Types of updates from Trend Micro include:
-
Security updates: Rules and malware patterns that agent software uses to identify potential threats. Types of security updates include:
-
Pattern updates: Used by Anti-Malware.
-
Rule updates: Used by:
-
Firewall
-
Intrusion Prevention
-
Integrity Monitoring
-
Log Inspection
-
-
Note that Application Control rule updates are created locally, based on your computers'
software. They are not from Trend Micro.
Trend Micro releases new rule updates every Tuesday, with additional updates as new
threats are discovered. Information about the updates is available in the Trend Micro
Threat Encyclopedia.
Workload Security checks for software upgrades
Updated agent software packages are automatically imported into Workload Security
and appear on .
Workload Security only informs you of minor version updates of software. For example,
if you have agent version 9.6.100, and Trend Micro releases 9.6.200, an alert notifies
you that software updates are available. However, if 10.0.nnn (a major version difference)
is released and you do not have any 10.0 agents, the alert does not appear (even though
10.0 is later than 9.6.100).
Best practices for upgrades
When deploying a new release of the agent:
- Relays must be the same version or newer than all agents in your environment. The relays provided as part of Workload Security are kept up to date and compatible with the latest available agents. However, if you have deployed your own relays, always upgrade them before upgrading your agents.
- Workload Security customers can ignore the Minimum DSM Version for agents. Trend Micro hosts and updates the manager as part of the service, and it is always compatible with the latest available agents.
Workload Security validation of update integrity
Both software updates and security updates are digitally signed. In addition to automatic
checks, if you want to manually validate the signatures or checksums, you can use
the following external tools:
- sha256sum (Linux)
- Checksum Calculator (Windows)
- jarsigner (Java Development Kit (JDK), see Check digital signatures on software packages)
Digital signatures
When security updates are viewed or used, Workload Security validates the signature.
A correct digital signature indicates that the software is authentically from Trend
Micro and has not been corrupted or tampered with. If the digital signature is invalid,
Workload Security does not use the file. A warning is also recorded in log files such
as
server0.log:WARNING: ThID:85|TID:0|TNAME:Primary|UID:1|UNAME:MasterAdmin|Verifying the signature
failed.com.thirdbrigade.manager.core.general.exceptions.FileNotSignedValidationException:
"corrupted_rules.zip." has not been digitally signed by Trend Micro and cannot be
imported.The agent also validates the digital signature, compares checksums (sometimes called
hashes or fingerprints) and uses other, non-disclosed integrity methods.
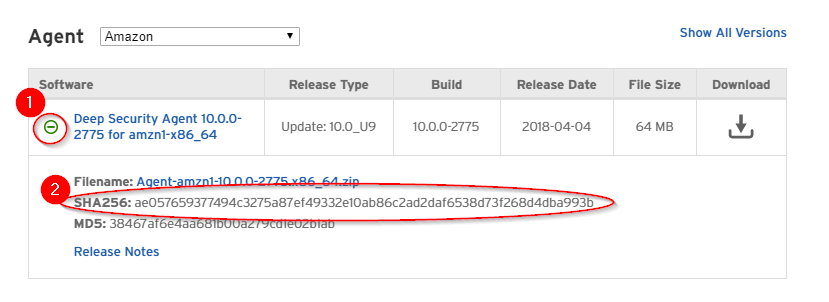
Checksums
Software checksums (also called hashes or fingerprints) are published on the Download Center. To view the SHA-256 hash, click + located to the left of the software's name.