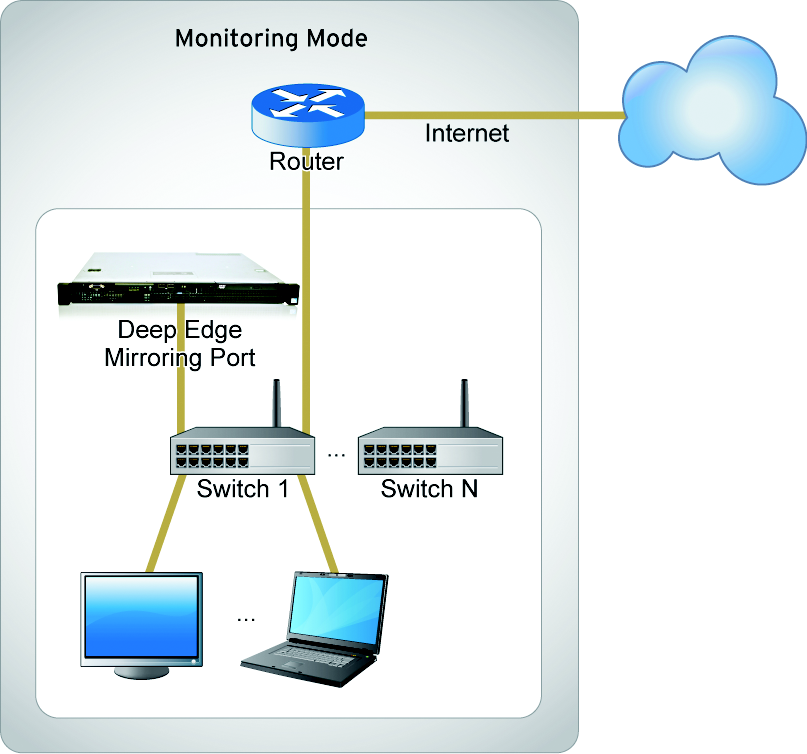
Monitoring mode
is designed for evaluating
Deep Edge on a
production network without blocking any traffic or making
Deep Edge a point of failure in the network flow. In Monitoring mode,
Deep Edge is invisible to the network. Establish the
correct monitoring settings on the network switch to mirror traffic to the port that
connects to
Deep Edge.
Deep Edge will apply policies to the mirrored traffic,
but only logs violation-related information. Network traffic is never blocked by policies
in this
mode.
Deep Edge in Monitoring mode illustrates
Deep Edge in Monitoring mode:
Deep Edge in Monitoring mode
In Monitoring mode, network traffic does not pass directly through Deep Edge. Deep Edge runs independently outside the network (logically) aided by the switches
of the network which mirror the specified traffic to interface(s) on which Deep Edge listens. Deep Edge monitors the status of the traffic and
presents the information to the Deep Edge
user.
Trend Micro suggests Deep Edge be deployed at
the core Internet switch in order to see a copy of all Internet traffic leaving and
entering the
network. Deep Edge requires at least two
network interfaces to function correctly in Monitoring mode. In addition to the interface
that
Deep Edge uses to listen for traffic, there
should be another connection for Deep Edge to
access the Internet to connect to the ActiveUpdate and WRS query servers, as well
as other cloud
protection sources that Deep Edge offers.
Monitoring mode is typically used when:
- The network already has related devices (firewall, IDS, etc.) deployed, but there
is a lack
of visibility into the overall network posture. In this case, Deep Edge provides visibility without dramatically
changing the network topology.
- Before deploying Deep Edge inline,
Monitoring mode could help with the evaluation of the Deep Edge device. After learning the security benefits provided by Deep Edge, administrators could change from Monitoring
mode to either Bridge mode or Router mode for true inline protection.