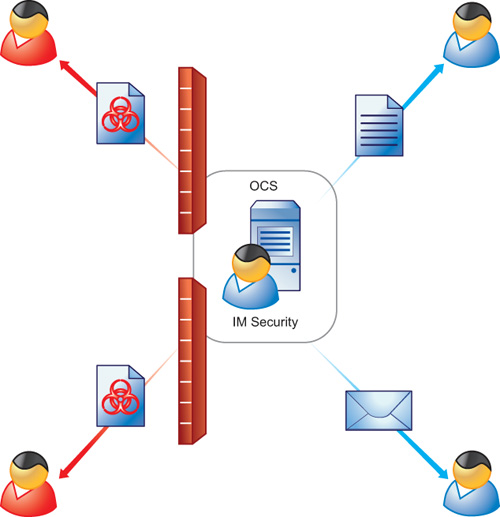
Instant messaging can mean instant exposure to fast-moving attacks designed to spread
malware,
lure victims to malicious sites, and steal data. Trend
Micro™
IM Security for Microsoft™
Lync™ Server secures your real-time IM communications by stopping the wide
range of threats—faster than ever. In-the-cloud Web Reputation blocks links to malicious
sites
before the links can be delivered. Signature-independent zero-day security, leading
antivirus,
and antispyware work together to stop malware before any damage can occur. Plus, flexible
Content
Filtering and Data Loss Protection features ensure appropriate IM use and prevent
data theft.
IM Security incorporates virus/malware and
spyware/grayware scanning, Content Filtering, URL filtering, File Blocking, Data Loss
Prevention,
and Communication Control into one cohesive solution.