Policies define the rules that are used to control what is allowed to run in your
Kubernetes cluster.
You will define one policy for each cluster that you want to protect, with a default
set of rules (also known as a "policy definition") that apply to the
entire cluster. If your cluster contains more than one namespace, you can also
define separate sets of rules for the namespaces. Any namespace rules take
precedence over the cluster-wide rules.
TipTo begin with, we recommend that you create a policy with log-only
rules. When you're satisfied that the policy is working as expected, change the
rules to block objects that violate the policy.
|
Define a policy for a cluster
Procedure
- Open the Trend Micro Cloud One console and select Container Security.
- Go to the
 Policies page.
Policies page. - Do one of the following:
-
If this is your first policy, click + New policy.

- If this is not your first policy, click + New.
-
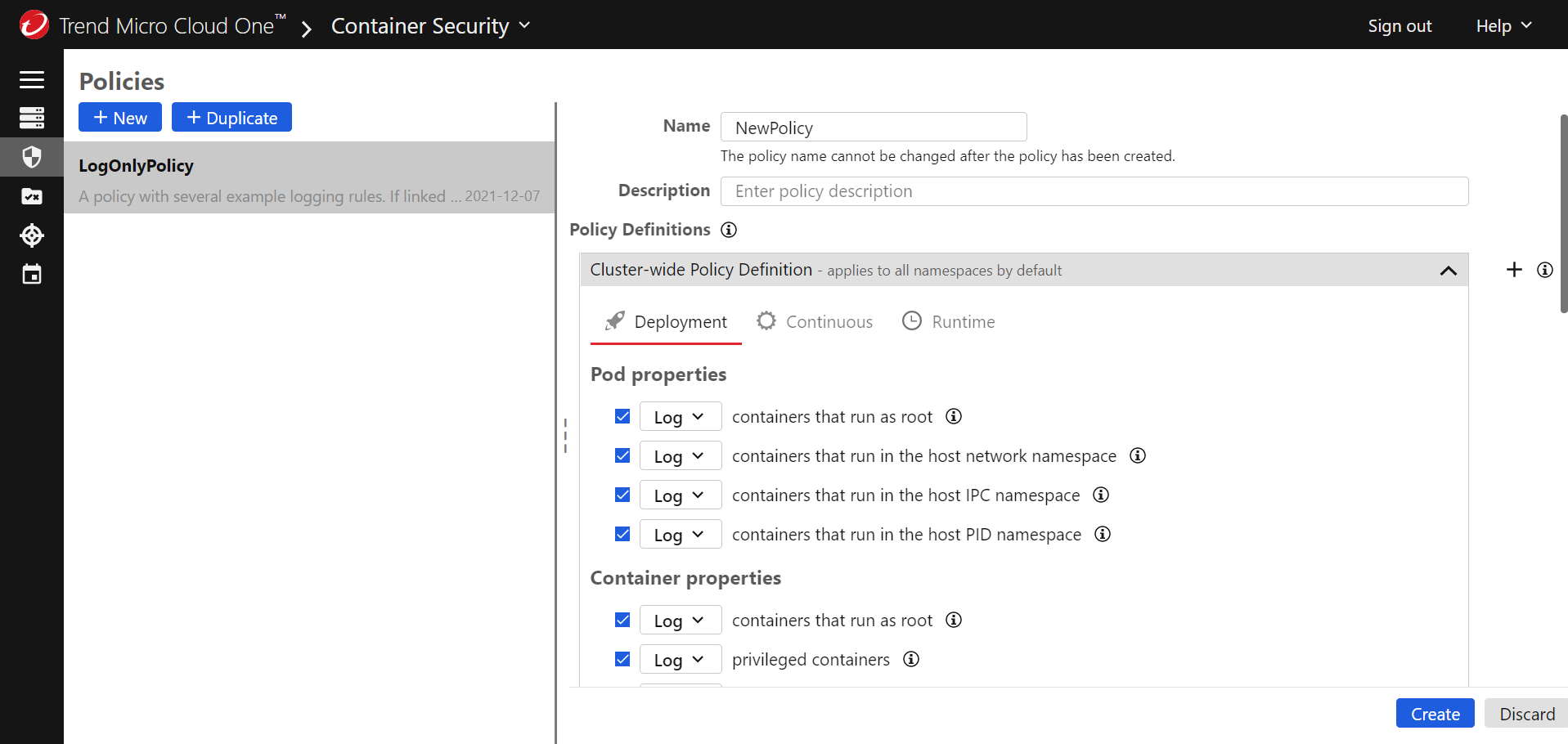
- Provide a unique Name for the policy that will help you identify its purpose, and optionally add a Description.
