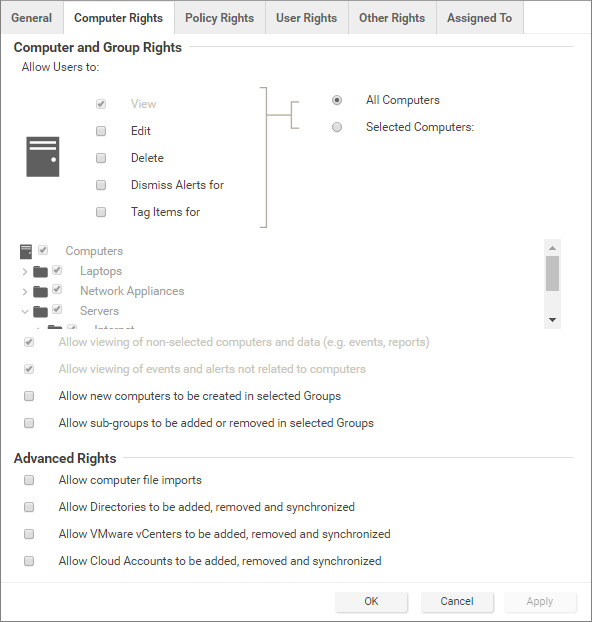 Four basic options are available:
Four basic options are available:-
Allow viewing of non-selected computers and data: If users in this role have restricted edit, delete, or dismiss alerts rights, you can still allow them to view, but not change, information about other computers by selecting it.
-
Allow viewing of events and alerts not related to computers: Set this option to allow users in this role to view non-computer-related information (for example, system events like users being locked out, new firewall rules being created, IP Lists being deleted, and so on).The previous two options affect the data to which users have access. Although the ability of a user to make changes to computers have been restricted, the preceding two settings control whether the users can see information relating to computers they do not otherwise have access to. This includes receiving email notifications related to those computers.
-
Allow new computers to be created in selected Groups: Set this option to allow users in this role to create new computers in the computer groups to which they have access.
-
Allow sub-groups to be added/removed in selected Groups: Set this option to allow users in this role to create and delete subgroups within the computer groups to which they have access.
You can also enabled the following in the Advanced Rights section:- Allow computer file imports: Allow users in this role to import computers using files created using Workload Security's Computer Export option.
- Allow Directories to be added, removed and synchronized: Allow users in this role to add, remove, and synchronize computers that are being managed using an LDAP-based directory like Microsoft Active Directory.
- Allow VMware vCenters to be added, removed and synchronized: Allow users in this role to add, remove and synchronize VMware vCenters.
-
-
Use the Policy Rights tab to assign viewing, editing, and deleting rights to users in a role. These rights can apply to all policies or they can be restricted to only certain policies. If you wish to restrict access, click Selected Policies and select the policies to which users in this role have access.
 When you allow rights to a policy that has child policies, users automatically get rights to the child policies as well.Two basic options are available:
When you allow rights to a policy that has child policies, users automatically get rights to the child policies as well.Two basic options are available:- Allow viewing of non-selected Policies: If users in this role have restricted edit or delete rights, you can still allow them to view, but not change information about other policies by making this selection.
- Allow new Policies to be created: Set this option to allow users in this role to create new policies.
You can also enable this in the Advanced Rights section:- Allow Policy imports: Allow users in this role to import policies using files created with Workload Security Export option on the Policies tab.
-
The options on the User Rights tab allow you to define permissions for administrator accounts.
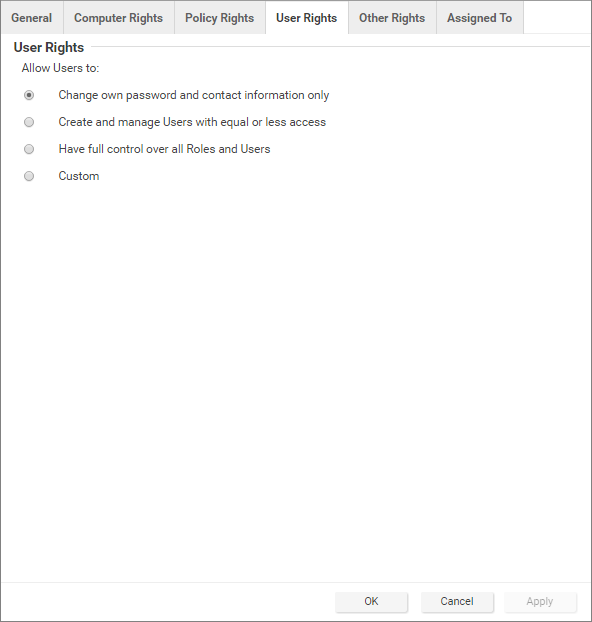
-
Change own password and contact information only: Users in this role can change their own password and contact information only.
