Once a piece of malicious software runs, it may
immediately initiate communication to a command-and-control (C&C) server for further
instructions or lie dormant on a system for hours in an attempt to remain hidden.
One of two
things usually happens when the software accesses the C&C server. First, the software
may
automatically download and install additional malware. This type of malware is called
a
downloader
. Second, the software can communicate back to the C&C server. A human
monitoring the C&C server (attacker) would then notice the new connection and initiate
some
sort of action. This type of software, called a
remote access Trojan
(RAT), gives an
attacker the ability to examine a system, extract files, download new files to run
on a
compromised system, turn on a system’s video camera and microphone, take screen captures,
capture
keystrokes, and run a command shell.
The C&C Contact Alert widget shows all attempts by compromised hosts
to connect to C&C servers. When Deep Edge detects a
C&C callback attempt, the traffic is controlled based on the policy action configuration.
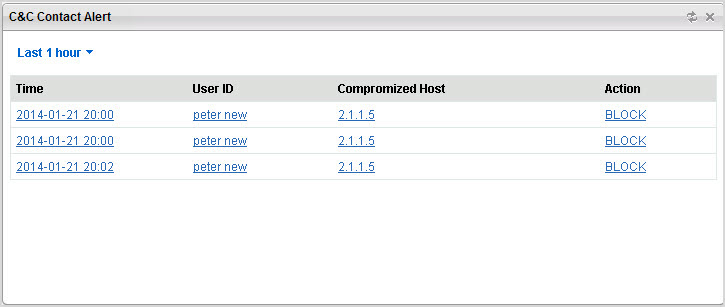
The time period displays information about today, last 1 hour, last 12
hours, last 24 hours, last 7 days.
To manually refresh the data, click the  icon in the upper
right corner of the widget.
icon in the upper
right corner of the widget. The
widget automatically refreshes data every minute.