- In the Cluster-Wide Policy Definition area, configure the
rules that you want to enforce with this policy. There are three tabs,
corresponding to three different types of rules:
-
Deployment: These rules are enforced when an image is about to be deployed. Select the checkboxes for the rules that you want to enforce and use the drop-downs to choose what happens when a rule is violated: log an event (and allow the deployment) or block deployment.
-
Continuous: These rules are checked periodically while a pod is running. Select the checkboxes for the rules that you want to enforce and use the drop-downs to choose what happens when a rule is violated: log an event and allow the pod to keep running, isolate the pod's network traffic, or terminate the pod.
-
Runtime: On this tab, add one or more rulesets that contain rules you want to enforce while a pod is running. See Configure runtime security for information on how to enable runtime security and define a ruleset. The ruleset also defines what action Container Security takes if a pod violates any rule during runtime: log and event and allow the pod to keep running, isolate the pod's network traffic, or terminate the pod.
For details about the rules, see About the rules.Deployment and continuous rules must be deployed in specific combinations:Deployment actionsContinuous actionsloglogblocklogblockisolateblockterminateContainer Security also has a default rule. For more information, see Trusted images. -
- To finalize the policy, select Create.
Assign a policy to a cluster
NoteThis section assumes you have added a
cluster.
|
Procedure
- Go to the
 Clusters page.
Clusters page. - Select the Kubernetes cluster where you want to apply the policy.
- Select the policy from the Policy list.
- Select Save.
Add a policy definition for a namespace
If your cluster contains more than one namespace, you can create separate policy
definitions for the namespaces. The namespace policy definition takes precedence
over the cluster-wide policy definition.
Procedure
- On the
 Policies page, select the name of an existing cluster-wide
policy.
Policies page, select the name of an existing cluster-wide
policy. - In the Policy Definitions section, next to the Cluster-Wide Policy
Definition heading, select +.
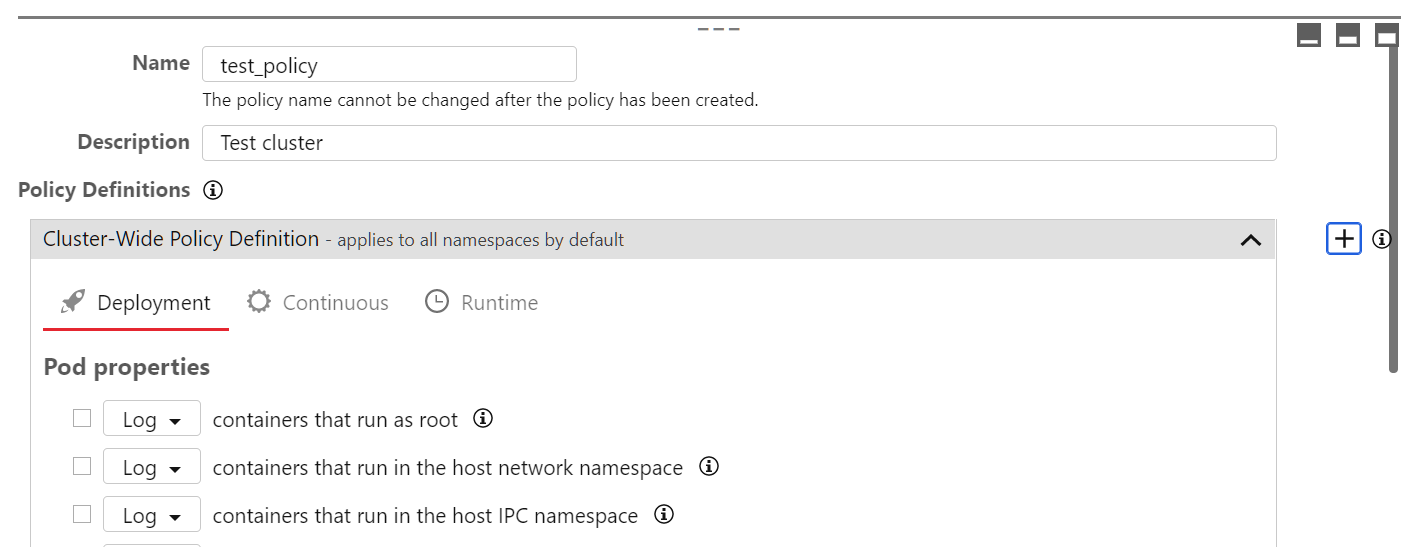
- Scroll to the bottom of the page and select
 in the new section that was added.
