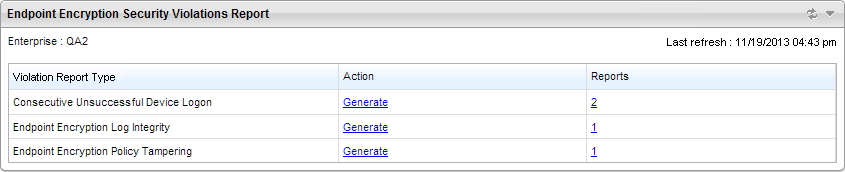
The Endpoint Encryption Security Violations
Report widget shows the security violations assessed by the following reports:
-
Endpoint Encryption Consecutive Unsuccessful Device Logon
-
Endpoint Encryption Policy Tampering
-
Endpoint Encryption Log Integrity
Generating a report gathers all security violations currently logged by PolicyServer.
Once generated, click the number on the Reports
column to view generated reports for that violation.
|
Header
|
Description
|
|
Violation report type
|
The available report types for various violations.
|
|
Action
|
Click Generate to create a new report.
|
|
Reports
|
The total number of generated reports for that violation. Click the number to view
available reports.
|
NoteTo specify the number of unsuccessful logons attempts before it is considered a security
violation, click ▼ to open the Widget Settings window, type a value in the Consecutive unsuccessful logons textbox, and then click Save.
|
Consecutive Unsuccessful Device Logon Report
The following table explains the Endpoint Encryption Consecutive Unsuccessful
Device Logon report. Use it to understand when the logon attempt occurred, the
affected Endpoint Encryption device, and how many times the
user attempted to log on to the Endpoint Encryption device.
Endpoint Encryption Consecutive Unsuccessful Device Logon Report Example
|
Entry
|
Example
|
Description
|
|
Event Timestamp
|
07/02/2012 01:56 pm
|
When the event occurred.
|
|
Device Name
|
TREND-4136D2DB3
|
The computer name used by the Endpoint Encryption
device.
|
|
Attempts
|
5
|
The number of times that a user attempted to log on to the Endpoint Encryption device.
|
Policy Tampering Report
The following table explains the Endpoint Encryption Policy Tampering
report. Use it to understand how to read the report details.
Endpoint Encryption Policy Tampering Report Example
|
Header
|
Example
|
Description
|
|
Event Timestamp
|
07/02/2012 01:56 pm
|
When the event occurred.
|
|
Event
|
Policy Value Integrity Check Failed
|
The logged event including the authentication method.
|
Log Integrity Report
The following table explains the Endpoint Encryption Log Integrity
report. Use it to understand how to read the report details.
Endpoint Encryption Log Integrity Report Example
|
Header
|
Example
|
Description
|
|
Event Timestamp
|
07/02/2012 01:56 pm
|
When the event occurred.
|
|
Event
|
Audit Log Record Missing |
The logged event including the authentication method.
|

