|
|
|
NoteFor information about the available user options in the policy, see Configuring Endpoint Encryption Users Rules.
|
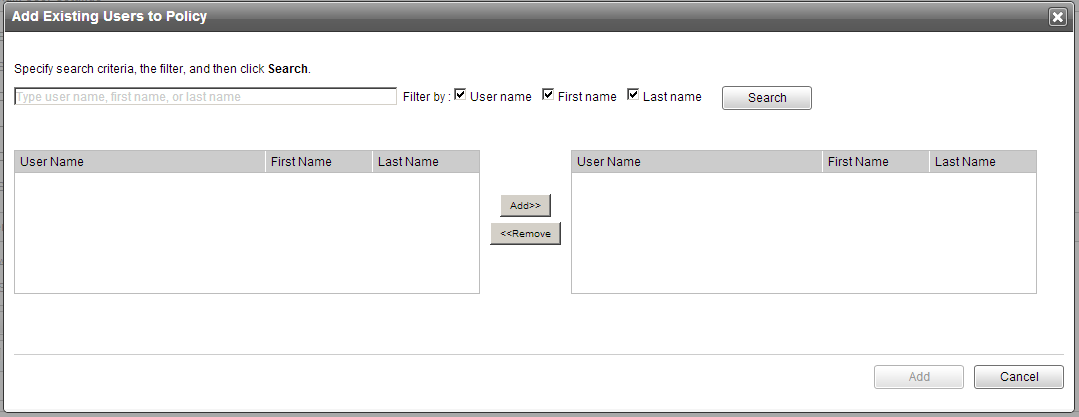
Note
|