in the new section that was added. - Provide a unique Name for the policy that will help you identify its purpose.
- In the Namespaces area, add one or more Kubernetes namespaces that you want to protect with this new policy.
- Configure the deployment rules, continuous rules, and runtime rules as required, using the corresponding tabs. Select the checkboxes for the rules that you want to enforce and use the drop-downs to choose what happens when an object violates the rule. For information about the rules, see About the rules.
- Select Save.If you want to add another set of namespace rules, select + to add a new namespace policy definition section.
Protect a namespace
To prevent attacks via Kubernetes credentials or misconfigured role-based access
control, it is important to set up rules to log or block attempts to access
those containers with special privileges. We recommend enabling this in the
trendmicro-system namespace:
Procedure
- Create a policy for a namespace for namespaces that you want to protect.
- Enable Kubectl access rules.
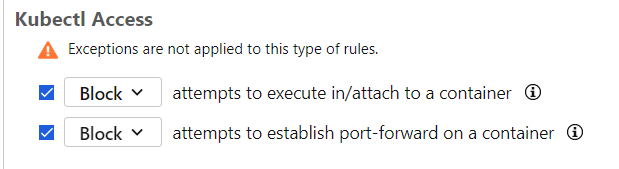
Test a policy
After you have created and configured a policy, you can use Container Security to
protect your Kubernetes cluster.
Any deployment (kubectl, helm, etc.) is reviewed by the deployment controller. In
this example, we'll attempt to deploy a privileged busybox container.
NoteThis example assumes that you selected "Block" as the action for
the privileged containers rule.
|
Procedure
- Create a file named
busybox.yamlwith the following contents:apiVersion: v1 kind: Pod metadata: name: busyboxpod labels: app: busyboxpod spec: containers: - image: busybox command: - sleep - "3600" imagePullPolicy: IfNotPresent name: busybox-container securityContext: privileged: true restartPolicy: Always

Note
In this pod definition, thesecurityContextis set toprivileged = true. The policy that we created earlier should block this pod because we set the policy to block privileged containers. - Ensure your kubectl context is set to your cluster.
- Use the following command to create the pod:
$ kubectl apply -f busybox.yaml - You should see that your request was denied:
$ kubectl apply -f busybox.yaml Error from server: error when creating "busybox.yaml": admission webhook "trendmicro-admission-controller.default.svc" denied the request: - containerSecurityContext violates rule privileged "true" in container(s) "busybox-container" (block).
