An organization must design a strategy that provides optimal protection for its Lync
Server
environment. Consider the following when selecting your IM Security protection strategy:
-
What is the overall corporate IT security strategy?
-
What are the available resources (processor, memory) on servers with Lync?
-
Where and how can security risks and unwanted content enter the Lync Server environment
(for
example, file transfer, instant message)?
Trend Micro recommends the following strategies
for optimal protection for a Lync server environment:
-
Implement a virus/malware and spyware/grayware scanning regimen
-
Create File Blocking rules for unauthorized file types and extensions
 |
Note
The IM Security product console
provides the recommended file types and extensions to block.
|
-
Create Content Filtering rules for unwanted or offensive keywords in instant messages
and
file transfers
-
Create Data Loss Prevention rules for sensitive data in instant messages and file
transfers
-
Configure scheduled component updates
These strategies provide excellent protection, while also minimizing the system resource
usage.
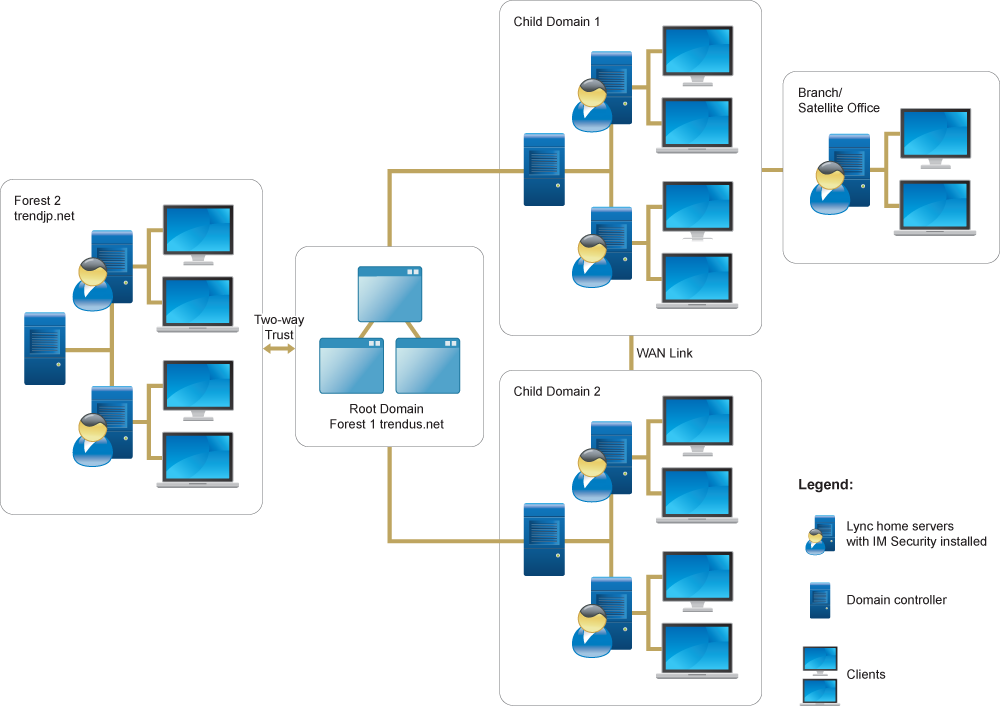
A sample protected Lync environment