![]()
![]()
dctrl
Device Control regulates access to external storage devices and network resources connected to computers. Device Control helps prevent data loss and leakage and, combined with file scanning, helps guard against security risks.
You can configure Device Control policies for internal and external clients. OfficeScan administrators typically configure a stricter policy for external clients.
Policies are granular settings in the OfficeScan client tree. You can enforce specific policies to client groups or individual clients. You can also enforce a single policy to all clients.
After you deploy the policies, clients use the location criteria you have set in the Computer Location screen (see Computer Location) to determine their location and the policy to apply. Clients switch policies each time the location changes.
Important:
Device Control only supports 32-bit platforms.
By default, Device Control is disabled on 32-bit versions of Windows Server 2003 and Windows Server 2008. Before enabling Device Control on these server platforms, read the guidelines and best practices outlined in Client Services.
The types of devices that OfficeScan can monitor depends on whether the Data Protection license is activated. Data Protection is a separately licensed module and must be activated before you can use it. For details about the Data Protection license, see Data Protection License.
|
Device Types |
|
Device Type |
Data Protection Activated |
Data Protection Not Activated |
|
Storage Devices |
||
|
CD/DVD |
Monitored |
Monitored |
|
Floppy disks |
Monitored |
Monitored |
|
Network drives |
Monitored |
Monitored |
|
USB storage devices |
Monitored |
Monitored |
|
Non-storage Devices |
||
|
COM and LPT ports |
Monitored |
Not monitored |
|
IEEE 1394 interface |
Monitored |
Not monitored |
|
Imaging devices |
Monitored |
Not monitored |
|
Infrared devices |
Monitored |
Not monitored |
|
Modems |
Monitored |
Not monitored |
|
PCMCIA card |
Monitored |
Not monitored |
|
Print screen key |
Monitored |
Not monitored |
For a list of supported device models, see:
http://docs.trendmicro.com/en-us/enterprise/officescan.aspx
Device Control permissions for storage devices are used when you:
Allow access to USB storage devices, CD/DVD, floppy disks, and network drives. You can grant full access to these devices or limit the level of access.
Configure the list of approved USB storage devices. Device Control allows you to block access to all USB storage devices, except those that have been added to the list of approved devices. You can grant full access to the approved devices or limit the level of access.
The following table lists the permissions:
|
Permissions |
Files on the Device |
Incoming Files |
|
Full access |
Permitted operations: |
Permitted operations: This means that a file can be saved, moved, and copied to the device. |
|
Modify |
Permitted operations: Prohibited operations: Execute |
Permitted operations: |
|
Read and execute |
Permitted operations: Prohibited operations: |
Prohibited operations: |
|
Read |
Permitted operations: Prohibited operations: |
Prohibited operations: |
|
List device content only |
Prohibited operations: The device and the files it contains are visible to the user (for example, from Windows Explorer). |
Prohibited operations: |
|
Block |
Prohibited operations: The device and the files it contains are not visible to the user (for example, from Windows Explorer). |
Prohibited operations: |
The file-based scanning function in OfficeScan complements and may override the device permissions. For example, if the permission allows a file to be opened but OfficeScan detects that the file is infected with malware, a specific scan action will be performed on the file to eliminate the malware. If the scan action is Clean, the file opens after it is cleaned. However, if the scan action is Delete, the file is deleted.
Advanced permissions apply when you grant limited permissions to storage devices. The permission can be any of the following:
Modify
Read and execute
Read
List device content only
You can keep the permissions limited but grant advanced permissions to certain programs on the storage devices and on the local computer.
To define programs, configure the following program lists:
|
Program Lists |
|
Program List |
Description |
Valid Inputs |
|
Programs with read and write access to storage devices |
This list contains local programs and programs on storage devices that have read and write access to the devices. An example of a local program is Microsoft Word (winword.exe), which is usually found in C:\Program Files\Microsoft Office\Office. If the permission for USB storage devices is "List device content only" but "C:\Program Files\Microsoft Office\Office\winword.exe" is included in this list:
|
Program path and name For details, see Specifying a Program Path and Name. |
|
Programs on storage devices that are allowed to execute |
This list contains programs on storage devices that users or the system can execute. For example, if you want to allow users to install software from a CD, add the installation program path and name, such as "E:\Installer\Setup.exe", to this list. |
Program path and name or Digital Signature Provider For details, see Specifying a Program Path and Name or Specifying a Digital Signature Provider. |
There are instances when you need to add a program to both lists. Consider the data lock feature in a USB storage device, which, if enabled, prompts users for a valid user name and password before the device can be unlocked. The data lock feature uses a program on the device called "Password.exe", which must be allowed to execute so that users can unlock the device successfully. "Password.exe" must also have read and write access to the device so that users can change the user name or password.