- If you go to the
 Events page in the Container Security console, you'll see a
corresponding event:
Events page in the Container Security console, you'll see a
corresponding event: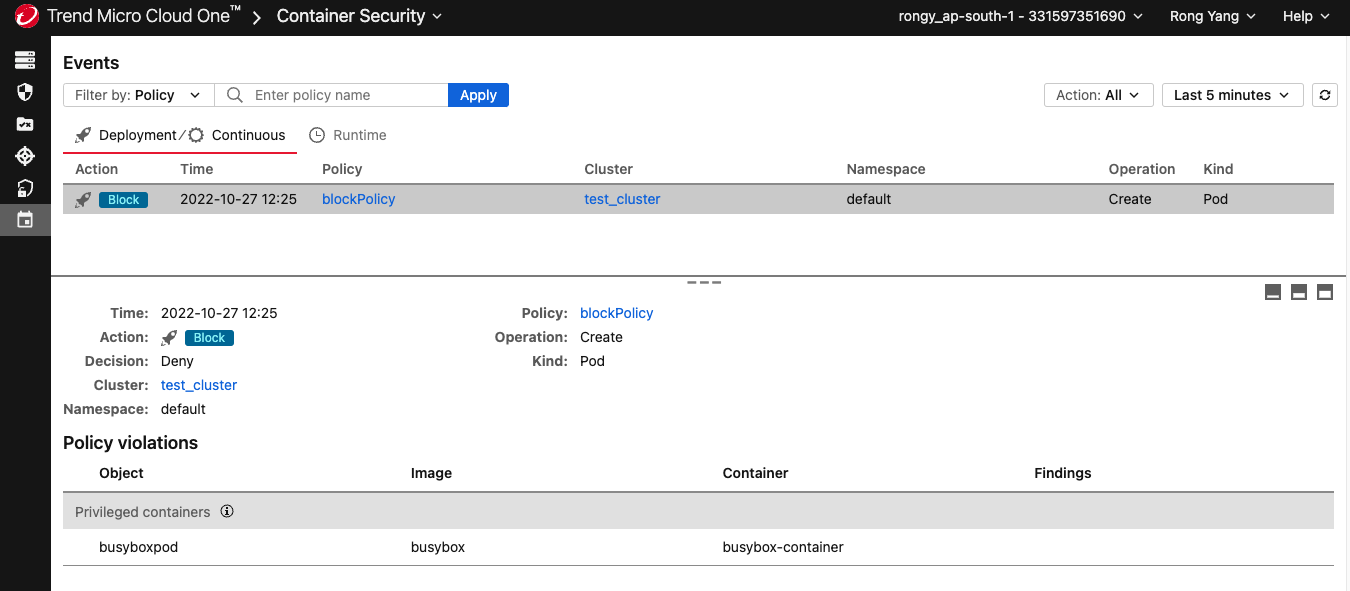
About the rules
Deployment rules
The rules on the Deployment tab are enforced when an image is about
to be deployed or an action is about to be applied. You can choose to
Log (and allow) or Block deployment based on these
rules.
|
Property
|
Description
|
|
Pod properties
|
|
|
Container properties
|
|
|
Image properties
|
|
|
Scan results
|
The following rules are supported by Trend Micro Artifact Scanner (TMAS):
|
|
Kubectl access
|
We recommend setting up a namespaced policy using these rules
to protect containers with special privileges including
Container Security.
|
|
Exceptions
|
Use the Exceptions section to add exceptions
that override the other deployment rules. For example, if
you have a deployment rule that blocks images with names
that contain "dev" but want to allow an image called
"devone", add an exception for "images with names that equal
devone".
Possible exceptions are:
|
Continuous rules
The rules on the Continuous tab are checked periodically while a pod
is running. You can choose to Log and allow it to continue running,
Isolate its network traffic, or Terminate the pod
when a rule is violated.
|
Pod properties
|
|
|
Container properties
|
|
|
Image properties
|
|
|
Exceptions
|
Use the Exceptions section to add exceptions
that override the other continuous rules. For example, if
you have a continuous rule that blocks images with names
that contain "dev" but want to allow an image called
"devone", add an exception for "images with names that equal
devone".
Possible exceptions are:
|
Runtime rules
On the Runtime tab, add one or more rulesets that contain rules you
want to enforce while a pod is running. See Configure
runtime security for information on how to enable runtime security
and define a ruleset, including how to add labels to control which pods the
rules are applied to.


