

Trend Micro
These actions include instructing clients to update their OfficeScan client components, enable Real-time Scan, and perform Scan Now and Cleanup Now. It also includes the ability to display a notification message on client computers to inform users of the antivirus policy violation. To help you analyze the performance of your antivirus policies, you also have the option to view Policy Server logs, which record information such as the client validation time and the result of the evaluation.
The following list shows the various components and important terms used with Cisco NAC technology:
Cisco Trust Agent (CTA): A program installed on a client computer to allow it to communicate with other Cisco NAC components
OfficeScan client computer: A computer with the OfficeScan client program installed. To work with Cisco NAC, the client computer also requires the Cisco Trust Agent.
Network Access Device: A network device that supports Cisco NAC functionality. Supported Network Access Devices include a range of Cisco routers, firewall applications, and access points, as well as third-party devices configured with Terminal Access Controller Access Control System (TACACS+) or the Remote Dial-In User Service (RADIUS) protocol.
Supported platforms and requirements
|
Supported Platform |
Models |
IOS Images |
Minimum Memory/Flash |
|
Routers | |||
|
Cisco 830, 870 series |
831, 836, 837 |
IOS 12.3(8) or later |
48MB/8MB |
|
Cisco 1700 series |
1701, 1711, 1712, 1721, 1751, 1751-V, 1760 |
IOS 12.3(8) or later |
64MB/16MB |
|
Cisco 1800 series |
1841 |
IOS 12.3(8) or later |
128MB/32MB |
|
Cisco 2600 series |
2600XM, 2691 |
IOS 12.3(8) or later |
96MB/32MB |
|
Cisco 2800 series |
2801, 2811, 2821, 2851 |
IOS 12.3(8) or later |
128MB/64MB |
|
Cisco 3600 series |
3640/3640A, 3660-ENT series |
IOS 12.3(8) or later |
48MB/16MB |
|
Cisco 3700 series |
3745, 3725 |
IOS 12.3(8) or later |
128MB/32MB |
|
Cisco 3800 series |
3845, 3825 |
IOS 12.3(8) or later |
256MB/64MB |
|
Cisco 7200 series |
720x, 75xx |
IOS 12.3(8) or later |
128MB/48MB |
|
| |||
|
VPN Concentrators | |||
|
Cisco VPN 3000 Series |
3005 - 3080 |
V4.7 or later |
N/A |
|
| |||
|
Switches | |||
|
Cisco Catalyst 2900 |
2950, 2970 |
IOS 12.1(22)EA5 |
N/A |
|
Cisco Catalyst 3x00 |
3550, 3560, 3750 |
IOS 12.2(25)SEC |
N/A |
|
Cisco Catalyst 4x00 |
Supervisor 2+ or higher |
IOS 12.2(25)EWA |
N/A |
|
Cisco Catalyst 6500 |
6503, 6509, Supervisor 2 or higher |
CatOS 8.5 or later |
Sup2 - 128MB |
|
| |||
|
Wireless Access Points | |||
|
Cisco AP1200 Series |
1230 |
N/A |
N/A |
Cisco Secure Access Control Server (ACS): A server that receives OfficeScan client antivirus data from the client through the Network Access Device and passes it to an external user database for evaluation. Later in the process, the ACS server also passes the result of the evaluation, which may include instructions for the OfficeScan client, to the Network Access Device.
Policy Server: A program that receives and evaluates OfficeScan client antivirus data. After performing the evaluation, the Policy Server determines the actions the OfficeScan client should carry out and then notifies the client to perform the actions.
OfficeScan server: Reports the current Virus Pattern and Virus Scan Engine versions to the Policy Server, which uses this information to evaluate the OfficeScan client’s antivirus status.
Security posture: The presence and currency of antivirus software on a client. In this implementation, security posture refers to whether the OfficeScan client program exists on client computers, the status of certain OfficeScan client settings, and whether the Virus Scan Engine and Virus Pattern are up-to-date.
Posture token: Created by the Policy Server after OfficeScan client validation. It includes information that tells the OfficeScan client to perform a set of specified actions, such as enabling Real-time Scan or updating antivirus components.
Client validation: The process of evaluating client security posture and returning the posture token to the client
Policy Server rule: Guidelines containing configurable criteria the Policy Server uses to measure OfficeScan client security posture. A rule also contains actions for the client and the Policy Server to carry out if the security posture information matches the criteria.
Policy Server policy: A set of rules against which the Policy Server measures the security posture of OfficeScan clients. Policies also contain actions for clients and the Policy Server to carry out if the criteria in the rules associated with the policy do not match the security posture.
The figure below illustrates a basic Cisco NAC architecture with the components described above.
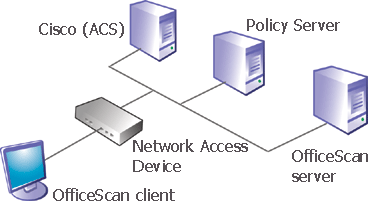
Client validation refers to the process of evaluating the OfficeScan client security posture and returning instructions for the client to perform if Policy Server considers it to be at-risk. The Policy Server validates an OfficeScan client by using configurable rules and policies.
In a separate process, the Policy Server periodically polls the OfficeScan server for Virus Pattern and Virus Scan Engine information to keep its security posture data current. It then uses a series of rules (contained in a policy) to perform a comparison of this information with the client security posture data it received from the ACS server. Following that, the Policy Server determines the value of a posture token, which passes back to the OfficeScan client through the ACS server and NAC client. Finally, the client performs the actions configured in the policies and rules upon itself. See Understanding rules and policies for more information on configuring Policy Server rules and policies.
Note: You can also configure the Cisco Secure ACS server to take actions on the OfficeScan client through the Network Access Device (for example, blocking the OfficeScan client from accessing the network). See your Cisco Secure ACS documentation for more information on ACS functionality and features.