Each program list on the user interface can contain up to 100 programs. If you want to add more programs to a program list, you will need to add them to the ofcscan.ini file, which can accommodate up to 1,000 programs. For instructions on adding programs to the ofcscan.ini file, see To add programs to the Device Control program lists using the ofcscan.ini file:.
Programs added to the ofcscan.ini file will be deployed to the root domain and will overwrite programs on individual domains and clients.
Specifying a Digital Signature Provider
Specify a Digital Signature Provider if you trust programs issued by the provider. For example, type Microsoft Corporation or Trend Micro, Inc. You can obtain the Digital Signature Provider by checking the properties of a program (for example, by right-clicking the program and selecting Properties).
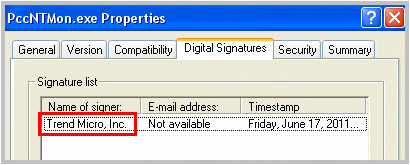
Digital Signature Provider for the OfficeScan client program (PccNTMon.exe)
Specifying a Program Path and Name
A program path and name should have a maximum of 259 characters and must only contain alphanumeric characters (A-Z, a-z, 0-9). It is not possible to specify only the program name.
You can use wildcards in place of drive letters and program names. Use a question mark (?) to represent single-character data, such as a drive letter. Use an asterisk (*) to represent multi-character data, such as a program name.
Wildcards cannot be used to represent folder names. The exact name of a folder must be specified.
Wildcards are used correctly in the following examples:
|
Correct Usage of Wildcards |
|
Example |
Matched Data |
|
?:\Password.exe |
The "Password.exe" file located directly under any drive |
|
C:\Program Files\Microsoft\*.exe |
Any .exe file in C:\Program Files\Microsoft |
|
C:\Program Files\*.* |
Any file in C:\Program Files that has a file extension |
|
C:\Program Files\a?c.exe |
Any .exe file in C:\Program Files that has 3 characters starting with the letter "a" and ending with the letter "c" |
|
C:\* |
Any file located directly under the C:\ drive, with or without file extensions |
Wildcards are used incorrectly in the following examples:
|
Incorrect Usage of Wildcards |
|
Example |
Reason |
|
??:\Buffalo\Password.exe |
?? represents two characters and drive letters only have a single alphabetic character. |
|
*:\Buffalo\Password.exe |
* represents multi-character data and drive letters only have a single alphabetic character. |
|
C:\*\Password.exe |
Wildcards cannot be used to represent folder names. The exact name of a folder must be specified. |
|
C:\?\Password.exe |
You can allow or block access to non-storage devices. There are no granular or advanced permissions for these devices.
To manage access to external devices (Data Protection activated):
Networked Computers > Client Management
In the client tree, click the root domain icon ![]() to include all clients or select specific
domains or clients.
to include all clients or select specific
domains or clients.
Click Settings > Device Control Settings.
Click the External Clients tab to configure settings for external clients or the Internal Clients tab to configure settings for internal clients.
Select Enable Device Control.
If you are on the External Clients tab, you can apply settings to internal clients by selecting Apply all settings to internal clients.
If you are on the Internal Clients tab, you can apply settings to external clients by selecting Apply all settings to external clients.
Choose to allow or block the AutoRun function (autorun.inf) on USB storage devices.
Configure settings for storage devices.
Select a permission for each storage device. For details about permissions, see Permissions for Storage Devices.
Configure advanced permissions and notifications if the permission for a storage device is any of the following:
Modify
Read and execute
Read
List device content only
Although you can configure advanced permissions and notifications for a specific storage device on the user interface, the permissions and notifications are actually applied to all storage devices. This means that when you click Advanced permissions and notifications for CD/DVD, you are actually defining permissions and notifications for all storage devices.
For details about advanced permissions and how to correctly define programs with advanced permissions, see Advanced Permissions for Storage Devices.
Click Advanced permissions and notifications. A new screen opens.
Below Programs with read and write access to storage devices, type a program path and file name and then click Add. Digital Signature Provider is not accepted.
Below Programs on storage devices that are allowed to execute, type the program path and name or the Digital Signature Provider and then click Add.
Select Display a notification message on the client computer when OfficeScan detects unauthorized device access.
