Flexibly manage Endpoint Encryption using only PolicyServer MMC or manage Endpoint Encryption using Control Manager for policy, user and device management and PolicyServer MMC for advanced log management and reporting.
The following illustration shows how to deploy Endpoint Encryption using Control Manager to manage PolicyServer. In a Control Manager deployment, administrators use Control Manager for all Endpoint Encryption policy, user, and device controls, and only use PolicyServer MMC for advanced Enterprise maintenance.
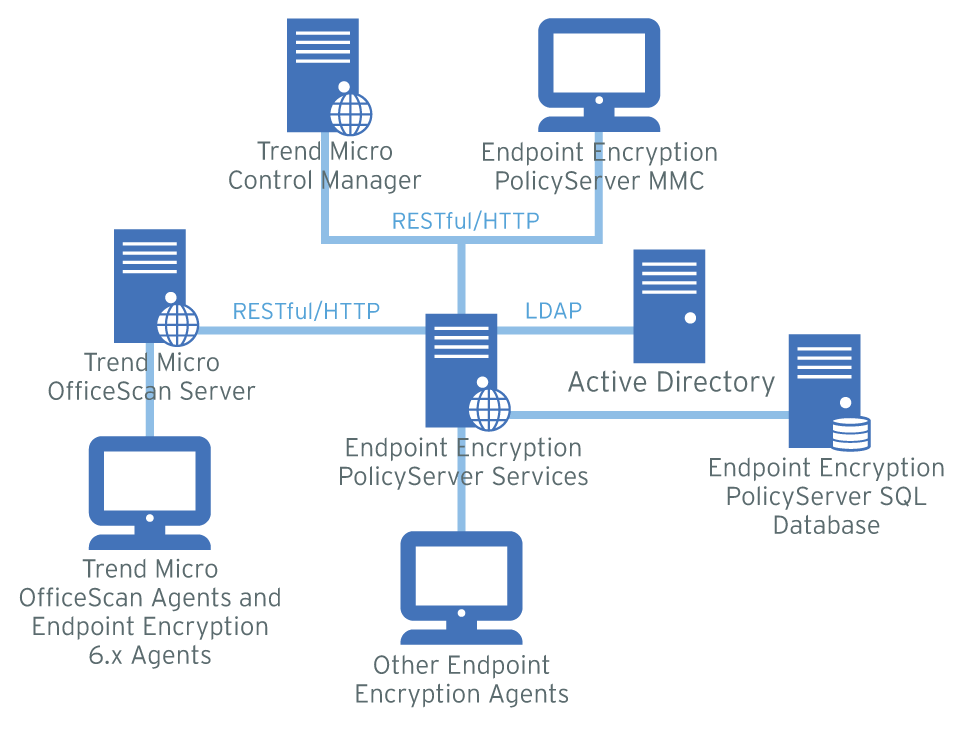
In environments that use Control Manager, changes to PolicyServer policies are always controlled by Control Manager. Any changes made using PolicyServer MMC are overwritten the next time that Control Manager synchronizes policies to the PolicyServer database.
Trend Micro Control Manager
Trend Micro™ Control Manager™ is a central management console that manages Trend Micro products and services at the gateway, mail server, file server, and corporate desktop levels. The Control Manager web-based management console provides a single monitoring point for managed products and services throughout the network.
Control Manager allows system administrators to monitor and report on activities such as infections, security violations, or virus entry points. System administrators can download and deploy components throughout the network, helping ensure that protection is consistent and up-to-date. Control Manager allows both manual and pre-scheduled updates, and the configuration and administration of products as groups or as individuals for added flexibility.
About PolicyServer MMC
The PolicyServer Microsoft Management Console plug-in (PolicyServer MMC) is the native management console for Endpoint Encryption policy, user, and device administration.
Use PolicyServer MMC to centrally manage:
-
All Endpoint Encryption users, devices, and groups
-
All policies including encryption, password complexity and authentication
-
Remote device actions, including killing a device, erasing data, or delaying authentication
-
Event logs about authentication events, management events, device encryption status, and security violations
-
Remote Help password reset process
-
Auditing and reporting options