-
Create and manage Users with equal or less access: Users in this role can create and manage any users who do not have any privileges greater than theirs. If there is even a single privilege that exceeds those of the users with this role, the users with this role cannot create or manage them.
-
Have full control over all Roles and Users: Gives users in this role the ability to create and edit and users or roles without restrictions. Be careful when using this option: if you assign it to a role, you may give a user with otherwise restricted privileges the ability to create and then sign in as a user with full unrestricted access to all aspects of Workload Security.
-
Custom: You can further restrict the ability of a user to view, create, edit, or delete users and roles by selecting Custom and using the options in the Custom Rights section. Some options may be restricted for certain users if the Can only manipulate Users with equal or lesser rights option is selected.The Can only manipulate Users with equal or lesser rights option limits the authority of users in this role. They can only make changes to users that have equal or lesser rights than themselves. Users in this role cannot create, edit, or delete roles. Selecting this option also places restrictions on some of the options in the Custom Rights section:
- Can Create New Users: Can only create users with equal or lesser rights.
- Can Edit User Properties: Can only edit a user (or set or reset password) with equal or lesser rights.
- Can Delete Users: Can only delete users with equal or lesser rights.
-
-
The Other Rights tab enables you to restrict roles' permissions so that they can only access specific Workload Security features, and sometimes specific actions with those features. This can be useful if, for example, you have a team of administrators, and you want to make sure that they do not accidentally overwrite each others' work. By default, roles are View Only or Hide for each feature. To allow to full control or customized access, select Custom from the list.
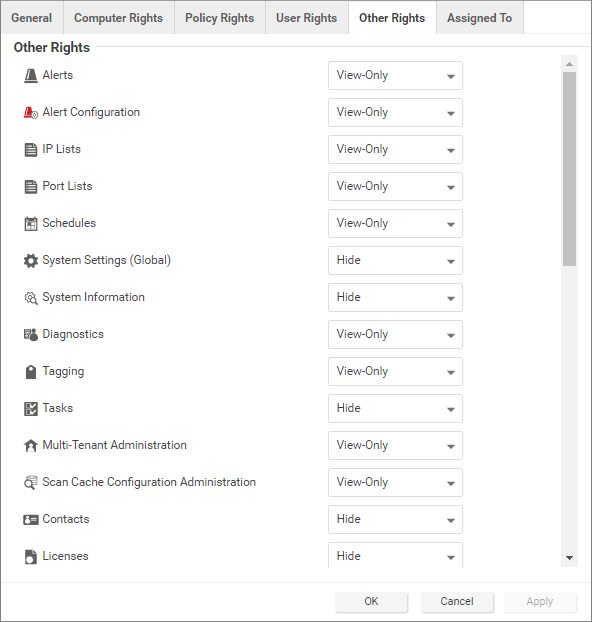
-
The Assigned To tab displays a list of the users who have been assigned this role. If you want to test that roles are working correctly, sign in as a newly created user and verify the functionality.
Default settings for full access, auditor, and new roles
The following table identifies the default rights settings for the full access role
and the auditor role. Also listed are the rights settings that are in place when creating
a new role by clicking New in the toolbar on the Roles page.
|
RIGHTS
|
SETTINGS BY ROLE
|
||
|
General
|
Full Access Role
|
Auditor/Workload Security Read Only Role
|
New Role Defaults
|
|
Allow Access to Workload Security Manager User Interface
|
Allowed
|
Allowed
|
Allowed
|
|
Allow Access to web services API
|
Allowed
|
Allowed
|
Not allowed
|
|
General
|
Full Access Role
|
Auditor/Workload Security Read Only Role
|
New Role Defaults
|
|
View
|
Allowed, All Computers
|
Allowed, All Computers
|
Allowed, All Computers
|
|
Edit
|
Allowed, All Computers
|
Not allowed, All Computers
|
Not allowed, All Computers
|
|
Delete
|
Allowed, All Computers
|
Not allowed, All Computers
|
Not allowed, All Computers
|
|
Dismiss Alerts for
|
Allowed, All Computers
|
Not allowed, All Computers
|
Not allowed, All Computers
|
|
Tag Items for
|
Allowed, All Computers
|
Not allowed, All Computers
|
Not allowed, All Computers
|
|
Allow viewing of non-selected computers and data (for example, events, reports)
|
Allowed
|
Allowed
|
Allowed
|
|
Allow viewing of events and alerts not related to computers
|
Allowed
|
Allowed
|
Allowed
|
|
Allow new computers to be created in selected Groups
|
Allowed
|
Not allowed
|
Not allowed
|
|
Allow sub-groups to be added or removed in selected Groups
|
Allowed
|
Not allowed
|
Not allowed
|
|
Allow computer file imports
|
Allowed
|
Not allowed
|
Not allowed
|
|
Allow VMware vCenters to be added, removed, and synchronized
|
Allowed
|
Not allowed
|
Not allowed
|
|
Allow Cloud Accounts to be added, removed and synchronized
|
Allowed
|
Not allowed
|
Not allowed
|
|
Policy Rights
|
Full Access Role
|
Auditor/Workload Security Read Only Role
|
New Role Defaults
|
|
View
|
Allowed, All Policies
|
Allowed, All Policies
|
Allowed, All Policies
|
|
Edit
|
Allowed, All Policies
|
Not allowed, All Policies
|
Not allowed, All Policies
|
|
Delete
|
Allowed, All Policies
|
Not allowed, All Policies
|
Not allowed, All Policies
|
|
Allow viewing of non-selected Policies
|
Allowed
|
Allowed
|
Allowed
|
|
Allow new Policies to be created
|
Allowed
|
Not allowed
|
Not allowed
|
|
Allow Policy imports
|
Allowed
|
Not allowed
|
Not allowed
|
|
User and APIKey Rights (See note on User rights below)
|
Full Access Role
|
Auditor/Workload Security Read Only Role
|
New Role Defaults
|
|
Change own password and contact information only
|
Yes
|
Yes
|
|
|
Create and manage Users with equal or less access
|
|||
|
Create and manage Users and APIkeys with equal or less access
|
|||
|
Have full control over all Roles and Users
|
Yes
|
||
|
Custom
|
|||
|
Other Rights
|
Full Access Role
|
Auditor/Workload Security Read Only Role
|
New Role Defaults
|
|
Scan Cache Configuration Administration
|
Full
|
View-Only
|
View-Only
|
|
Agent Version Controls
|
Full
|
View-Only
|
View-Only
|
|
Data Center Gateways
|
Full (can Create, View, Edit, or Delete Data Center Gateways)
|
Hide
|
Hide
|
|
Alerts
|
Full (can Dismiss Global Alerts)
|
View-Only
|
View-Only
|
|
Alert Configuration
|
Full (can Edit Alert Configurations)
|
View-Only
|
View-Only
|
|
IP Lists
|
Full (can Create, Edit, Delete)
|
View-Only
|
View-Only
|
|
Port Lists
|
Full (can Create, Edit, Delete)
|
View-Only
|
View-Only
|
|
Schedules
|
Full (can Create, Edit, Delete)
|
View-Only
|
View-Only
|
|
System Settings (Global)
|
Full (can View, Edit System Settings (Global))
|
Hide
|
Hide
|
|
Expert Settings
|
Full
|
Hide
|
Hide
|
|
System Information
|
Full
|
Hide
|
Hide
|
|
Diagnostics
|
Full (can Create Diagnostic Packages)
|
View-Only
|
View-Only
|
|
Tagging
|
Full (can Tag (Items not belonging to Computers), can Delete Tags, can Update Non-Owned
Auto-Tag Rules, can Run Non-Owned Auto-Tag Rules, can Delete Non-Owned Auto-Tag Rules)
|
View-Only
|
View-Only
|
|
Tasks
|
Full (can View, Add, Edit, Delete Tasks, Execute Tasks)
|
Hide
|
Hide
|
|
Contacts
|
Full (can View, Create, Edit, Delete Contacts)
|
Hide
|
Hide
|
|
Licenses
|
Full (can View, Change License)
|
Hide
|
Hide
|
|
Updates
|
Full (can Add, Edit, Delete Software; can View Update For Components; can Download,
Import, Apply Update Components; can Delete Deep Security Rule Updates)
|
Hide
|
Hide
|
|
Asset Values
|
Full (can Create, Edit, Delete Asset Values)
|
View-Only
|
View-Only
|
|
Certificates
|
Full (can Create, Delete SSL Certificates)
|
View-Only
|
View-Only
|
|
Relay Management
|
Full
|
View-Only
|
View-Only
|
|
Proxy
|
Full
|
View-Only
|
View-Only
|
|
Syslog Configurations
|
Full
|
View-Only
|
View-Only
|
|
USB Device
|
Full (can Create, Edit, Delete)
|
View-Only
|
View-Only
|
|
Malware Scan Configuration
|
Full (can Create, Edit, Delete Malware Scan Configuration)
|
View-Only
|
View-Only
|
|
Identified File
|
Full (can Delete, Download Identified File)
|
View-Only
|
View-Only
|
|
Web Reputation Configuration
|
Full
|
View-Only
|
View-Only
|
|
Activity Monitoring Configuration
|
Full
|
View-Only
|
View-Only
|
|
Directory Lists
|
Full (can Create, Edit, Delete)
|
View-Only
|
View-Only
|
|
File Lists
|
Full (can Create, Edit, Delete)
|
View-Only
|
View-Only
|
|
File Extension Lists
|
Full (can Create, Edit, Delete)
|
View-Only
|
View-Only
|
|
Application Control Rulesets
|
Full (can Create, View, Edit, or Delete Application Control rulesets)
|
Hide
|
Hide
|
|
Application Control Rule
|
Full (can Create, View, Edit, or Delete Application Control rules)
|
Hide
|
Hide
|
|
Application Control Unrecognized Software
|
Full (can View or Allow/Block unrecognized software)
|
Hide
|
Hide
|
|
Application Control Software Inventory
|
Full (can Create, View, or Delete software inventory)
|
Hide
|
Hide
|
|
Integrity Monitoring Rules
|
Full (can Create, Edit, Delete)
|
View-Only
|
View-Only
|
|
Log Inspection Rules
|
Full (can Create, Edit, Delete)
|
View-Only
|
View-Only
|
|
Log Inspection Decoders
|
Full (can Create, Edit, Delete)
|
View-Only
|
View-Only
|
|
Firewall Rules
|
Full (can Create, Edit, Delete Firewall Rules)
|
View-Only
|
View-Only
|
|
Firewall Stateful Configurations
|
Full (can Create, Edit, Delete Firewall Stateful Configurations)
|
View-Only
|
View-Only
|
|
Intrusion Prevention Rules
|
Full (can Create, Edit, Delete)
|
View-Only
|
View-Only
|
|
Application Types
|
Full (can Create, Edit, Delete)
|
View-Only
|
View-Only
|
|
MAC Lists
|
Full (can Create, Edit, Delete)
|
View-Only
|
View-Only
|
|
Contexts
|
Full (can Create, Edit, Delete)
|
View-Only
|
View-Only
|
|
Tenant Account
|
Full
|
Hide
|
Hide
|
The settings corresponding to the Change own password and contact information only option are listed in the following table:
|
Settings for Change own password and contact information only
|
|
|
Users
|
|
|
Can View Users
|
Not allowed
|
|
Can Create New Users
|
Not allowed
|
|
Can Edit User Properties (User can always edit select properties of own account)
|
Not allowed
|
|
Can Delete Users
|
Not allowed
|
|
Roles
|
|
|
Can View Roles
|
Not allowed
|
|
Can Create New Roles
|
Not allowed
|
|
Can Edit Role Properties (Warning: conferring this right lets Users with this Role
edit their own rights)
|
Not allowed
|
|
Can Delete Roles
|
Not allowed
|
|
Delegate Authority
|
|
|
Can only manipulate Users with equal or lesser rights
|
Not allowed
|
The settings corresponding to the Create and manage Users with equal or less access option are listed in the following table:
|
Settings for Create and manage Users with equal or less access
|
|
|
Users
|
|
|
Can View Users
|
Allowed
|
|
Can Create New Users
|
Allowed
|
|
Can Edit User Properties (User can always edit select properties of own account)
|
Allowed
|
|
Can Delete Users
|
Allowed
|
|
Roles
|
|
|
Can View Roles
|
Not allowed
|
|
Can Create New Roles
|
Not allowed
|
|
Can Edit Role Properties (Warning: conferring this right lets Users with this Role
edit their own rights)
|
Not allowed
|
|
Can Delete Roles
|
Not allowed
|
|
Delegate Authority
|
|
|
Can only manipulate Users with equal or lesser rights
|
Allowed
|
The settings corresponding to the Have full control over all Roles and Users option are listed in the following table:
|
Settings for "Have full control over all Roles and Users
|
|
|
Users
|
|
|
Can View Users
|
Allowed
|
|
Can Create New Users
|
Allowed
|
|
Can Edit User Properties (User can always edit select properties of own account)
|
Allowed
|
|
Can Delete Users
|
Allowed
|
|
Roles
|
|
|
Can View Roles
|
Allowed
|
|
Can Create New Roles
|
Allowed
|
|
Can Edit Role Properties (Warning: conferring this right will let Users with this
Role edit their own rights)
|
Allowed
|
|
Can Delete Roles
|
Allowed
|
|
Delegate Authority
|
|
|
Can only manipulate Users with equal or lesser rights
|
Not applicable
|


