|
|
|
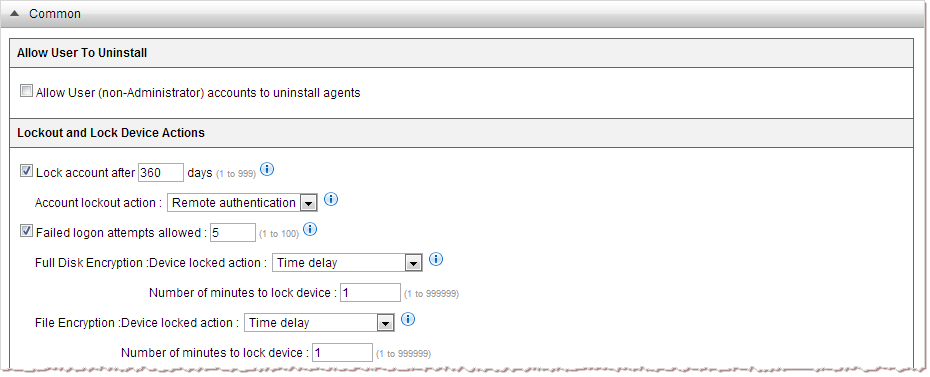
NoteBy default, only Enterprise Administrator accounts can uninstall Endpoint Encryption agents.
|
NoteFor information about lock options, see Account Lockout and Device Lock Actions
|
Remote Authenticationor the
Eraseaction occurs at lockout.
NoteFor information about lock options, see Account Lockout and Device Lock Actions
|
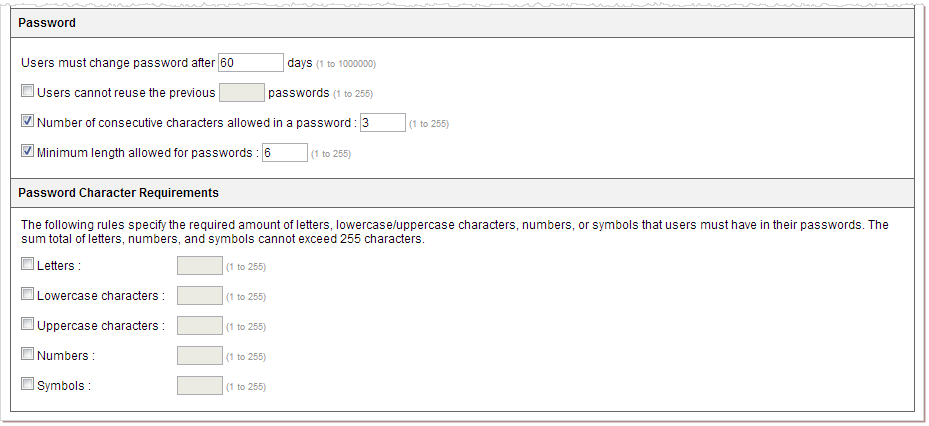
ImportantThe sum total of letters, numbers, and symbols cannot exceed 255
characters.
|