Procedure
- Create a new Endpoint Encryption policy.See Creating a Policy.
- Click Common.The Common policy rules settings appear.
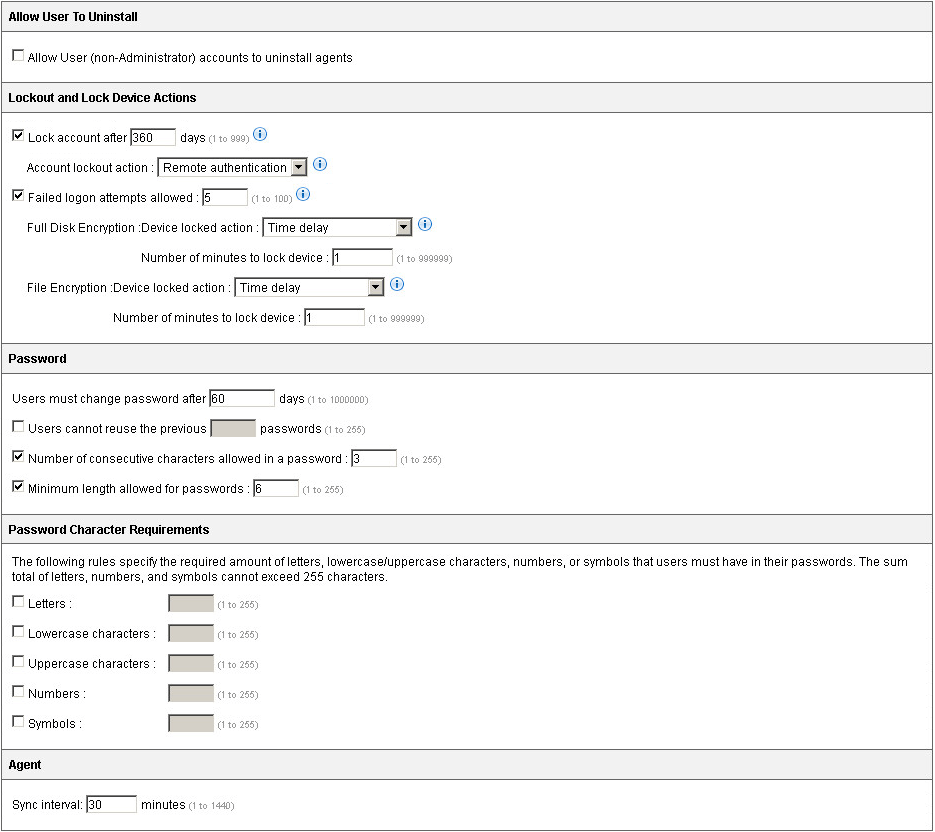
Common Policy Rules - Under Allow User to Uninstall, select Allow
User (non-administrator) accounts to uninstall agent software to
allow any Endpoint Encryption user to uninstall the
agent.

Note
By default, only Administrator accounts can uninstall Endpoint Encryption agents. - Under Lockout and Lock Device Actions, configure the
following options:
-
Select Lock account after <number> days to specify the number of days that the Endpoint Encryption device locks if it does not synchronize policies.
-
Use Account lockout action to specify whether the remote authentication or erase action occurs at lockout.

Note
For information about lock options, see Lockout Actions
-
-
Select Failed log on attempts allowed to specify how many times that a user can attempt to authenticate before the Endpoint Encryption device locks.
-
For Full Disk Encryption or File Encryption devices, separately configure the following:
-
Use Device locked action to specify whether the
Remote Authentication
or theErase
action occurs at lockout.
Note
For information about lock options, see Lockout Actions -
Use Number of minutes to lock device to specify the duration that time delay locks the Endpoint Encryption device from authentication
-
-
- Under Password, configure the following options:
-
Select Users must change password after <number> days to control when a user is prompted to update password.
-
Select Users cannot reuse the previous <number> passwords to specify how many previous passwords the user may reuse.
-
Select Number of consecutive characters allowed in a password to specify how many repeated characters a user may specify in the password.
-
Select Minimum length allowed for passwords to specify how many characters the user is required to use in the password.
-
- Under Password Requirements, specify the password
character limitations.
-
Letters
-
Lowercase characters
-
Uppercase characters
-
Numbers
-
Symbols

Important
The sum total of letters, numbers, and symbols cannot exceed 255 characters. -
- Under Agent, specify the Sync internal in minutes.
Lockout Actions
Some
policies have settings to lock out a user account or to lock a device based on certain
criteria. Account lockout and device lockout actions affect the Endpoint Encryption device whether or not the agent synchronizes
policies with PolicyServer. For example, if the Endpoint Encryption agent does not communicate with PolicyServer
for a certain period of time, the Endpoint Encryption agent
automatically locks the Endpoint Encryption device. Use the
tables below to understand the actions available for the account lockout and device
lock
actions.
The following table describes when the lockout actions occur:
|
Type
|
Description
|
|
Account lockout
|
Account lockout actions take effect when the Endpoint Encryption agent does not communicate with
PolicyServer for a certain period of time as set by the policy.
|
|
Full Disk Encryption device lockout
|
Full Disk Encryption device lockout actions take effect when the Endpoint Encryption user exceeds the number of
unsuccessful logon attempts to that Full Disk Encryption device as set by the
policy.
|
|
File Encryption device lockout
|
File Encryption device lockout actions take effect when the Endpoint Encryption user exceeds the number of
unsuccessful logon attempts to that File Encryption device as set by the
policy.
|
The options for lockout actions are as follows:
|
Action
|
Description
|
||
|
Erase
|
PolicyServer erases all data controlled by the associated Endpoint Encryption agent.
|
||
|
Remote authentication
|
PolicyServer locks the Endpoint Encryption device until the Endpoint Encryption user contacts receives Remote Help
authentication from an authenticator or from Support.
See Remote Help.
|
||
|
Time delay
|
PolicyServer temporarily locks the Endpoint Encryption device and notifies the Endpoint Encryption user that the device is locked. The ability to
authenticate or reset the password is disabled during the time delay. The duration
of the
time delay is determined by policy. Once the time delay has expired, the user is permitted
to authenticate.
|