Unauthorized device access refers to prohibited device operations. For example, if the device permission is "Read", users will not be able to save, move, delete, or execute a file on the device. For a list of prohibited device operations based on permissions, see Permissions for Storage Devices.
You can modify the notification message. For details, see Device Control Notifications.
Click Back.
If the permission for USB storage devices is Block, configure a list of approved devices. Users can access these devices and you can control the level of access using permissions.
Click Approved devices.
Type the device vendor.
Type the device model and serial ID.
Use the Device List Tool to query devices connected to endpoints. The tool provides the device vendor, model, and serial ID for each device. For details, see Device List Tool.
Select the permission for the device. For details about permissions, see Permissions for Storage Devices.
To add more devices, click the ![]() icon.
icon.
Click Back.
For each non-storage device, select Allow or Block.
If you selected domain(s) or client(s) in the client tree, click Save. If you clicked the root domain icon, choose from the following options:
Apply to All Clients: Applies settings to all existing clients and to any new client added to an existing/future domain. Future domains are domains not yet created at the time you configured the settings.
Apply to Future Domains Only: Applies settings only to clients added to future domains. This option will not apply settings to new clients added to an existing domain.
To manage access to external devices (Data Protection not activated):
Networked Computers > Client Management
In the client tree, click the root domain icon ![]() to include all clients or select specific
domains or clients.
to include all clients or select specific
domains or clients.
Click Settings > Device Control. Settings.
Click the External Clients tab to configure settings for external clients or the Internal Clients tab to configure settings for internal clients.
Select Enable Device Control.
If you are on the External Clients tab, you can apply settings to internal clients by selecting Apply all settings to internal clients.
If you are on the Internal Clients tab, you can apply settings to external clients by selecting Apply all settings to external clients.
Choose to allow or block the AutoRun function (autorun.inf) on USB storage devices.
Select the permission for each device. For details about permissions, see Permissions for Storage Devices.
Configure advanced permissions and notifications if the permission for a device is any of the following:
Modify
Read and execute
Read
List device content only
There is no need to configure advanced permissions and notifications if the permission for all devices is Full Access.
For details about advanced permissions and how to correctly define programs with advanced permissions, see Advanced Permissions for Storage Devices.
Below Programs with read and write access to storage devices, type a program path and file name and then click Add. Digital Signature Provider is not accepted.
Below Programs on storage devices that are allowed to execute, type the program path and name or the Digital Signature Provider and then click Add.
Select Display a notification message on the client computer when OfficeScan detects unauthorized device access.
Unauthorized device access refers to prohibited device operations. For example, if the device permission is "Read", users will not be able to save, move, delete, or execute a file on the device. For a list of prohibited device operations based on permissions, see Permissions for Storage Devices.
You can modify the notification message. For details, see Device Control Notifications.
If you selected domain(s) or client(s) in the client tree, click Save. If you clicked the root domain icon, choose from the following options:
Apply to All Clients: Applies settings to all existing clients and to any new client added to an existing/future domain. Future domains are domains not yet created at the time you configured the settings.
Apply to Future Domains Only: Applies settings only to clients added to future domains. This option will not apply settings to new clients added to an existing domain.
To add programs to the Device Control program lists using the ofcscan.ini file:
For details about program lists and how to correctly define programs that can be added to the lists, see Advanced Permissions for Storage Devices.
On the OfficeScan server computer, navigate to < Server installation folder >\PCCSRV.
Open ofcscan.ini using a text editor.
To add programs with read and write access to storage devices:
Locate the following lines:
[DAC_APPROVED_LIST]
Count=x
Replace "x" with the number of programs in the program list.
Below "Count=x", add programs by typing the following:
Item<number>=<program path and name or Digital Signature Provider>
For example:
[DAC_APPROVED_LIST]
Count=3
Item0=C:\Program Files\program.exe
Item1=?:\password.exe
Item2=Microsoft Corporation
To add programs on storage devices that are allowed to execute:
Locate the following lines:
[DAC_EXECUTABLE_LIST]
Count=x
Replace "x" with the number of programs in the program list.
Below "Count=x", add programs by typing the following:
Item<number>=<program path and name or Digital Signature Provider>
For example:
[DAC_EXECUTABLE_LIST]
Count=3
Item0=?:\Installer\Setup.exe
Item1=E:\*.exe
Item2=Trend Micro, Inc.
Save and close the ofcscan.ini file.
Open the OfficeScan web console and go to Networked Computers > Global Client Settings.
Click Save to deploy the program lists to all clients.
See also: