|
|
|
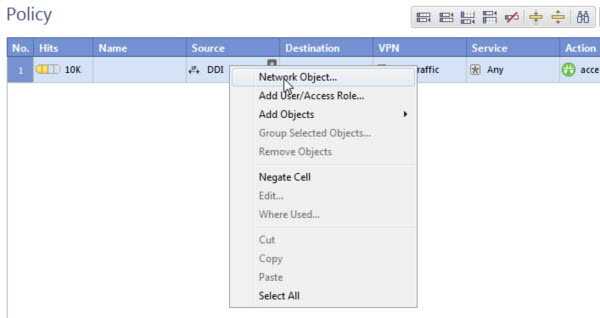
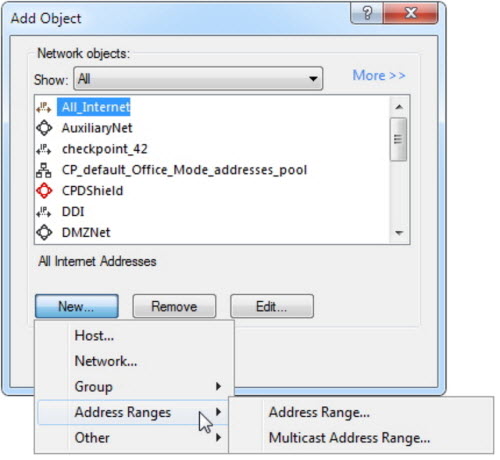
NoteEnsure that your network configuration allows TippingPoint Advanced
Threat Protection for Email to
connect to the Check Point appliance.
TippingPoint Advanced
Threat Protection for Email may connect to the Check Point appliance through
the secured connection port or clear connection port that is configured
on the Check Point appliance. TippingPoint Advanced
Threat Protection for Email also
pulls the certificate from the Check Point appliance through port
18210.
|
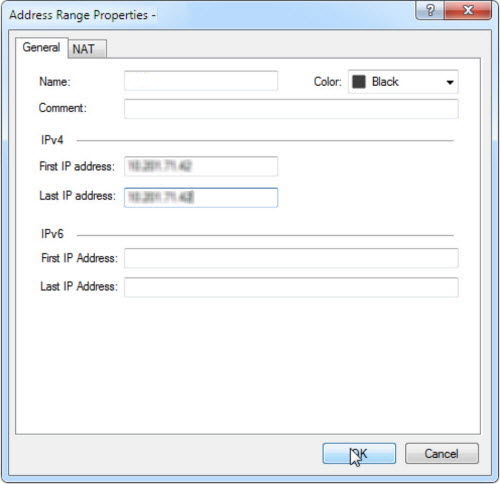
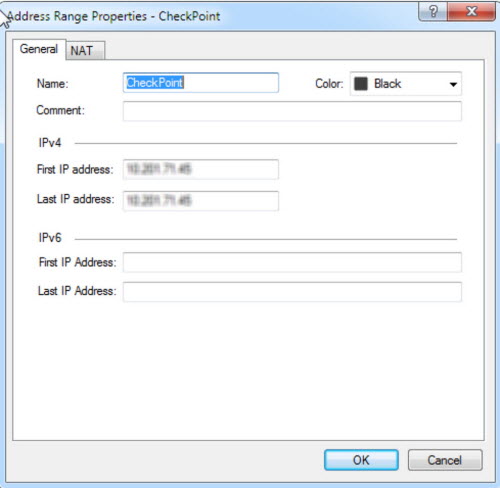
NoteThe server name must be the IPv4 address of
the auxiliary product.
|
NoteIf the one-time password is reset on the Check Point
appliance, the new one-time password must be different than the previous
one-time password.
|
NoteThis port must be the same port that is configured on
the security gateway. For details, see Preconfiguring a Security Gateway.
|