|
|
|
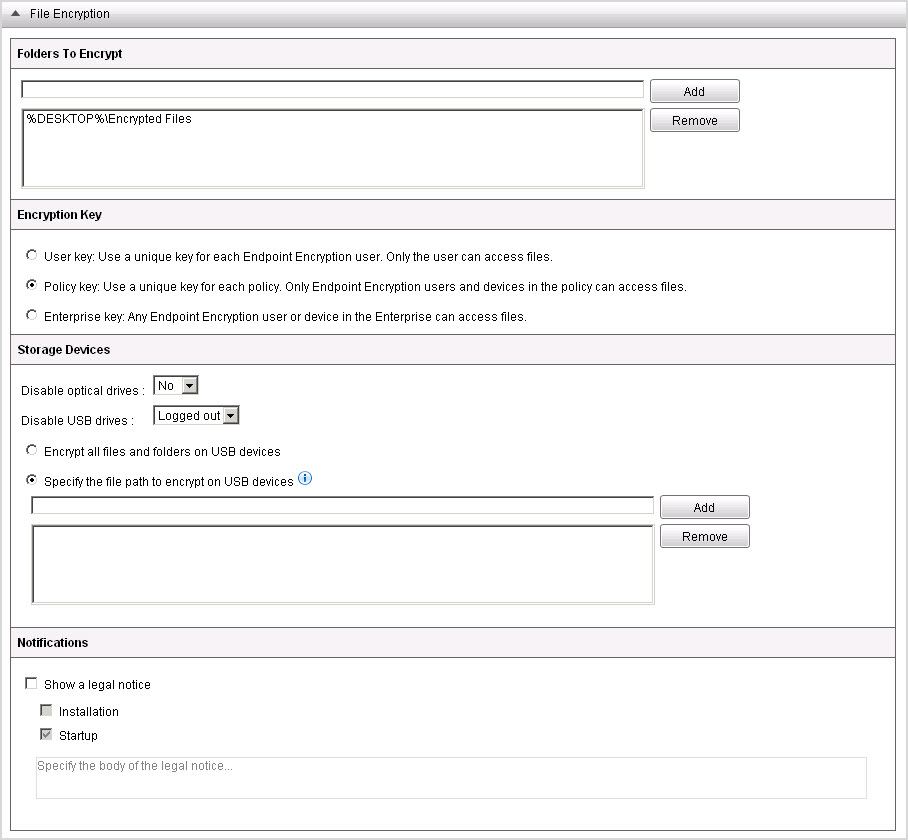
NoteSelecting Policy key or Enterprise
key controls the sharing for the File Encryption shared key. For more information,
see File Encryption Shared Key Encryption.
|